
Act now and download your today! Do not waste time for the worthless tutorials. Download with real questions and answers and begin to learn with a classic professional.
Online 300-165 free questions and answers of New Version:
NEW QUESTION 1
DRAG DROP
Drag and drop the optional OSPF parameters from the left onto the correct functions on the right.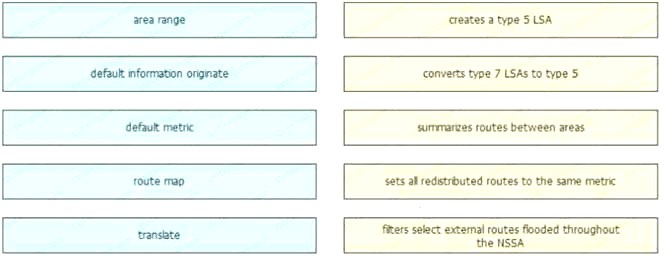
Answer:
Explanation: 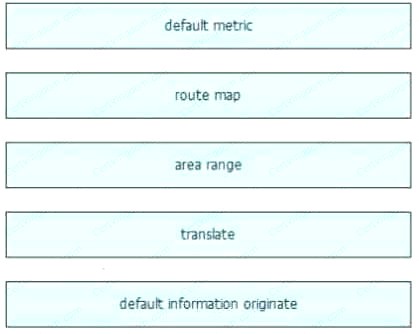
NEW QUESTION 2
Which two security features are only supported on the Cisco Nexus 7000 Series Switches? (Choose two.)
Answer: BF
Explanation: A traffic storm occurs when packets flood the LAN, creating excessive traffic and degrading network performance. You can use the traffic storm control feature to prevent disruptions on Layer 2 ports by a broadcast, multicast, or unicast traffic storm on physical interfaces.
Traffic storm control (also called traffic suppression) allows you to monitor the levels of the incoming broadcast, multicast, and unicast traffic over a 10-millisecond interval. During this interval, the traffic level, which is a percentage of the total available bandwidth of the port, is compared with the traffic storm control level that you configured. When the ingress traffic reaches the traffic storm control level that is configured on the port, traffic storm control drops the traffic until the interval ends. Reference: http://www.cisco.com/c/en/us/td/docs/switches/datacenter/sw/5_x/dcnm/security/configuration/g uide/b_Cisco_DCNM_Security_Configuration_Guide Release_5- x/Cisco_DCNM_Security_Configuration_Guide Release_5-x_chapter17.html
And http://www.cisco.com/c/en/us/td/docs/switches/datacenter/sw/5_x/dcnm/security/configuration/g uide/b_Cisco_DCNM_Security_Configuration_Guide Release_5- x/Cisco_DCNM_Security_Configuration_Guide Release_5-x_chapter1.html
NEW QUESTION 3
Refer to the exhibit.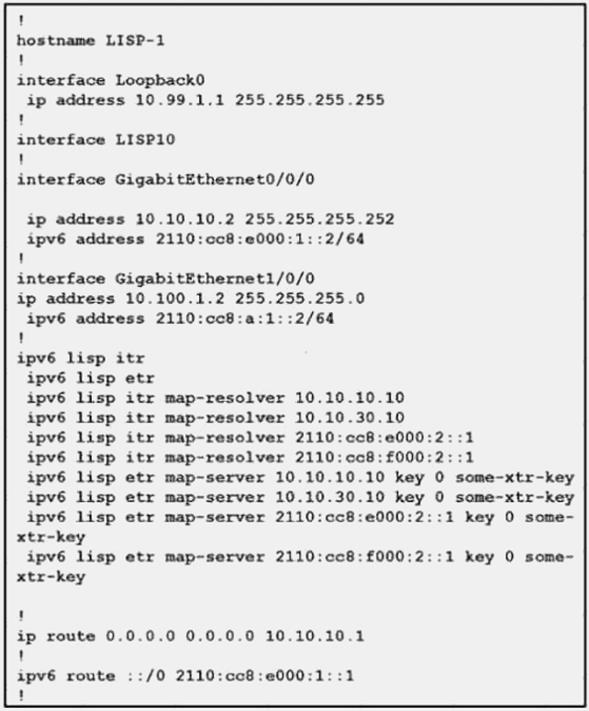
Which statement about the configuration is true?
Answer: A
NEW QUESTION 4
Which example creates an Embedded Event Manager policy allowing the CLI command to execute,
and triggers an SNMP notification when a user enters configuration mode?
A)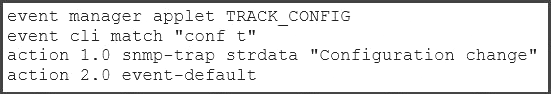
B)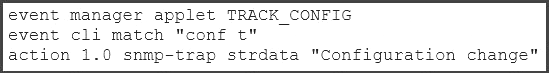
C)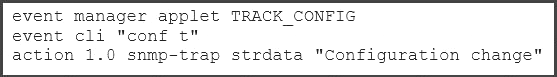
D)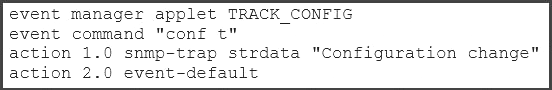
Answer: A
NEW QUESTION 5
Which parameter is configurable when setting up logging on the Connectivity Management Processor?
Answer: D
NEW QUESTION 6
Which option accurately describes an EPLD upgrade on supervisor modules?
Answer: B
NEW QUESTION 7
Which item represents the process that allows FCoE multihop using T11 standard FC-BB-5?
Answer: D
Explanation: FIP snooping is used in multi-hop FCoE environments. FIP snooping is a frame inspection method that can be used by FIP snooping capable DCB devices to monitor FIP frames and apply policies based on the information in those frames. This allows for:
Enhanced FCoE security (Prevents FCoE MAC spoofing.) Creates FC point-to-point links within the Ethernet LAN
Allows auto-configuration of ACLs based on name server information read in the FIP frames Reference:
http://www.definethecloud.net/fcoe-initialization-protocol-fip-deep-dive/
NEW QUESTION 8
Refer to the exhibit.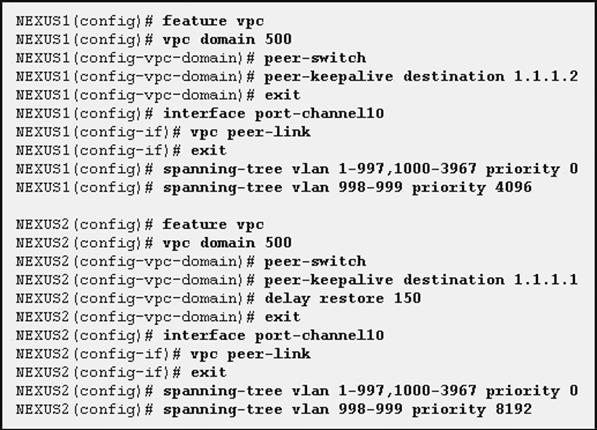
You configure two switches named NEXUS1 and NEXUS2. Which two results of implementing the configuration are true? (Choose two.)
Answer: BE
NEW QUESTION 9
Which two statements about Cisco Nexus 7000 line cards are true? (Choose two.)
Answer: AD
Explanation: Cisco is introducing a new line card called as F3 Module which has rich feature set and offers high performance 40G/100G port density to the Nexus 7000 product family. Cisco also introduced a new feature in NX-OS 6.2(2) where the F2e line card can be in the same VDC as M1 or M2 Line Card. The objective of this session is to cover detailed steps and methodology of migrating Nexus 7000 with VDC types prior to NX-OS 6.2 to the newer F3 or M/F2e VDC types. The session also covers the effect of VDC migration with commonly used Network features, firewall and load balancer services.
M-Series XL modules support larger forwarding tables. M-Series modules are frequently required at network core, peering, and aggregation points. When used with the F1-Series, the M-Series modules provide inter-VLAN services and form a pool of Layer 3 resources for the system.
Reference: https://www.ciscolive2014.com/connect/sessionDetail.ww?SESSION_ID=2244
And http://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Data_Center/VMDC/2- 6/vmdctechwp.html
NEW QUESTION 10
Refer to the exhibit.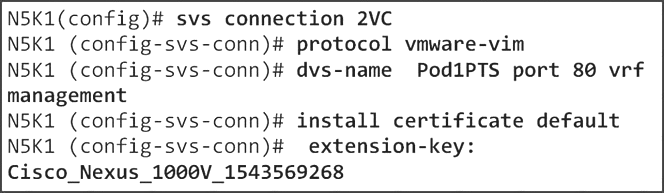
Which two commands are missing from this configuration that an admin needs to integrate a Cisco Nexus 5000 switch with vCenter to leverage VM-FEX? (Choose two.)
Answer: AC
NEW QUESTION 11
Which two options can be used for link aggregation when you configure vPC member interfaces? (Choose two.)
Answer: AC
NEW QUESTION 12
Refer to the exhibit.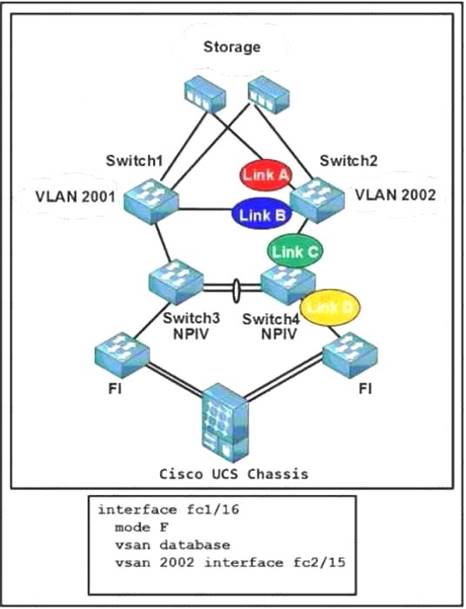
The configuration belongs to which link?
Answer: D
NEW QUESTION 13
Which three options are CallHome predefined destination profiles that are supported on Cisco NXOS? (Choose three.)
Answer: ABD
NEW QUESTION 14
What mode is required on a Cisco Nexus 7000 32-port 10-GB module port group to allow equal access to the 10-GB port controller?
Answer: C
Explanation: You can share 10 Gb of bandwidth among a group of ports (four ports) on a 32-port 10-Gigabit Ethernet module. To share the bandwidth, you must bring the dedicated port administratively down, specify the ports that are to share the bandwidth, change the rate mode to shared, and then bring the ports administratively up.
Reference: http://www.cisco.com/c/en/us/td/docs/switches/datacenter/sw/5_x/nxos/ interfaces/configuration/guide/if_cli/if_basic.html#70242
NEW QUESTION 15
DRAG DROP
Drag the network characteristics on the left to the most appropriate design layer on the right.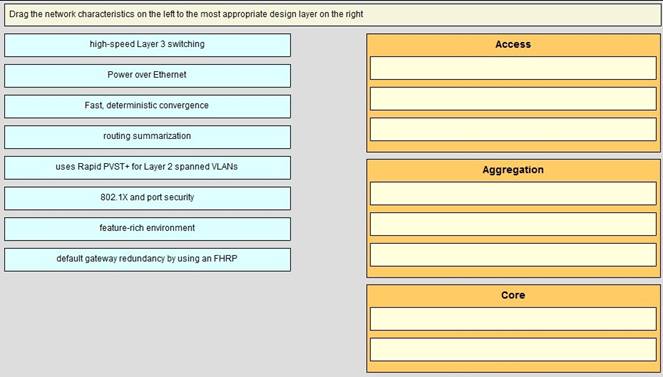
Answer:
Explanation: The access layer is the first tier or edge of the campus. It is the place where end devices (PCs, printers, cameras, and the like) attach to the wired portion of the campus network. It is also the place where devices that extend the network out one more level are attached—IP phones and wireless access points (APs) being the prime two key examples of devices that extend the connectivity out one more layer from the actual campus access switch. The wide variety of possible types of devices that can connect and the various services and dynamic configuration mechanisms that are necessary, make the access layer one of the most feature-rich parts of the campus network. You can enable an 802.1X port for port security by using the dot1x multiple-hosts interface configuration command. You must also configure port security on the port by using the switchport port-security interface configuration command. With the multiple-hosts mode enabled, 802.1X authenticates the port, and port security manages network access for all MAC addresses, including that of the client. You can then limit the number or group of clients that can access the network through an 802.1X multiple-host port.
NEW QUESTION 16
Refer to the exhibit.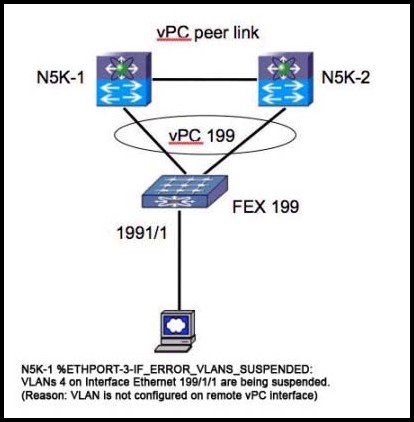
Which corrective action is taken to resolve the problem?
Answer: C
Explanation: Place interface ethernet 199/1/1 in VLAN 4 in the N5K-2 configuration.
P.S. Certstest now are offering 100% pass ensure 300-165 dumps! All 300-165 exam questions have been updated with correct answers: https://www.certstest.com/dumps/300-165/ (286 New Questions)