
Master the 200-201 Understanding Cisco Cybersecurity Operations Fundamentals content and be ready for exam day success quickly with this Pass4sure 200-201 exam answers. We guarantee it!We make it a reality and give you real 200-201 questions in our Cisco 200-201 braindumps.Latest 100% VALID Cisco 200-201 Exam Questions Dumps at below page. You can use our Cisco 200-201 braindumps and pass your exam.
Check 200-201 free dumps before getting the full version:
NEW QUESTION 1
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
Answer: D
NEW QUESTION 2
What is the difference between a threat and a risk?
Answer: A
NEW QUESTION 3
Refer to the exhibit.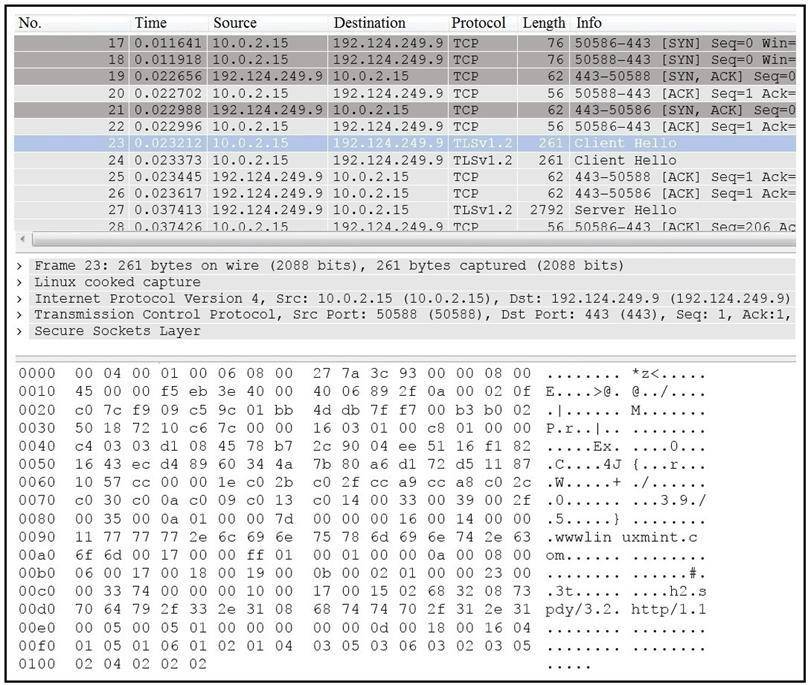
Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.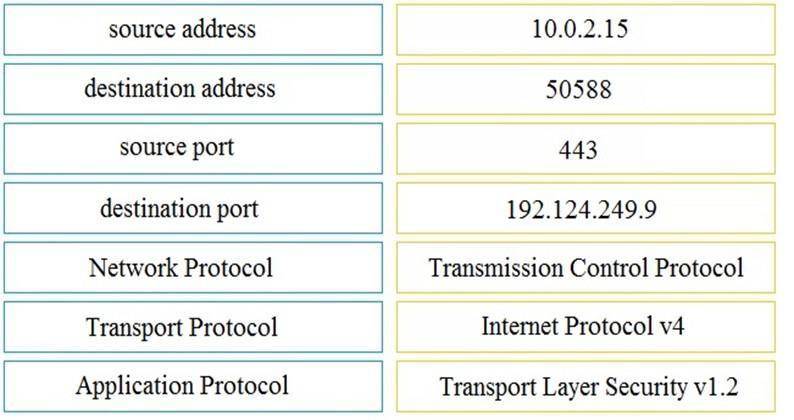
Answer: A
Explanation: 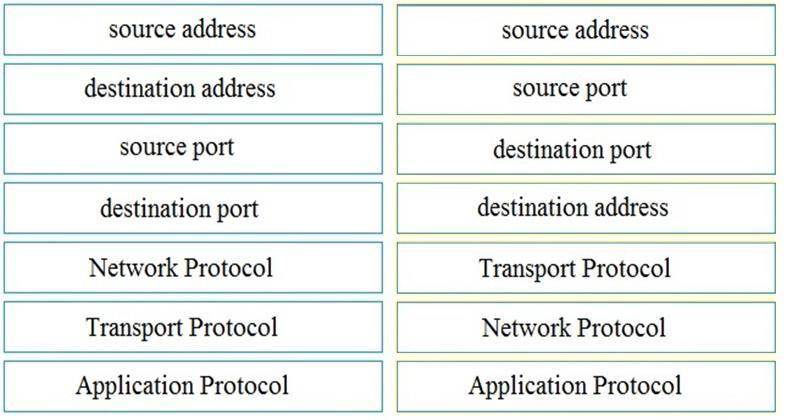
NEW QUESTION 4
At which layer is deep packet inspection investigated on a firewall?
Answer: C
NEW QUESTION 5
What are two social engineering techniques? (Choose two.)
Answer: CE
NEW QUESTION 6
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication.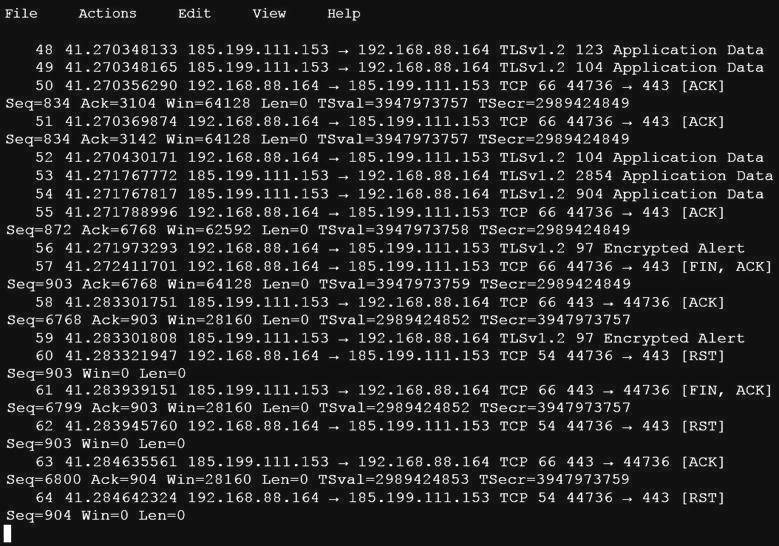
Which obfuscation technique is the attacker using?
Answer: B
NEW QUESTION 7
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
Answer: B
NEW QUESTION 8
Which security technology allows only a set of pre-approved applications to run on a system?
Answer: C
NEW QUESTION 9
Which process is used when IPS events are removed to improve data integrity?
Answer: B
NEW QUESTION 10
A security expert is working on a copy of the evidence, an ISO file that is saved in CDFS format. Which type of evidence is this file?
Answer: A
NEW QUESTION 11
Which type of evidence supports a theory or an assumption that results from initial evidence?
Answer: D
NEW QUESTION 12
Which evasion technique is a function of ransomware?
Answer: B
NEW QUESTION 13
What specific type of analysis is assigning values to the scenario to see expected outcomes?
Answer: A
NEW QUESTION 14
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor.
Which type of evidence is this?
Answer: C
NEW QUESTION 15
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
Answer: AE
NEW QUESTION 16
What is the difference between deep packet inspection and stateful inspection?
Answer: D
NEW QUESTION 17
The target web application server is running as the root user and is vulnerable to command injection. Which result of a successful attack is true?
Answer: B
NEW QUESTION 18
Refer to the exhibit.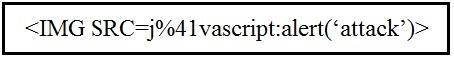
Which kind of attack method is depicted in this string?
Answer: A
NEW QUESTION 19
Which two elements are used for profiling a network? (Choose two.)
Answer: DE
NEW QUESTION 20
What does an attacker use to determine which network ports are listening on a potential target device?
Answer: B
NEW QUESTION 21
......
P.S. Easily pass 200-201 Exam with 98 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam 200-201 Dumps: https://www.surepassexam.com/200-201-exam-dumps.html (98 New Questions)