
Proper study guides for 1D0-61C CIW Network Technology Associate certified begins with preparation products which designed to deliver the by making you pass the 1D0-61C test at your first time. Try the free right now.
Free 1D0-61C Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
Which of the following statementabout virtualization is true?
Answer: D
NEW QUESTION 2
SuperBank is considering a cloud service from Local Data Center, Inc., to support the bank’s expanding needs. SuperBank’s managers are concerned about security. What can SuperBank request to protect its data from security threats?
Answer: D
NEW QUESTION 3
Lisa is traveling on company business. She has a company-issued smartphone with 4G access. Her hotel does not provide Internet access. What advantage does4G provide to help her access the Internet?
Answer: A
NEW QUESTION 4
Consider the network configuration shown in the command prompt: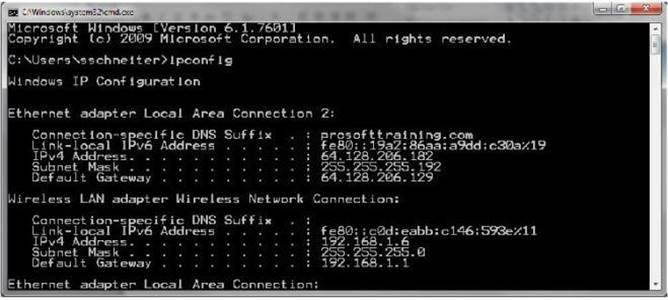
What does the Default Gateway identify?
Answer: D
NEW QUESTION 5
Which term describes a compact personal computer that relies on a touch screen forinput, generally uses a solid-state drive instead of a traditional hard disk, and relies on wireless or mobile networks for connectivity?
Answer: A
NEW QUESTION 6
What should be your first step when troubleshooting a network connection that uses a cable modem?
Answer: D
NEW QUESTION 7
You want to enable wireless security on your Android device and your Linux system. Which of the following is a disadvantage of Wired Equivalent Privacy (WEP)?
Answer: B
NEW QUESTION 8
ABC Company develops itsowndatabase applications. ABC is considering migrating to cloud services to accommodate the company’s growth. What strategy should ABC use to ensure continuous data protection if it begins using cloud services?
Answer: C
NEW QUESTION 9
Which of the following is a drawback to using Wired Equivalent Privacy (WEP)?
Answer: B
NEW QUESTION 10
Ron has an older computer to which he frequently downloads and saves company files. He recently noticed that he was running low on disk space and decided to delete many old files that he no longer needed. He now notices that it takes a long time to open or save documents to his hard drive. Which maintenance task can help?
Answer: A
NEW QUESTION 11
Your company is investigating the possibility of moving its customer service management system to a cloud service provider. The sales rep for the cloud service provider has presented many advantages that would benefit your company. What would be a potential drawback of moving the CRM from your current in-house solution?
Answer: A
NEW QUESTION 12
Sam is a professor at a small college. Due to a scheduling conflict, he was unable to obtain access to the computer lab to give the final exam. As an alternative, he asked students to bring their own devices (BYOD) and connect to the college’s Wi-Fi for network access. What security risk is associated with this implementation?
Answer: C
NEW QUESTION 13
Henry is the network manager at XYY Corporation, a large manufacturing company that competes in the global market. The company’s computing environment is extremely complex and includes several proprietary software systems, all of which require custom configuration of network devices to operate correctly. The company’s executive management team believes that they can benefit by switching the company over to any cloud-based service. Henry disagrees.
What is a disadvantage of cloud-based services that Henry can cite to support his position?
Answer: D
NEW QUESTION 14
You are distributing a large video game file using BitTorrent. First, you upload the initial file and make it available via a central server called a tracker. Other users can then connect to the tracker and download the file. Each user who downloads the file makesit available to other users todownload. The use of BitTorrent significantly reduces the original provider’s hardware and bandwidth resource costs. BitTorrent is an example of what type of network?
Answer: C
NEW QUESTION 15
Jenny recently switched from broadband cable Internet to ADSL service with her local phone company.
To economize, she chose the self-installation option. It appears that her ADSL modem is not allowing her to connect to the Internet. Which setting should she check first?
Answer: C
NEW QUESTION 16
Sally is a network technician at Acme Corporation. She has been directed to configure the network adapter for a company laptop so that it can be used to connect to the company network and the Internet. What is one of the required TCP/IP settings that she will need to configure?
Answer: B
Thanks for reading the newest 1D0-61C exam dumps! We recommend you to try the PREMIUM prep-labs.com 1D0-61C dumps in VCE and PDF here: https://www.prep-labs.com/dumps/1D0-61C/ (59 Q&As Dumps)