
we provide Best Quality Cisco 300-375 free practice test which are the best for clearing 300-375 test, and to get certified by Cisco Securing Cisco Wireless Enterprise Networks. The 300-375 Questions & Answers covers all the knowledge points of the real 300-375 exam. Crack your Cisco 300-375 Exam with latest dumps, guaranteed!
NEW QUESTION 1
When a network engineer plans to implement the client MFP, which three settings should be supported by the client? (Choose three)
Answer: ACF
NEW QUESTION 2
An engineer is configuring an autonomous AP for RADIUS authentication. What two pieces of information must be known to configure the AP? (Choose two.)
Answer: AC
Explanation:
You identify RADIUS security servers by their host name or IP address, host name and specific UDP port numbers, or their IP address and specific UDP port numbers. The combination of the IP address and the UDP port number creates a unique identifier allowing different ports to be individually defined as RADIUS hosts providing a specific AAA service. This unique identifier enables RADIUS requests to be sent to multiple UDP ports on a server at the same IP address. https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_rad/configuration/xe-3se/3850/secusr- rad-xe-3se-3850-book/sec-rad-mult-udp-ports.html
NEW QUESTION 3
Which three options are valid client profile probes m Cisco ISE? (Choose three.)
Answer: ADF
NEW QUESTION 4
An engineer is configuring a new mobility anchor for a WLAN on the CLI with the config wlan mobility anchor add 3 10.10.10.10 command, but the command is failing. Which two conditions must be met to be able to enter this command? (Choose two.)
Answer: AB
NEW QUESTION 5
Which two statements describe the requirements for EAP-TLS?
Answer: AB
NEW QUESTION 6
A network engineer must segregate all iPads on the guest WLAN to a separate VLAN. How does the engineer accomplish this task without using ISE?
Answer: B
NEW QUESTION 7
Refer to the exhibit.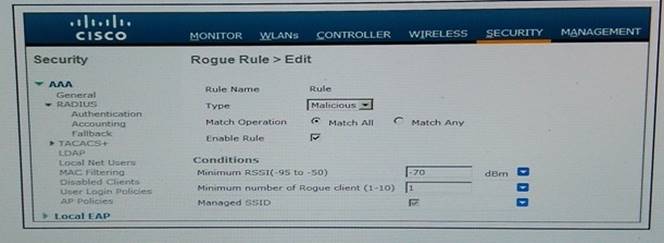
A WLAN with the SSID "Enterprise" is configured. Which rogue is marked as malicious?
Answer: C
NEW QUESTION 8
An engineer is adding APs to an existing VoWLAN to allow for location based services. Which option
will the primary change be to the network?
Answer: C
NEW QUESTION 9
An engineer configures 802.1 X authentication for the access points using the config ap 802.1Xuser add username admin password secret AP_01 command.
Which EAP method does the access point use to authenticate?
Answer: D
Explanation:
Enables or disables Extensible Authentication Protocol-Flexible Authentication via Secure Tunneling (EAP-FAST) authentication.
https://www.cisco.com/c/en/us/td/docs/wireless/controller/8-0/cmdref/b_cr80/config_commands_a_to_i.html
NEW QUESTION 10
After receiving an alert regarding a rogue AP, a network engineer logs into Cisco Prime and looks at the floor map where the AP that detected the rogue is located. The map is synchronized with a mobility services engine that determines the rogue device is actually inside the campus. The engineer determines the rogue to be a security threat and decides to stop it from broadcasting inside the enterprise wireless network. What is the fastest way to disable the rogue?
Answer: C
NEW QUESTION 11
An engineer with ID 338860948 is implementing Cisco Identity-Based Networking on a Cisco AireOS
controller. The engineer has two ACLs on the controller. The first ACL, named BASE_ACL, is applied to the corporate_clients interface on the WLC, which is used for all corporate clients. The second ACL, named HR_ACL, is referenced by ISE in the Human Resources group policy.
Which option is the resulting ACL when a Human Resources user connects?
Answer: A
NEW QUESTION 12
802.1X AP supplicant credentials have been enabled and configured on a Cisco WLC v7.0 in both the respective Wireless>AP>Global Configuration location and AP>Credentials tab locations. What describes the 802.1X AP authentication process when connected via Ethernet to a switch?
Answer: B
NEW QUESTION 13
Which attribute on the Cisco WLC v7.0 does RADIUS IETF attribute "Tunnel-Private-Group ID" assign?
Answer: D
NEW QUESTION 14
Which client roam is considered the fastest in a wireless deployment using Cisco IOS XE mobility controllers and mobility agents?
Answer: B
Explanation:
• Inter-SPG, Intra-subdomain roaming?The client roaming between mobility agents in different SPGs
within the same subdomain. https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3850/software/release/3se/system_m anagement/configuration_guide/b_sm_3se_3850_cg/b_sm_3se_3850_cg_chapter_0111.pdf
NEW QUESTION 15
An engineer configures the wireless LAN controller to perform 802.1x user authentication. Which option must be enabled to ensure that client devices can connect to the wireless, even when WLC cannot communicate with the RADIUS?
Answer: A
NEW QUESTION 16
When a supplicant and AAA server are configured to use PEAP, which mechanism is used by the client to authenticate the AAA server in Phase One?
Answer: C
NEW QUESTION 17
Which EAP method can an AP use to authenticate to the wired network?
Answer: C
NEW QUESTION 18
Regarding the guidelines for using MFP, under what circumstances will a client without Cisco compatible Extensions v5 be able to associate to a WLAN?
Answer: D
NEW QUESTION 19
When a wireless client uses WPA2 AES, which keys are created at the end of the four way handshake process between the client and the access point?
Answer: A
NEW QUESTION 20
An engineer has configured central web authentication on the wireless network, but clients are receiving untrusted certificate errors on their internet browsers when directed to the guest splash page. Which file must be provided to an approved trusted certificate authority to fix this issue?
Answer: B
NEW QUESTION 21
Which method does a Cisco switch use to authenticate a Cisco lightweight access point that is acting as a 802.1x supplicant?
Answer: B
NEW QUESTION 22
......
Recommend!! Get the Full 300-375 dumps in VCE and PDF From DumpSolutions, Welcome to Download: https://www.dumpsolutions.com/300-375-dumps/ (New 124 Q&As Version)