
Proper study guides for Up to the immediate present CheckPoint Check Point Certified Security Expert Update Blade certified begins with CheckPoint 156-915.77 preparation products which designed to deliver the Best Quality 156-915.77 questions by making you pass the 156-915.77 test at your first time. Try the free 156-915.77 demo right now.
Free 156-915.77 Demo Online For CheckPoint Certifitcation:
NEW QUESTION 1
Your R77 primary Security Management Server is installed on GAiA. You plan to schedule the Security Management Server to run fw logswitch automatically every 48 hours. How do you create this schedule?
Answer: B
NEW QUESTION 2
Which of the following items should be configured for the Security Management Server to authenticate via LDAP?
Answer: B
NEW QUESTION 3
CORRECT TEXT
The command useful for debugging by capturing packet information, including verifying LDAP authentication on all Check Point platforms is
Answer: A
NEW QUESTION 4
Which Security Gateway R77 configuration setting forces the Client Authentication authorization time-out to refresh, each time a new user is authenticated? The:
Answer: C
NEW QUESTION 5
After filtering a fw monitor trace by port and IP, a packet is displayed three times; in the i, I, and o inspection points, but not in the O inspection point. Which is the likely source of the issue?
Answer: D
NEW QUESTION 6
Your company has the requirement that SmartEvent reports should show a detailed and accurate view of network activity but also performance should be guaranteed. Which actions should be taken to achieve that?
1) Use same hard drive for database directory, log files, and temporary directory.
2) Use Consolidation Rules.
3) Limit logging to blocked traffic only.
4) Use Multiple Database Tables.
Answer: A
NEW QUESTION 7
Which process should you debug if SmartDashboard login fails?
Answer: D
NEW QUESTION 8
Which of the following statements accurately describes the command snapshot?
Answer: A
NEW QUESTION 9
CORRECT TEXT
Fill in the blank. To save your OSPF configuration in GAiA, enter the command _____.
Answer: A
NEW QUESTION 10
When do modifications to the Event Policy take effect?
Answer: B
NEW QUESTION 11
Users with Identity Awareness Agent installed on their machines login with , so that when the user logs into the domain, that information is also used to meet Identity Awareness credential requests.
Answer: D
NEW QUESTION 12
Your internal network is configured to be 10.1.1.0/24. This network is behind your perimeter R77 Gateway, which connects to your ISP provider. How do you configure the Gateway to allow this network to go out to the Internet?
Answer: A
NEW QUESTION 13
Match the VPN-related terms with their definitions. Each correct term is only used once.
Exhibit: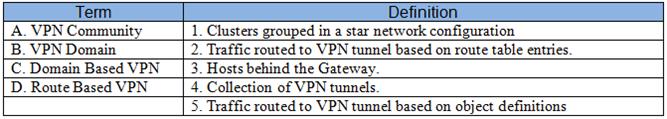
Answer: B
NEW QUESTION 14
You cannot use SmartDashboard’s User Directory features to connect to the LDAP server. What should you investigate?
1) Verify you have read-only permissions as administrator for the operating system.
2) Verify there are no restrictions blocking SmartDashboard's User Manager from connecting to the LDAP server.
3) Check that the login Distinguished Name configured has root permission (or at least write permission Administrative access) in the LDAP Server's access control configuration.
Answer: B
NEW QUESTION 15
In the Rule Base displayed, user authentication in Rule 4 is configured as fully automatic. Eric is a member of the LDAP group, MSD_Group.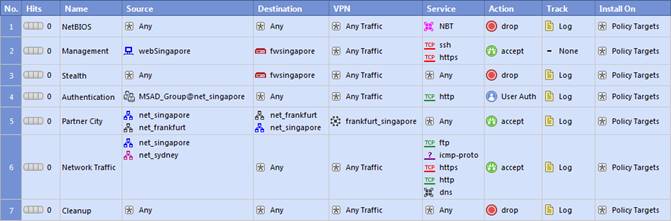
What happens when Eric tries to connect to a server on the Internet?
Answer: D
NEW QUESTION 16
A Web server behind the Security Gateway is set to Automatic Static NAT. Client side NAT is not checked in the Global Properties. A client on the Internet initiates a session to the Web Server. Assuming there is a rule allowing this traffic, what other configuration must be done to allow the traffic to reach the Web server?
Answer: C
NEW QUESTION 17
CORRECT TEXT
Type the command and syntax to view critical devices on a cluster member in a ClusterXL environment.
Answer: A
NEW QUESTION 18
Update the new topology in the cluster object from SmartDashboard.
Answer: A
NEW QUESTION 19
You have created a Rule Base for firewall, websydney. Now you are going to create a new policy package with security and address translation rules for a second Gateway.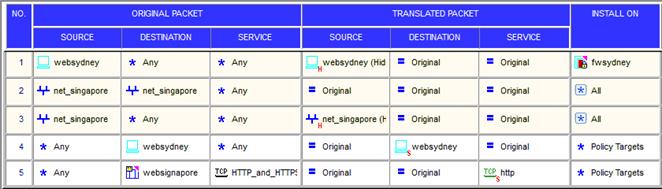
What is TRUE about the new package’s NAT rules?
Answer: A
NEW QUESTION 20
Which command will erase all CRL’s?
Answer: C
NEW QUESTION 21
......
Recommend!! Get the Full 156-915.77 dumps in VCE and PDF From Dumpscollection.com, Welcome to Download: https://www.dumpscollection.net/dumps/156-915.77/ (New 203 Q&As Version)