
Passleader 300-210 Questions are updated and all 300-210 answers are verified by experts. Once you have completely prepared with our 300-210 exam prep kits you will be ready for the real 300-210 exam without a problem. We have Rebirth Cisco 300-210 dumps study guide. PASSED 300-210 First attempt! Here What I Did.
Online Cisco 300-210 free dumps demo Below:
NEW QUESTION 1
Which Cisco WSA is intended for deployment in organizations of more than 6000 users?
Answer: B
NEW QUESTION 2
An engineer manages a Cisco Intrusion Prevention System via IME. A new user must be able to tune signatures, but must not be able to create new users. Which role for the new user is correct?
Answer: C
Explanation:
http://www.cisco.com/c/en/us/td/docs/security/ips/7-0/command/reference/cmdref/crIntro.html
NEW QUESTION 3
When learning accept mode is set to auto, and the action is set to rotate, when is the KB created and used?
Answer: A
NEW QUESTION 4
Which Cisco technology provides spam filtering and email protection?
Answer: B
NEW QUESTION 5
If learning accept mode is set to "auto" and the knowledge base is loaded only when explicitly requested on the IPS, which statement about the knowledge base is true?
Answer: B
NEW QUESTION 6
Which command establishes a virtual console session to a CX module within a Cisco Adaptive Security Appliance?
Answer: E
NEW QUESTION 7
Which two appliances support logical routed interfaces? (Choose two.)
Answer: D
NEW QUESTION 8
Which three protocols are required when considering firewall rules for email services using a Cisco Email Security Appliance? (Choose three.)
Answer: ABC
NEW QUESTION 9
A web security appliance is inspecting inbound traffic. In which sequence is inbound https traffic inspected?
Answer: B
NEW QUESTION 10
Which redundancy protocol is available for Cisco firepower but is a limitation for the WSA?
Answer: C
NEW QUESTION 11
How many interfaces can a Cisco ASA bridge group support and how many bridge groups can a Cisco ASA appliance support?
Answer: D
NEW QUESTION 12
What are three benefits of the Cisco AnyConnect Secure Mobility Solution? (Choose three.)
Answer: BCE
NEW QUESTION 13
Which Cisco AMP file disposition valid?
Answer: B
Explanation:
https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config-guide-v60/Refere
NEW QUESTION 14
Refer to the exhibit.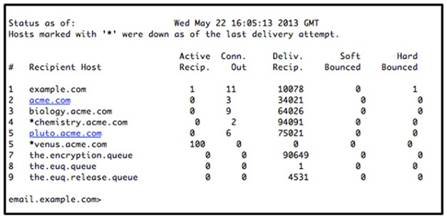
What Cisco ESACLI command generated the output?
Answer: B
NEW QUESTION 15
What is the CLI command to create a new Message Filter in a Cisco Email Security Appliance?
Answer: B
NEW QUESTION 16
In order to set up HTTPS decryption on the Cisco Web Security Appliance, which two steps must be performed? (Choose two.)
Answer: AC
NEW QUESTION 17
What is the function of the Web Proxy Auto Discovery protocol?
Answer: D
NEW QUESTION 18
Which option represents the cisco event aggregation product?
Answer: C
NEW QUESTION 19
Which three zones are used for anomaly detection in a Cisco IPS? (Choose three.)
Answer: ABC
NEW QUESTION 20
With Cisco ASA active/standby failover, what is needed to enable subsecond failover?
Answer: C
NEW QUESTION 21
Which three options are characteristics of router-based IPS? (Choose three.)
Answer: BDF
NEW QUESTION 22
Which signature engine is responsible for ICMP inspection on Cisco IPS?
Answer: D
NEW QUESTION 23
Which three protocols are required when considering firewall rules email services using a Cisco Email Security Appliance?
Answer: ABE
NEW QUESTION 24
Which standby protocol which works on NGIPS but not on CWS?
Answer: C
NEW QUESTION 25
Which four advanced endpoint assessment statements are correct? (Choose four.)
Answer: ABCF
NEW QUESTION 26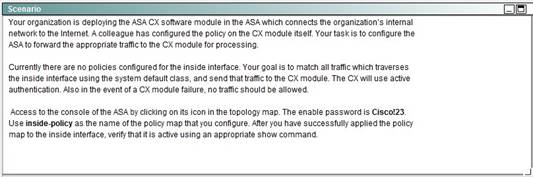
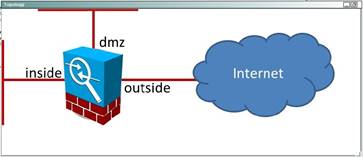
Answer: A
Explanation:
We need to create a policy map named inside-policy and send the traffic to the CXSC blade:
ASA-FW# config t
ASA-FW(config)# policy-map inside-policy
ASA-FW(config-pmap)# policy-map inside-policy ASA-FW(config-pmap)# class class-default
ASA-FW(config-pmap-c)# cxsc fail-close auth-proxy ASA-FW(config-pmap-c)# exit
ASA-FW(config-pmap)# exit
The fail-close is needed as per instructions that if the CX module fails, no traffic should be allowed. The auth-proxy keyword is needed for active authentication.
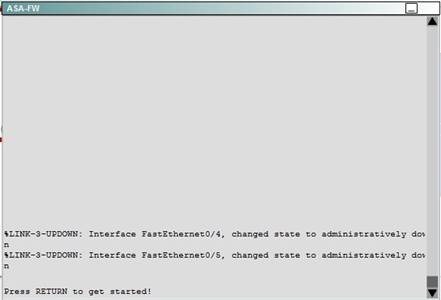
Next, we need to apply this policy map to the inside interface: ASA-FW(config)#service-policy inside-policy interface inside. Finally, verify that the policy is active:
ASA-FW# show service-policy interface inside Interface inside:
Service-policy: inside-policy Class-map: class-default
Default QueueingCXSC: card status Up, mode fail-close, auth-proxy enabled Packet input 181, packet output 183, drop 0, reset-drop 0, proxied 0 Configuration guidelines can be found at this reference link:
Reference:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa84/configuration/guide/asa_84_cli_config/modules_cx.pdf
NEW QUESTION 27
Which five system management protocols are supported by the Intrusion Prevention System? (Choose five.)
Answer: ABCFG
NEW QUESTION 28
In the predefined URL category filtering configuration page in a cisco WSA, which two actions are valid?
Answer: AD
NEW QUESTION 29
Which three functions can Cisco Application Visibility and Control perform? (Choose three.)
Answer: BDE
NEW QUESTION 30
What access control action will analyze the traffic as it passes through the device?
Answer: C
NEW QUESTION 31
......
Thanks for reading the newest 300-210 exam dumps! We recommend you to try the PREMIUM Passcertsure 300-210 dumps in VCE and PDF here: https://www.passcertsure.com/300-210-test/ (481 Q&As Dumps)