
Ucertify offers free demo for 156-215.80 exam. "Check Point Certified Security Administrator", also known as 156-215.80 exam, is a Check-Point Certification. This set of posts, Passing the Check-Point 156-215.80 exam, will help you answer those questions. The 156-215.80 Questions & Answers covers all the knowledge points of the real exam. 100% real Check-Point 156-215.80 exams and revised by experts!
Free 156-215.80 Demo Online For Check-Point Certifitcation:
NEW QUESTION 1
The most important part of a site-to-site VPN deployment is the ____.
Answer: C
Explanation:
Site to Site VPN
The basis of Site to Site VPN is the encrypted VPN tunnel. Two Security Gateways negotiate a link and create a VPN tunnel and each tunnel can contain more than one VPN connection. One Security Gateway can maintain more than one VPN tunnel at the same time.
NEW QUESTION 2
Which of the following is NOT a VPN routing option available in a star community?
Answer: A
Explanation:
SmartConsole
For simple hubs and spokes (or if there is only one Hub), the easiest way is to configure a VPN star community in R80 SmartConsole:
On the Star Communitywindow, in the:
Center Gateways section, select the Security Gateway that functions as the "Hub".
Satellite Gateways section, select Security Gateways as the "spokes", or satellites.
On the VPN Routing page, Enable VPN routing for satellites section, select one of these options:
To center and to other Satellites through center - This allows connectivity between the Security Gateways, for example if the spoke Security Gateways are DAIP Security Gateways, and the Hub is a Security Gateway with a static IP address.
To center, or through the center to other satellites, to internet and other VPN targets - This allows connectivity between the Security Gateways as well as the ability to inspect all communication passing through the Hub to the Internet.
Create an appropriate Access Control Policy rule.
NAT the satellite Security Gateways on the Hub if the Hub is used to route connections from Satellites to the Internet.
The two Dynamic Objects (DAIP Security Gateways) can securely route communication through the Security Gateway with the static IP address.
NEW QUESTION 3
A digital signature:
Answer: A
NEW QUESTION 4
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, gateway policy permits access only from Join's desktop which is assigned an IP address 10.0.0.19 via DHCP.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but the limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop. He wants to move around the organization and continue to have access to the HR Web Server. To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
John plugged in his laptop to the network on a different network segment and he is not able to connect. How does he solve this problem?
Answer: C
NEW QUESTION 5
You want to store the GAiA configuration in a file for later reference. What command should you use?
Answer: D
NEW QUESTION 6
The WebUI offers three methods for downloading Hotfixes via CPUSE. One of them is Automatic method. How many times per day will CPUSE agent check for hotfixes and automatically download them?
Answer: D
NEW QUESTION 7
You are about to integrate RSA SecurID users into the Check Point infrastructure. What kind of users are to be defined via SmartDashboard?
Answer: A
NEW QUESTION 8
What does ExternalZone represent in the presented rule?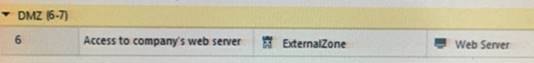
Answer: B
Explanation:
Configuring Interfaces
Configure the Security Gateway 80 interfaces in the Interfaces tab in the Security Gateway window. To configure the interfaces:
From the Devices window, double-click the Security Gateway 80.
The Security Gateway
window opens.
Select the Interfaces tab.
Select Use the following settings. The interface settings open.
Select the interface and click Edit.
The Edit window opens.
From the IP Assignment section, configure the IP address of the interface:
Select Static IP.
Enter the IP address and subnet mask for the interface.
In Security Zone, select Wireless, DMS, External, or Internal. Security zone is a type of zone, created by a bridge to easily create segments, while maintaining IP addresses and router configurations. Security zones let you choose if to enable or not the firewall between segments.
References:
NEW QUESTION 9
Where would an administrator enable Implied Rules logging?
Answer: B
NEW QUESTION 10
In SmartView Tracker, which rule shows when a packet is dropped due to anti-spoofing?
Answer: A
NEW QUESTION 11
Fill in the blank: A new license should be generated and installed in all of the following situations EXCEPT when ____.
Answer: A
Explanation:
There is no need to generate new license in this situation, just need to detach license from wrong Security Gateway and attach it to the right one.
NEW QUESTION 12
Fill in the blank: The R80 feature _____ permits blocking specific IP addresses for a specified time period.
Answer: C
Explanation:
Suspicious Activity Rules Solution
Suspicious Activity Rules is a utility integrated into SmartView Monitor that is used to modify access privileges upon detection of any suspicious network activity (for example, several attempts to gain unauthorized access).
The detection of suspicious activity is based on the creation of Suspicious Activity rules. Suspicious Activity rules are Firewall rules that enable the system administrator to instantly block suspicious connections that are not restricted by the currently enforced security policy. These rules, once set (usually with an expiration date), can be applied immediately without the need to perform an Install Policy operation
NEW QUESTION 13
Which type of Check Point license is tied to the IP address of a specific Security Gateway and cannot be transferred to a gateway that has a different IP address?
Answer: D
NEW QUESTION 14
What does the “unknown” SIC status shown on SmartConsole mean?
Answer: D
Explanation:
The most typical status is Communicating. Any other status indicates that the SIC communication is problematic. For example, if the SIC status is Unknown then there is no connection between the Gateway an the Security Management server. If the SIC status is Not Communicating, the Security Management server is able to contact the gateway, but SIC communication cannot be established.
NEW QUESTION 15
Which command is used to obtain the configuration lock in Gaia?
Answer: A
Explanation:
Obtaining a Configuration Lock
lock database override
unlock database
NEW QUESTION 16
The organization's security manager wishes to back up just the Gaia operating system parameters. Which command can be used to back up only Gaia operating system parameters like interface details, Static routes and Proxy ARP entries?
Answer: B
Explanation:
3. System Backup (and System Restore)
System Backup can be used to backup current system configuration. A backup creates a compressed file that contains the Check Point configuration including the networking and operating system parameters, such as routing and interface configuration etc., but unlike a snapshot, it does not include the operating system, product binaries, and hotfixes.
NEW QUESTION 17
All R77 Security Servers can perform authentication with the exception of one. Which of the Security Servers can NOT perform authentication?
Answer: B
NEW QUESTION 18
When using GAiA, it might be necessary to temporarily change the MAC address of the interface eth 0 to 00:0C:29:12:34:56. After restarting the network the old MAC address should be active. How do you configure this change?
Answer: C
NEW QUESTION 19
SandBlast offers flexibility in implementation based on their individual business needs. What is an option for deployment of Check Point SandBlast Zero-Day Protection?
Answer: A
NEW QUESTION 20
Choose what BEST describes the reason why querying logs now is very fast.
Answer: B
NEW QUESTION 21
......
P.S. Certleader now are offering 100% pass ensure 156-215.80 dumps! All 156-215.80 exam questions have been updated with correct answers: https://www.certleader.com/156-215.80-dumps.html (485 New Questions)