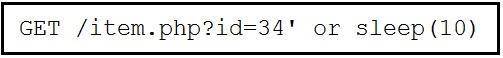- Home
- Cisco
- 200-201 Exam
Cisco 200-201 Free Practice Questions
Exam Code: 200-201 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Understanding Cisco Cybersecurity Operations Fundamentals
Certification Provider: Cisco
Free Today! Guaranteed Training- Pass 200-201 Exam.
Also have 200-201 free dumps questions for you:
NEW QUESTION 1
Which artifact is used to uniquely identify a detected file?
- A. file timestamp
- B. file extension
- C. file size
- D. file hash
Answer: D
NEW QUESTION 2
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header.
Which technology makes this behavior possible?
- A. encapsulation
- B. TOR
- C. tunneling
- D. NAT
Answer: D
NEW QUESTION 3
Refer to the exhibit.
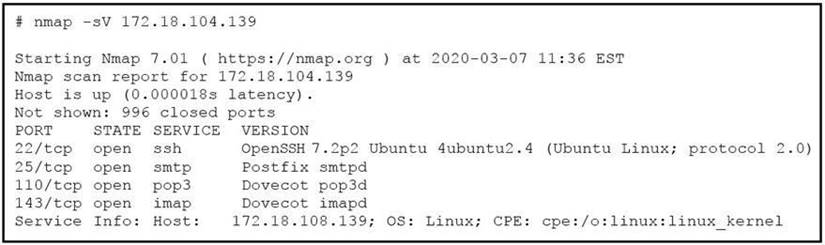
What does the output indicate about the server with the IP address 172.18.104.139?
- A. open ports of a web server
- B. open port of an FTP server
- C. open ports of an email server
- D. running processes of the server
Answer: C
NEW QUESTION 4
What is the function of a command and control server?
- A. It enumerates open ports on a network device
- B. It drops secondary payload into malware
- C. It is used to regain control of the network after a compromise
- D. It sends instruction to a compromised system
Answer: D
NEW QUESTION 5
Which type of data consists of connection level, application-specific records generated from network traffic?
- A. transaction data
- B. location data
- C. statistical data
- D. alert data
Answer: A
NEW QUESTION 6
What is personally identifiable information that must be safeguarded from unauthorized access?
- A. date of birth
- B. driver's license number
- C. gender
- D. zip code
Answer: B
NEW QUESTION 7
Refer to the exhibit.
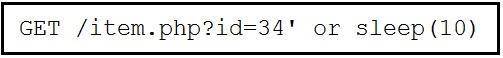
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
- A. parameter manipulation
- B. heap memory corruption
- C. command injection
- D. blind SQL injection
Answer: D
NEW QUESTION 8
Which signature impacts network traffic by causing legitimate traffic to be blocked?
- A. false negative
- B. true positive
- C. true negative
- D. false positive
Answer: D
NEW QUESTION 9
Which security principle requires more than one person is required to perform a critical task?
- A. least privilege
- B. need to know
- C. separation of duties
- D. due diligence
Answer: C
NEW QUESTION 10
Which regular expression matches "color" and "colour"?
- A. colo?ur
- B. col[08]+our
- C. colou?r
- D. col[09]+our
Answer: C
NEW QUESTION 11
Which two pieces of information are collected from the IPv4 protocol header? (Choose two.)
- A. UDP port to which the traffic is destined
- B. TCP port from which the traffic was sourced
- C. source IP address of the packet
- D. destination IP address of the packet
- E. UDP port from which the traffic is sourced
Answer: CD
NEW QUESTION 12
Refer to the exhibit.
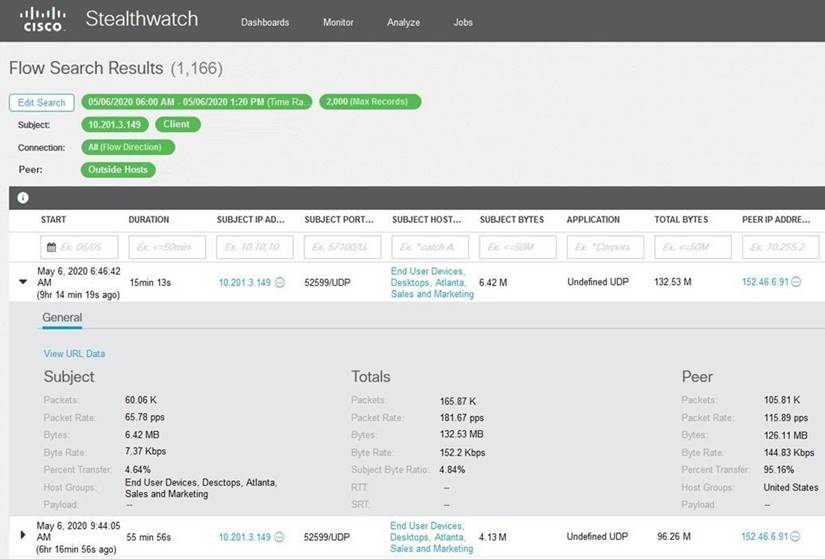
What is the potential threat identified in this Stealthwatch dashboard?
- A. Host 10.201.3.149 is sending data to 152.46.6.91 using TCP/443.
- B. Host 152.46.6.91 is being identified as a watchlist country for data transfer.
- C. Traffic to 152.46.6.149 is being denied by an Advanced Network Control policy.
- D. Host 10.201.3.149 is receiving almost 19 times more data than is being sent to host 152.46.6.91.
Answer: D
NEW QUESTION 13
What is an example of social engineering attacks?
- A. receiving an unexpected email from an unknown person with an uncharacteristic attachment from someone in the same company
- B. receiving an email from human resources requesting a visit to their secure website to update contact information
- C. sending a verbal request to an administrator who knows how to change an account password
- D. receiving an invitation to the department’s weekly WebEx meeting
Answer: B
NEW QUESTION 14
Refer to the exhibit.
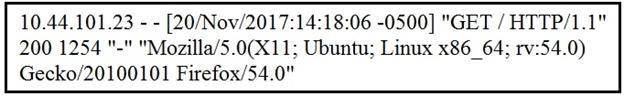
What does the message indicate?
- A. an access attempt was made from the Mosaic web browser
- B. a successful access attempt was made to retrieve the password file
- C. a successful access attempt was made to retrieve the root of the website
- D. a denied access attempt was made to retrieve the password file
Answer: C
NEW QUESTION 15
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
- A. The computer has a HIPS installed on it.
- B. The computer has a NIPS installed on it.
- C. The computer has a HIDS installed on it.
- D. The computer has a NIDS installed on it.
Answer: C
NEW QUESTION 16
What makes HTTPS traffic difficult to monitor?
- A. SSL interception
- B. packet header size
- C. signature detection time
- D. encryption
Answer: D
NEW QUESTION 17
What is the difference between statistical detection and rule-based detection models?
- A. Rule-based detection involves the collection of data in relation to the behavior of legitimate users over a period of time
- B. Statistical detection defines legitimate data of users over a period of time and rule-based detection defines it on an IF/THEN basis
- C. Statistical detection involves the evaluation of an object on its intended actions before it executes that behavior
- D. Rule-based detection defines legitimate data of users over a period of time and statistical detection defines it on an IF/THEN basis
Answer: B
NEW QUESTION 18
Which utility blocks a host portscan?
- A. HIDS
- B. sandboxing
- C. host-based firewall
- D. antimalware
Answer: C
NEW QUESTION 19
Refer to the exhibit.

Which two elements in the table are parts of the 5-tuple? (Choose two.)
- A. First Packet
- B. Initiator User
- C. Ingress Security Zone
- D. Source Port
- E. Initiator IP
Answer: DE
NEW QUESTION 20
Refer to the exhibit.

Which type of log is displayed?
- A. IDS
- B. proxy
- C. NetFlow
- D. sys
Answer: D
P.S. Easily pass 200-201 Exam with 98 Q&As Dumpscollection.com Dumps & pdf Version, Welcome to Download the Newest Dumpscollection.com 200-201 Dumps: https://www.dumpscollection.net/dumps/200-201/ (98 New Questions)