
Exam Code: 300-375 (), Exam Name: Securing Cisco Wireless Enterprise Networks, Certification Provider: Cisco Certifitcation, Free Today! Guaranteed Training- Pass 300-375 Exam.
Online Cisco 300-375 free dumps demo Below:
NEW QUESTION 1
When you configure BYOD access to the network, you face increased security risks and challenges. Which challenge is resolved by deploying digital client certificates?
Answer: D
Explanation:
NEW QUESTION 2
Refer to the exhibit.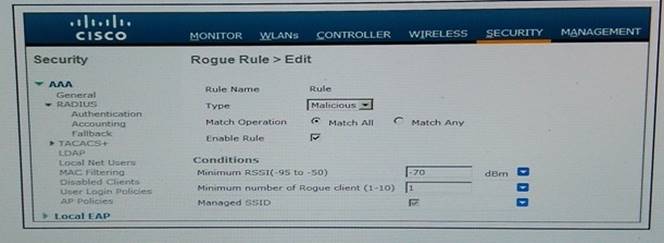
A WLAN with the SSID "Enterprise" is configured. Which rogue is marked as malicious?
Answer: C
Explanation:
NEW QUESTION 3
An engineer is configuring a BYOD deployment strategy and prefers a single SSID model. Which technology is required to accomplish this configuration?
Answer: C
Explanation:
NEW QUESTION 4
Which method does a Cisco switch use to authenticate a Cisco lightweight access point that is acting as a 802.1x supplicant?
Answer: B
Explanation:
NEW QUESTION 5
A network engineer is implementing a wireless network and is considering deploying a single SSID for device onboarding. Winch option is a benefit of using dual SSIDs with a captive portal on the onboard SSID compared to a single SSID solution?
Answer: B
Explanation:
NEW QUESTION 6
Which three WLAN polices can be controlled by using the Cisco IBNS on the Cisco WLC and Cisco Secure ACS? (Choose three.)
Answer: ABD
Explanation:
NEW QUESTION 7
Refer to the exhibit. What do the red circles represent in the exhibit?
Answer: C
Explanation:
NEW QUESTION 8
An engineer is trying to determine if an existing configuration deviates from the Cisco defaults while enabling PMF on a WLAN. Which set represents the default timer configuration for PMF?
Answer: D
Explanation:
NEW QUESTION 9
WPA2 Enterprise with 802.1x is being used for clients to authenticate to a wireless network through
an ACS server. For security reasons, the network engineer wants to ensure only PEAP authentication can be used. The engineer sent instructions to clients on how to configure their supplicants, but users are still in the ACS logs authentication using EAP-FAST. Which option describes the most efficient way the engineer can ensure these users cannot access the network unless the correct authentication mechanism is configured?
Answer: D
Explanation:
NEW QUESTION 10
Refer to the exhibit.
A customer is having problems with clients associating to me wireless network. Based on the configuration, which option describes the most likely cause of the issue?
Answer: E
Explanation:
NEW QUESTION 11
You are configuring the social login for a guest network. Which three options are configurable social connect in Cisco CMS visitor connect? (Choose three.)
Answer: ADE
Explanation:
NEW QUESTION 12
A company is deploying wireless PCs on forklifts within its new 10,000-square-foot (3048-squaremeter) facility. The clients are configured for PEAP-MS-CHAPv2 with WPA TKIP. Users report that applications frequently drop when the clients roam between access points on the floor. A
professional site survey was completed. Which configuration change is recommended to improve the speed of client roaming?
Answer: D
Explanation:
Although the controller and APs support WLAN with SSID using WiFi Protected Access (WPA) and WPA2 simultaneously, it is common that some wireless client drivers cannot handle complex SSID settings. Whenever possible, Cisco recommends WPA2 only with Advanced Encryption Standard (AES). However, due to standards and mandatory WiFi Alliance certification process, TKIP support is required across future software versions. Keep the security policies simple for any SSID. Use a separate WLAN/SSID with WPA and Temporal Key Integrity Protocol (TKIP), and a separate one with WPA2 and Advanced Encryption Standard (AES). Since TKIP is being deprecated, Cisco recommends to use TKIP together with WEP, or to migrate out of TKIP completely and use PEAP, if possible.
NEW QUESTION 13
A customer wants the access points in the CEO’s office to have different usernames and passwords for administrative support than the other access points deployed throughout the facility. Which feature can be enabled on the WLC and access points to achieve this criteria?
Answer: D
Explanation:
You can configure administrator usernames and passwords to prevent unauthorized users from reconfiguring the switch and viewing configuration information. This section provides instructions for initial configuration and for password recovery.
You can also set administrator usernames and passwords to manage and configure one or more access points that are associated with the switch. https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3650/software/release/16-1/configuration_guide/b_161_consolidated_3650_cg/b_161_consolidated_3650_cg_chapter_01010 111.pdf
NEW QUESTION 14
802.1X AP supplicant credentials have been enabled and configured on a Cisco WLC v7.0 in both the respective Wireless>AP>Global Configuration location and AP>Credentials tab locations. What describes the 802.1X AP authentication process when connected via Ethernet to a switch?
Answer: B
Explanation:
NEW QUESTION 15
An engineer configures the wireless LAN controller to perform 802.1x user authentication. Which option must be enabled to ensure that client devices can connect to the wireless, even when WLC cannot communicate with the RADIUS?
Answer: A
Explanation:
NEW QUESTION 16
An engineer is implementing SNMP v3 on a Cisco 5700 Series WLC. Which three commands are the
minimum needed to configure SNMP v3? (Choose three.)
Answer: BCF
Explanation:
NEW QUESTION 17
Which two events are possible outcomes of a successful RF jamming attack? (Choose two.)
Answer: DE
Explanation:
NEW QUESTION 18
Refer to the exhibit. You are configuring an autonomous AP for 802.1x access to a wired infrastructure. What does the command do?
Answer: C
Explanation:
NEW QUESTION 19
A customer is concerned about DOS attacks from a neighboring facility. Which feature can be enabled to help alleviate these concerns and mitigate DOS attacks on a WLAN?
Answer: A
Explanation:
P.S. Easily pass 300-375 Exam with 124 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy 300-375 Dumps: https://www.2passeasy.com/dumps/300-375/ (124 New Questions)