
It is more faster and easier to pass the Cisco 350-701 exam by using Verified Cisco Implementing and Operating Cisco Security Core Technologies questuins and answers. Immediate access to the Most recent 350-701 Exam and find the same core area 350-701 questions with professionally verified answers, then PASS your exam with a high score now.
Free 350-701 Demo Online For Cisco Certifitcation:
NEW QUESTION 1
Which information is required when adding a device to Firepower Management Center?
Answer: D
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config-guide-v60/Device_Management_Basics.html#ID-2242-0000069d
NEW QUESTION 2
DRAG DROP
Drag and drop the Firepower Next Generation Intrustion Prevention System detectors from the left onto the correct definitions on the right.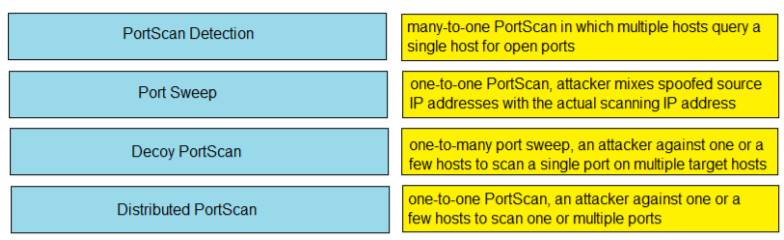
Answer: A
NEW QUESTION 3
Which Cisco product provides proactive endpoint protection and allows administrators to centrally manage the deployment?
Answer: B
NEW QUESTION 4
Which two prevention techniques are used to mitigate SQL injection attacks? (Choose two.)
Answer: AB
Explanation:
Reference: https://en.wikipedia.org/wiki/SQL_injection
NEW QUESTION 5
Which technology must be used to implement secure VPN connectivity among company branches over a private IP cloud with any-to-any scalable connectivity?
Answer: D
NEW QUESTION 6
Which feature within Cisco Umbrella allows for the ability to inspect secure HTTP traffic?
Answer: C
NEW QUESTION 7
When web policies are configured in Cisco Umbrella, what provides the ability to ensure that domains are blocked when they host malware, command and control, phishing, and more threats?
Answer: B
Explanation:
Reference: https://support.umbrella.com/hc/en-us/articles/115004563666-Understanding-Security-Categories
NEW QUESTION 8
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two.)
Answer: DE
Explanation:
Reference: https://www.cisco.com/c/dam/en/us/td/docs/security/ces/overview_guide/Cisco_Cloud_Hybrid_Email_Security_Overview_Guide.pdf
NEW QUESTION 9
Which two application layer preprocessors are used by Firepower Next Generation Intrusion Prevention System? (Choose two.)
Answer: AC
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config-guide-v60/Application_Layer_Preprocessors.html
NEW QUESTION 10
An engineer configured a new network identity in Cisco Umbrella but must verify that traffic is being routed through the Cisco Umbrella network. Which action tests the routing?
Answer: B
NEW QUESTION 11
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/117940-qa-wsa-00.html
NEW QUESTION 12
Which Talos reputation center allows you to track the reputation of IP addresses for email and web traffic?
Answer: D
NEW QUESTION 13
What does the Cloudlock Apps Firewall do to mitigate security concerns from an application perspective?
Answer: B
Explanation:
Reference: https://www.cisco.com/c/en/us/products/security/cloudlock/index.html#~features
NEW QUESTION 14
Which technology reduces data loss by identifying sensitive information stored in public computing environments?
Answer: D
Explanation:
Reference: https://www.cisco.com/c/dam/en/us/products/collateral/security/cloudlock/cisco-cloudlock-cloud-data-security-datasheet.pdf
NEW QUESTION 15
An engineer is configuring AMP for endpoints and wants to block certain files from executing. Which outbreak control method is used to accomplish this task?
Answer: C
NEW QUESTION 16
......
P.S. Easily pass 350-701 Exam with 337 Q&As Dumps-hub.com Dumps & pdf Version, Welcome to Download the Newest Dumps-hub.com 350-701 Dumps: https://www.dumps-hub.com/350-701-dumps.html (337 New Questions)