
are updated and are verified by experts. Once you have completely prepared with our you will be ready for the real 1Z0-821 exam without a problem. We have . PASSED First attempt! Here What I Did.
Also have 1Z0-821 free dumps questions for you:
NEW QUESTION 1
Which two statements describe the COMSTAR framework available in Oracle Solaris 11?
Answer: AB
Explanation: A: You can configure Common Multiprotocol SCSI TARget, or COMSTAR, a software
framework that enables you to convert any Oracle Solaris 11 host into a SCSI target device that can be accessed over a storage network by initiator hosts.
This means you can make storage devices on a system available to Linux, Mac OS, or Windows client systems as if they were local storage devices. Supported storage protocols are iSCSI, FC, iSER, and SRP.
B: iSCSI targets cannot be configured as dump devices.
NEW QUESTION 2
Subnets are created by using .
Answer: B
Explanation: The process of subnetting involves the separation of the network and subnet portion of an address from the host identifier. This is performed by a bitwise AND operation between the IP address and the (sub)network prefix. The result yields the network address or prefix, and the remainder is the host identifier.
The routing prefix of an address is written in a form identical to that of the address itself. This is called the network mask, or netmask, of the address. For example, a specification of the most-significant 18 bits of an IPv4 address, 11111111.11111111.11000000.00000000, is written as 255.255.192.0.
NEW QUESTION 3
Which files must be edited in order to set up logging of all failed login attempts?
Answer: B
Explanation: This procedure captures in a syslog file all failed login attempts.
1. Set up the /etc/default/login file with the desired values for SYSLOG and SYSLOG_FAILED_LOGINS
Edit the /etc/default/login file to change the entry. Make sure that SYSLOG=YES is uncommented.
2. Create a file with the correct permissions to hold the logging information. Create the authlog file in the /var/adm directory.
3. Edit the syslog.conf file to log failed password attempts. Send the failures to the authlog file.
NEW QUESTION 4
View the Exhibit and review the disk configuration.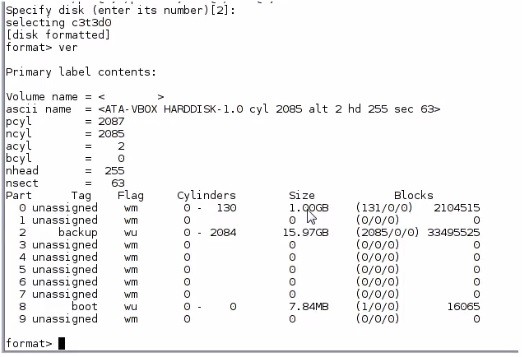
The following command is executed on the disk: zpool create pool1 c3t3d0s0
What is the result of executing this command?
Answer: B
NEW QUESTION 5
On server A, you enter the following command to add a static route to serverA route -p add
-host 192.168.1.101 192.168.1.101 -static
What is the purpose of this command?
Answer: B
Explanation: Note: # route -p add -host destination-IP gateway-IP -static
where destination-IP and gateway-IP are IPv4 addresses of the host to be used as a target.
For example, you would type the following to specify the target system 192.168.10.137, which is on the same subnet as the interfaces in IPMP group itops0:
$ route -p add -host 192.168.10.137 192.168.10.137 -static
This new route will be automatically configured every time the system is restarted. If you
want to define only a temporary route to a target system for probe-based failure detection, then do not use the -p option.
NEW QUESTION 6
Which option would you choose to display the kernel revision level for your operating system?
Answer: B
NEW QUESTION 7
You are going to use the- Automated installer (AI) to install a non global zone named zone1. You have created a custom manifest for the non-global zone and named it zone1manifest
Which command will you use to add this custom manifest to the s11-sparc install service and associate this custom manifest with the non-global zone?
Answer: B
Explanation: installadm add-manifest
Associates manifests with a specific install service, thus making the manifests available on the network, independently from creating a service. When publishing a non-default manifest, it is required to associate criteria either via criteria entered on the command line (-c) or via a criteria XML file (-C).
NEW QUESTION 8
View the Exhibit.
The file came from your Automated Installer (AI) install server. The file is .
Answer: D
Explanation: ai_manifest
- Automated installation manifest file format
Synopsis
/usr/share/install/ai.dtd.1
Some customizations have been made, such as the selection of specific locales.
NEW QUESTION 9
Which two options are characteristics of a fast reboot?
Answer: CD
Explanation: C: To change the default behavior of the Fast Reboot feature on the SPARC platform, so that a fast reboot is automatically performed when the system reboots, see below.
The following example shows how to set the property's value to true on the SPARC platform, so that a fast reboot is initiated by default:
# svccfg -s "system/boot-config:default" setprop config/fastreboot_default=true
# svcadm refresh svc:/system/boot-config:default
D: Fast Reboot implements an in-kernel boot loader that loads the kernel into memory and then switches to that kernel.
The firmware and boot loader processes are bypassed, which enables the system to reboot within seconds.
The Fast Reboot feature is managed by SMF and implemented through a boot configuration service, svc:/system/boot-config. The boot-config service provides a means for setting or changing the default boot configuration parameters. When the config/fastreboot_default property is set to true, the system performs a fast reboot automatically, without the need to use the reboot -f command. This property's value is set to true on the x86 platform. For task-related information, including how to change the default behavior of Fast Reboot on the SPARC platform, see Accelerating the Reboot Process on an x86 Based System.
Note: One new feature, called Fast Reboot, will allow the system to boot up without doing the routine set of hardware checks, a move that can make system boot times up to two- and-a-half times faster, Oracle claimed. This feature can be handy in that an administrator applying a patch or software update across thousands of Solaris deployments can reboot them all the more quickly.
NEW QUESTION 10
You have already generated a 256-bit AES raw key and named the keystore file /mykey. You need to use the key to create an encrypted file system.
Which command should you use to create a ZFS encrypted file system named pool1/encrypt using the /mykey keystore?
Answer: B
Explanation: Example: Encrypting a ZFS File System by Using a Raw Key
In the following example, an aes-256-ccm encryption key is generated by using the pktool command and is written to a file, /cindykey.file.
# pktool genkey keystore=file outkey=/cindykey.file keytype=aes keylen=256
Then, the /cindykey.file is specified when the tank/home/cindy file system is created.
# zfs create -o encryption=aes-256-ccm -o keysource=raw, file:///cindykey.file tank/home/cindys
NEW QUESTION 11
Identify the two security features incorporated in the Oracle Solaris 11 Cryptographic Framework.
Answer: DE
Explanation: The framework enables providers of cryptographic services to have their services used by many consumers in the Oracle Solaris operating system. Another name for providers is plugins. The framework allows three types of plugins:
* User-level plugins - Shared objects that provide services by using PKCS #11 libraries, such as pkcs11_softtoken.so.1.
* Kernel-level plugins - Kernel modules that provide implementations of cryptographic algorithms in software, such as AES.
Many of the algorithms in the framework are optimized for x86 with the SSE2 instruction set and for SPARC hardware.
* Hardware plugins - Device drivers and their associated hardware accelerators. The Niagara chips, the ncp and n2cp device drivers, are one example. A hardware accelerator offloads expensive cryptographic functions from the operating system. The Sun Crypto Accelerator 6000 board is one example.
NEW QUESTION 12
You are attempting to troubleshoot an event that should have made an entry into the messages log. This event happened about two weeks ago. Which file should you look at
first?
Answer: A
Explanation: The /var/adm/messages is the file to which all the messages printed on the console are logged to by the Operating System. This helps to track back check the console messages to troubleshoot any issues on the system.
Syslog daemon also writes to this /var/adm/messages file.
The /var/adm/messages file monitored and managed by newsyslog and its configuration file is /usr/lib/newsyslog.
This script runs as the roots cron job everyday, checks the /var/adm/messages file and copies/moves it to /var/adm/messages.0, 1, 2, 3, 4, 5, 6, 7. In other words, it does the Log Rotation for the /var/adm/messages.
In an event the /var file system is running out of space, these files needs to checked and can be removed (not the actual /var/adm/messages itself) to free up space on the file system.
However, care has to be taken, if you decide to empty the /var/adm/messages itself for any reason. This process is called Truncation.
SOLARIS SYSTEM ADMIN TIPS, /var/adm/messages
NEW QUESTION 13
The COMSTAR framework provides support for the iSCSI protocol. Select three options that correctly describe the COMSTAR framework.
Answer: BDE
Explanation: B: By carrying SCSI commands over IP networks, the iSCSI protocol enables you to access block devices from across the network as if they were connected to the local system. COMSTAR provides an easier way to manage these iSCSI target devices.
D: Common Multiprotocol SCSI TARget, or COMSTAR, a software framework that enables you to convert any Oracle Solaris 11 host into a SCSI target device that can be accessed over a storage network by initiator hosts.
E: One IP port can handle multiple iSCSI target devices.
NEW QUESTION 14
Review the zonestat command:
zonestate - q physical - memory -R high -z -p -p “zones” 10 24h 60m
Select the option that correctly describes the information that is displayed by this command.
Answer: D
Explanation: * (Not A, B, C): interval (here 10 seconds): Specifies the length in seconds to pause between each interval report.
* duration (here 24 h)
* -R report[, report] (here high) Print a summary report.
High Print a summary report detailing the highest usage of each resource and zone during any interval of the zonestat utility invocation.
Note: The zonestat utility reports on the cpu, memory, and resource control utilization of the currently running zones. Each zone's utilization is reported both as a percentage of system resources and the zone's configured limits.
The zonestat utility prints a series of interval reports at the specified interval. It optionally
also prints one or more summary reports at a specified interval.
The default output is a summary of cpu, physical, and virtual memory utilization. The -r option can be used to choose detailed output for specific resources.
NEW QUESTION 15
The core dump configuration for your system is:
A user is running a process in the global zone and the process crashes. The process information is:
User1 2663 2618 0 17:46:42 pts/2 0:00 /usr/bin/bash
The server host name is: zeus
What will the per-process core file be named?
Answer: C
Explanation: Note the first line:
global core file pattern: /globalcore/core.%f.%p
The program name is bash The runtime process ID is 2663
Note: By default, the global core dump is disabled. You need to use the coreadm command with the -e global option to enable it. The -g option causes the command to append the program name(%f) and the runtime process ID (%p) to the core file name.
NEW QUESTION 16
You need to make sure that all of the software packages on your server are up to date. Without installing any updates, which two commands would display .my software updates that are available in the default Oracle repository?
Answer: AD
Explanation: A: the pgk list command display a list of packages in the current image, including state and other information. By default, package variants for a different architecture or zone type are excluded.
D: pkginfo displays information about software packages that are installed on the system (with the first synopsis, with -l) or that reside on a particular device or directory (with the second synopsis, with -r).
Without options, pkginfo lists the primary category, package instance, and the names of all completely installed and partially installed packages. It displays one line for each package selected.
With -r, retrieve the data from the repositories of the image's configured publishers. Note that you must specify one or more package patterns in this case.
NEW QUESTION 17
Which two options are valid methods of installing a solaris10 branded zone on a system running Oracle Solaris 11?
Answer: BC
Explanation: B: How to Migrate an Existing native Non-Global Zone
Use the V2V process to migrate an existing zone on your Solaris 10 system to a solaris10 brand zone on a system running the Oracle Solaris 11 release.
C: How to Install the solaris10 Branded Zone
A configured solaris10 branded zone is installed by using the zoneadm command with the install subcommand.
NEW QUESTION 18
You have completed configuring a zone named dbzone on your Solaris 11 server. The configuration is as following: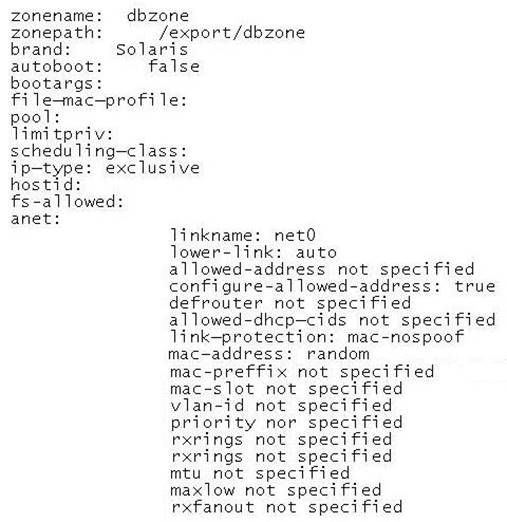
The global zone displays the following network information: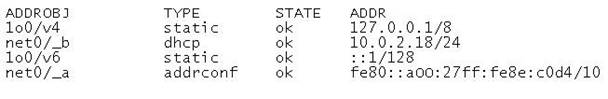
The zone has never been booted. Which three options correctly describe this zone?
Answer: CEG
Explanation: C: Immutable Zones provide read-only file system profiles for solaris non-global zones. Note that ip-type: exclusive:
Starting with OpenSolaris build 37 and Oracle Solaris 10 8/07, a default zone can be configured as an "exclusive-IP zone" which gives it exclusive access to the NIC(s) that the zone has been assigned. Applications in such a zone can communicate directly with the NIC(s) available to the zone.
Note on zones:
After installing Oracle Solaris on a system, but before creating any zones, all processes run in the global zone. After you create a zone, it has processes that are associated with that zone and no other zone. Any process created by a process in a non-global zone is also associated with that non-global zone.
Any zone which is not the global zone is called a non-global zone. Most people call non- global zones simply "zones." Some people call them "local zones" but this is discouraged.
The default native zone file system model on Oracle Solaris 10 is called "sparse-root." This model emphasizes efficiency and security at the cost of some configuration flexibility. Sparse-root zones optimize physical memory and disk space usage by sharing some directories, like /usr and /lib. Sparse-root zones have their own private file areas for directories like /etc and /var. Whole-root zones increase configuration flexibility but increase resource usage. They do not use shared file systems for /usr, /lib, and a few others.
There is no supported way to convert an existing sparse-root zone to a whole-root zone. Creating a new zone is required.
NEW QUESTION 19
A user account must be a member of a primary group, and may also be a member of one or more secondary groups. What is the maximum total number of groups that one user can concurrently belong to?
Answer: B
Explanation: Each user belongs to a group that is referred to as the user’s primary group. The GID number, located in the user’s account entry within the /etc/passwd file, specifies the user’s primary group.
Each user can also belong to up to 15 additional groups, known as secondary groups. In the /etc/group file, you can add users to group entries, thus establishing the user’s secondary group affiliations.
Note (4 PSARC/2009/542):
his project proposes changing the maximum value for NGROUPS_MAX from 32 to 1024 by changing the definition of NGROUPS_UMAX from 32 to 1024.
The use for a larger number of groups is described in CR 4088757, particular in the case of Samba servers and ADS clients; the Samba servers map every SID to a Unix group. Users with more than 32 groups SIDs are common. We've seen reports varying from "64 is enough", "128 is absolutely enough" and "we've users with more 190 group SIDS).
NGROUPS_MAX as defined by different Unix versions are as follows (http://www.j3e.de/ngroups.html):
Linux Kernel >= 2.6.3 65536
Linux Kernel < 2.6.3 32 Tru64 / OSF/1 32
IBM AIX 5.2 64
IBM AIX 5.3 ... 6.1 128
OpenBSD, NetBSD, FreeBSD, Darwin (Mac OS X) 16 Sun Solaris 7, 8, 9, 10 16 (can vary from 0-32)
HP-UX 20
IRIX 16 (can vary from 0-32)
Plan 9 from Bell Labs 32
Minix 3 0 (Minix-vmd: 16)
QNX 6.4 8
P.S. Easily pass 1Z0-821 Exam with 243 Q&As Exambible Dumps & pdf Version, Welcome to Download the Newest Exambible 1Z0-821 Dumps: https://www.exambible.com/1Z0-821-exam/ (243 New Questions)