
Your success in Cisco 350-701 is our sole target and we develop all our 350-701 braindumps in a way that facilitates the attainment of this target. Not only is our 350-701 study material the best you can find, it is also the most detailed and the most updated. 350-701 Practice Exams for Cisco Cisco Other Exam 350-701 are written to the highest standards of technical accuracy.
Also have 350-701 free dumps questions for you:
NEW QUESTION 1
Which feature requires a network discovery policy on the Cisco Firepower Next Generation Intrusion Prevention System?
Answer: A
NEW QUESTION 2
What is the primary difference between an Endpoint Protection Platform and an Endpoint Detection and Response?
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/products/security/endpoint-security/what-is-endpoint-detection-response-edr.html
NEW QUESTION 3
Which two preventive measures are used to control cross-site scripting? (Choose two.)
Answer: AB
NEW QUESTION 4
Refer to the exhibit.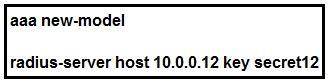
Which statement about the authentication protocol used in the configuration is true?
Answer: C
NEW QUESTION 5
Which solution protects hybrid cloud deployment workloads with application visibility and segmentation?
Answer: D
Explanation:
Reference: https://www.cisco.com/c/en/us/solutions/security/secure-data-center-solution/index.html#~products
NEW QUESTION 6
Which policy is used to capture host information on the Cisco Firepower Next Generation Intrusion Prevention System?
Answer: D
NEW QUESTION 7
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
Answer: D
NEW QUESTION 8
What is a language format designed to exchange threat intelligence that can be transported over the TAXII protocol?
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/web_security/scancenter/administrator/guide/b_ScanCenter_Administrator_Guide/b_ScanCenter_Administrator_Guide_chapter_0100011.pdf
NEW QUESTION 9
Which two probes are configured to gather attributes of connected endpoints using Cisco Identity Services Engine? (Choose two.)
Answer: AC
Explanation:
Reference: https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_prof_pol.html
NEW QUESTION 10
Which two descriptions of AES encryption are true? (Choose two.)
Answer: BD
Explanation:
Reference: https://gpdb.docs.pivotal.io/43190/admin_guide/topics/ipsec.html
NEW QUESTION 11
What two mechanisms are used to redirect users to a web portal to authenticate to ISE for guest services? (Choose two.)
Answer: BE
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/2-2/admin_guide/b_ise_admin_guide_22/b_ise_admin_guide_22_chapter_01110.html
NEW QUESTION 12
Which two capabilities does TAXII support? (Choose two.)
Answer: BC
NEW QUESTION 13
DRAG DROP
Drag and drop the capabilities from the left onto the correct technologies on the right.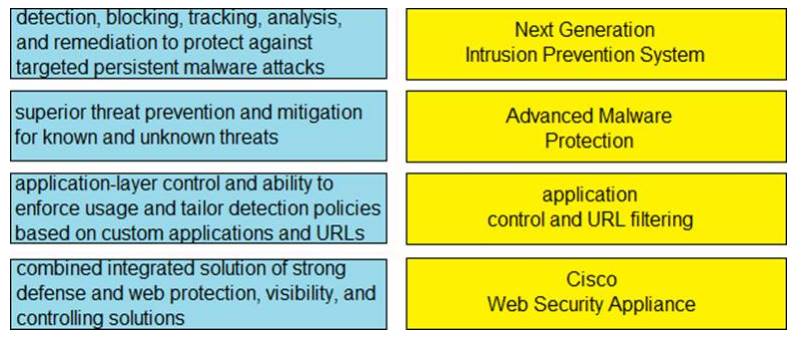
Answer: A
Explanation: 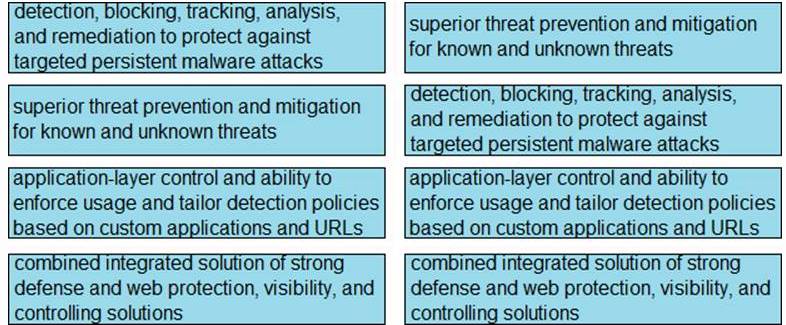
NEW QUESTION 14
How does Cisco Umbrella archive logs to an enterprise- owned storage?
Answer: D
Explanation:
Reference: https://docs.umbrella.com/deployment-umbrella/docs/log-management
NEW QUESTION 15
Which policy represents a shared set of features or parameters that define the aspects of a managed device that are likely to be similar to other managed devices in a deployment?
Answer: D
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/622/configuration/guide/fpmc-config-guide-v622/platform_settings_policies_for_managed_devices.pdf
NEW QUESTION 16
What are the two most commonly used authentication factors in multifactor authentication? (Choose two.)
Answer: AD
NEW QUESTION 17
Which technology must be used to implement secure VPN connectivity among company branches over a private IP cloud with any-to-any scalable connectivity?
Answer: D
NEW QUESTION 18
Which technology reduces data loss by identifying sensitive information stored in public computing environments?
Answer: D
Explanation:
Reference: https://www.cisco.com/c/dam/en/us/products/collateral/security/cloudlock/cisco-cloudlock-cloud-data-security-datasheet.pdf
NEW QUESTION 19
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
Answer: C
NEW QUESTION 20
How is Cisco Umbrella configured to log only security events?
Answer: A
Explanation:
Reference: https://docs.umbrella.com/deployment-umbrella/docs/log-management
NEW QUESTION 21
......
100% Valid and Newest Version 350-701 Questions & Answers shared by Dumpscollection, Get Full Dumps HERE: http://www.dumpscollection.net/dumps/350-701/ (New 102 Q&As)