
Master the 156-215.80 Check Point Certified Security Administrator content and be ready for exam day success quickly with this Passleader 156-215.80 real exam. We guarantee it!We make it a reality and give you real 156-215.80 questions in our Check-Point 156-215.80 braindumps.Latest 100% VALID Check-Point 156-215.80 Exam Questions Dumps at below page. You can use our Check-Point 156-215.80 braindumps and pass your exam.
Free 156-215.80 Demo Online For Check-Point Certifitcation:
NEW QUESTION 1
How do you configure the Security Policy to provide uses access to the Captive Portal through an external (Internet) interface?
Answer: A
NEW QUESTION 2
Which of the following is NOT an element of VPN Simplified Mode and VPN Communities?
Answer: A
Explanation:
Migrating from Traditional Mode to Simplified Mode
To migrate from Traditional Mode VPN to Simplified Mode:
1. On the Global Properties > VPN page, select one of these options:
• Simplified mode to all new Firewall Policies
• Traditional or Simplified per new Firewall Policy
2. Click OK.
3. From the R80 SmartConsole Menu, select Manage policies. The Manage Policies window opens.
4. Click New.
The New Policy window opens.
5. Give a name to the new policy and select Access Control.
In the Security Policy Rule Base, a new column marked VPN shows and the Encrypt option is no longer available in the Action column. You are now working in Simplified Mode.
NEW QUESTION 3
Which rule is responsible for the user authentication failure?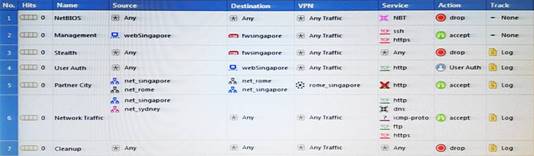
Answer: C
NEW QUESTION 4
What is the difference between SSL VPN and IPSec VPN?
Answer: D
NEW QUESTION 5
You can see the following graphic: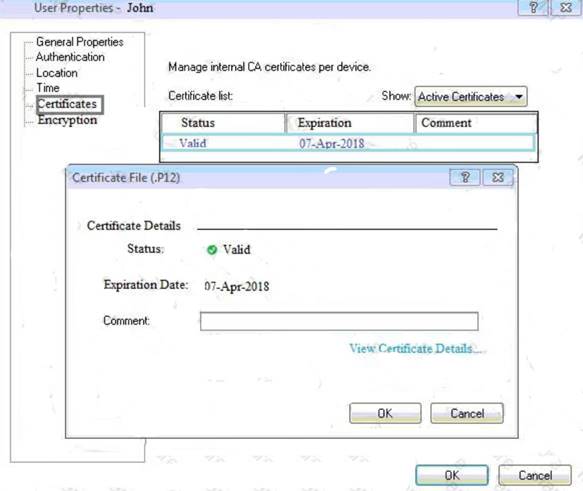
What is presented on it?
Answer: A
NEW QUESTION 6
In the Check Point three-tiered architecture, which of the following is NOT a function of the Security Management Server (Security Management Server)?
Answer: A
NEW QUESTION 7
Which option would allow you to make a backup copy of the OS and Check Point configuration, without stopping Check Point processes?
Answer: D
NEW QUESTION 8
Which of the following statements is TRUE about R80 management plug-ins?
Answer: C
NEW QUESTION 9
Which VPN routing option uses VPN routing for every connection a satellite gateway handles?
Answer: D
Explanation:
On the VPN Routing page, enable the VPN routing for satellites section, by selecting one of these options:
To center and to other Satellites through center; this allows connectivity between Gateways; for example, if the spoke Gateways are DAIP Gateways, and the hub is a Gateway with a static IP address
To center, or through the center to other satellites, to Internet and other VPN targets; this allows connectivity between the Gateways, as well as the ability to inspect all communication passing through the hub to the Internet.
NEW QUESTION 10
Which path below is available only when CoreXL is enabled?
Answer: C
NEW QUESTION 11
Which type of Endpoint Identity Agent includes packet tagging and computer authentication?
Answer: A
Explanation:
Endpoint Identity Agents – dedicated client agents installed on users’ computers that acquire and report identities to the Security Gateway.
NEW QUESTION 12
Which identity Source(s) should be selected in Identity Awareness for when there is a requirement for a higher level of security for sensitive servers?
Answer: D
NEW QUESTION 13
Where would an administrator enable Implied Rules logging?
Answer: B
NEW QUESTION 14
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his desktop with a static IP (10.0.0.19). He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
3) Changes from static IP address to DHCP for the client PC.
What should John request when he cannot access the web server from his laptop?
Answer: C
NEW QUESTION 15
Fill in the blank: To build an effective Security Policy, use a _____ and _____ rule.
Answer: A
NEW QUESTION 16
Sally has a Hot Fix Accumulator (HFA) she wants to install on her Security Gateway which operates with GAiA, but she cannot SCP the HFA to the system. She can SSH into the Security Gateway, but she has never been able to SCP files to it. What would be the most likely reason she cannot do so?
Answer: C
NEW QUESTION 17
Fill in the blank: Authentication rules are defined for ____ .
Answer: A
NEW QUESTION 18
Fill in the blank: The _____ feature allows administrators to share a policy with other policy packages.
Answer: A
NEW QUESTION 19
What happens if the identity of a user is known?
Answer: D
NEW QUESTION 20
What is the main difference between Threat Extraction and Threat Emulation?
Answer: B
NEW QUESTION 21
What are the three tabs available in SmartView Tracker?
Answer: C
NEW QUESTION 22
You are unable to login to SmartDashboard. You log into the management server and run #cpwd_admin list with the following output: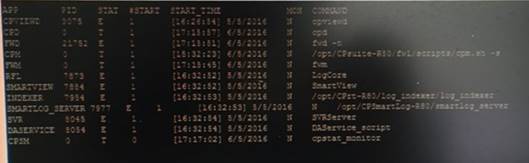
What reason could possibly BEST explain why you are unable to connect to SmartDashboard?
Answer: C
Explanation:
The correct answer would be FWM (is the process making available communication between SmartConsole applications and Security Management Server.). STATE is T (Terminate = Down)
Symptoms
SmartDashboard fails to connect to the Security Management server.
Verify if the FWM process is running. To do this, run the command:
[Expert@HostName:0]# ps -aux | grep fwm
If the FWM process is not running, then try force-starting the process with the following command: [Expert@HostName:0]# cpwd_admin start -name FWM -path "$FWDIR/bin/fwm" -command "fwm" [Expert@HostName:0]# ps -aux | grep fwm
[Expert@HostName:0]# cpwd_admin start -name FWM -path "$FWDIR/bin/fwm" -command "fwm"
NEW QUESTION 23
What is the SOLR database for?
Answer: A
NEW QUESTION 24
What happens if the identity of a user is known?
Answer: C
NEW QUESTION 25
Your boss wants you to closely monitor an employee suspected of transferring company secrets to the competition. The IT department discovered the suspect installed a WinSCP client in order to use encrypted
communication. Which of the following methods is BEST to accomplish this task?
Answer: A
NEW QUESTION 26
Mesh and Star are two types of VPN topologies. Which statement below is TRUE about these types of communities?
Answer: D
NEW QUESTION 27
What are the three essential components of the Check Point Security Management Architecture?
Answer: A
Explanation:
Standalone deployment - Security Gateway and the Security Management server are installed on the same machine.
Distributed deployment - Security Gateway and the Security Management server are installed on different machines.
Deployments
Basic deployments: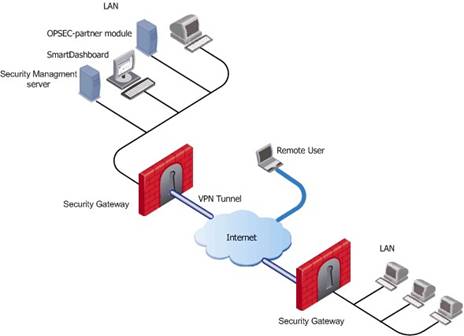
Assume an environment with gateways on different sites. Each Security Gateway connects to the Internet on one side, and to a LAN on the other.
You can create a Virtual Private Network (VPN) between the two Security Gateways, to secure all communication between them.
The Security Management server is installed in the LAN, and is protected by a Security Gateway. The Security Management server manages the Security Gateways and lets remote users connect securely to the corporate network. SmartDashboard can be installed on the Security Management server or another computer.
There can be other OPSEC-partner modules (for example, an Anti-Virus Server) to complete the network security with the Security Management server and its Security Gateways.
NEW QUESTION 28
You find a suspicious connection from a problematic host. You decide that you want to block everything from that whole network, not just the problematic host. You want to block this for an hour while you investigate further, but you do not want to add any rules to the Rule Base. How do you achieve this?
Answer: C
NEW QUESTION 29
Which options are given on features, when editing a Role on Gaia Platform?
Answer: B
Explanation:
Roles
Role-based administration (RBA) lets you create administrative roles for users. With RBA, an administrator can allow Gaia users to access specified features by including those features in a role and assigning that role to users. Each role can include a combination of administrative (read/write) access to some features, monitoring (readonly) access to other features, and no access to other features.
You can also specify which access mechanisms (WebUI or the CLI) are available to the user.
Note - When users log in to the WebUI, they see only those features that they have read-only or read/write access to. If they have read-only access to a feature, they can see the settings pages, but cannot change the settings.
Gaia includes these predefined roles:
You cannot delete or change the predefined roles.
Note - Do not define a new user for external users. An external user is one that is defined on an authentication server (such as RADIUS or TACACS) and not on the local Gaia system.
NEW QUESTION 30
Which type of Check Point license is tied to the IP address of a specific Security Gateway and cannot be transferred to a gateway that has a different IP address?
Answer: D
NEW QUESTION 31
......
P.S. Certleader now are offering 100% pass ensure 156-215.80 dumps! All 156-215.80 exam questions have been updated with correct answers: https://www.certleader.com/156-215.80-dumps.html (485 New Questions)