
Accurate of 156-215.80 testing engine materials and free practice test for Check-Point certification for consumer, Real Success Guaranteed with Updated 156-215.80 pdf dumps vce Materials. 100% PASS Check Point Certified Security Administrator exam Today!
Check 156-215.80 free dumps before getting the full version:
NEW QUESTION 1
The IT Management team is interested in the new features of the Check Point R80 Management and wants to upgrade but they are concerned that the existing R77.30 Gaia Gateways cannot be managed by R80 because it is so different. As the administrator responsible for the Firewalls, how can you answer or confirm these concerns?
Answer: A
NEW QUESTION 2
If there are two administrators logged in at the same time to the SmartConsole, and there are objects locked for editing, what must be done to make them available to other administrators? Choose the BEST answer.
Answer: A
Explanation:
To make changes available to all administrators, and to unlock the objects and rules that are being edited, the administrator must publish the session.
To make your changes available to other administrators, and to save the database before installing a policy, you must publish the session. When you publish a session, a new database version is created.
When you select Install Policy, you are prompted to publish all unpublished changes. You cannot install a policy if the included changes are not published.
NEW QUESTION 3
Using ClusterXL, what statement is true about the Sticky Decision Function?
Answer: A
NEW QUESTION 4
What are types of Check Point APIs available currently as part of R80.10 code?
Answer: B
NEW QUESTION 5
Which of the following is NOT an alert option?
Answer: B
Explanation:
In Action, select:
none - No alert.
log - Sends a log entry to the database.
alert - Opens a pop-up window to your desktop.
mail - Sends a mail alert to your Inbox.
snmptrap - Sends an SNMP alert.
useralert - Runs a script. Make sure a user-defined action is available. Go to SmartDashboard > Global Properties > Log and Alert > Alert Commands.
NEW QUESTION 6
Provide very wide coverage for all products and protocols, with noticeable performance impact.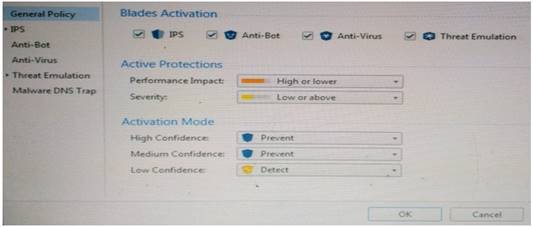
How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
Answer: B
NEW QUESTION 7
Joey is using the computer with IP address 192.168.20.13. He wants to access web page “www.Check Point.com”, which is hosted on Web server with IP address 203.0.113.111. How many rules on Check Point Firewall are required for this connection?
Answer: D
NEW QUESTION 8
Which one of the following is the preferred licensing model? Select the Best answer.
Answer: B
Explanation:
Central License
A Central License is a license attached to the Security Management server IP address, rather than the gatewa IP address. The benefits of a Central License are:
Only one IP address is needed for all licenses.
A license can be taken from one gateway and given to another.
The new license remains valid when changing the gateway IP address. There is no need to create and install a new license.
NEW QUESTION 9
During the Check Point Stateful Inspection Process, for packets that do not pass Firewall Kernel Inspection and are rejected by the rule definition, packets are:
Answer: D
NEW QUESTION 10
Which of the following commands is used to monitor cluster members?
Answer: A
NEW QUESTION 11
How would you determine the software version from the CLI?
Answer: A
NEW QUESTION 12
What port is used for delivering logs from the gateway to the management server?
Answer: C
NEW QUESTION 13
Message digests use which of the following?
Answer: D
NEW QUESTION 14
Check Point APIs allow system engineers and developers to make changes to their organization’s security policy with CLI tools and Web Services for all of the following except:
Answer: A
NEW QUESTION 15
Fill in the blank: Each cluster has _____ interfaces.
Answer: C
Explanation:
Each cluster member has three interfaces: one external interface, one internal interface, and one for synchronization. Cluster member interfaces facing in each direction are connected via a switch, router, or VLAN switch.
NEW QUESTION 16
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ____ .
Answer: B
Explanation:
To enable Identity Awareness:
Log in to SmartDashboard.
From the Network Objects tree, expand the Check Point branch.
Double-click the Security Gateway on which to enable Identity Awareness.
In the Software Blades section, select Identity Awareness on the Network Security tab.
The Identity Awareness
Configuration wizard opens.
Select one or more options. These options set the methods for acquiring identities of managed and unmanaged assets.
AD Query - Lets the Security Gateway seamlessly identify Active Directory users and computers
Browser-Based Authentication - Sends users to a Web page to acquire identities from unidentified users. If Transparent Kerberos Authentication is configured, AD users may be identified transparently.
NEW QUESTION 17
Mesh and Star are two types of VPN topologies. Which statement below is TRUE about these types of communities?
Answer: D
NEW QUESTION 18
Choose the Best place to find a Security Management Server backup file named backup_fw, on a Check Point Appliance.
Answer: D
Explanation:
Gaia's Backup feature allows backing up the configuration of the Gaia OS and of the Security Management server database, or restoring a previously saved configuration. The configuration is saved to a .tgz file in the following directory:
Gaia OS Version Hardware
Local Directory R75.40 - R77.20
Check Point appliances
/var/log/CPbackup/backups/ Open Server
/var/CPbackup/backups/ R77.30
Check Point appliances
/var/log/CPbackup/backups/ Open Server
NEW QUESTION 19
In order to modify Security Policies the administrator can use which of the following tools? Select the BEST answer.
Answer: D
NEW QUESTION 20
Which of the following are types of VPN communicates?
Answer: D
NEW QUESTION 21
......
Recommend!! Get the Full 156-215.80 dumps in VCE and PDF From Downloadfreepdf.net, Welcome to Download: https://www.downloadfreepdf.net/156-215.80-pdf-download.html (New 485 Q&As Version)