
It is more faster and easier to pass the by using . Immediate access to the and find the same core area with professionally verified answers, then PASS your exam with a high score now.
Also have 412-79v10 free dumps questions for you:
NEW QUESTION 1
Which of the following documents helps in creating a confidential relationship between the pen tester and client to protect critical and confidential information or trade secrets?
Answer: D
NEW QUESTION 2
Rule of Engagement (ROE) is the formal permission to conduct a pen-test. It provides top-level guidance for conducting the penetration testing. Various factors are considered while preparing the scope of ROE which clearly explain the limits associated with the security test.
Which of the following factors is NOT considered while preparing the scope of the Rules of Engagment (ROE)?
Answer: A
NEW QUESTION 3
How many bits is Source Port Number in TCP Header packet?
Answer: D
NEW QUESTION 4
An "idle" system is also referred to as what?
Answer: A
NEW QUESTION 5
Which of the following is the range for assigned ports managed by the Internet Assigned Numbers Authority (IANA)?
Answer: D
NEW QUESTION 6
You work as an IT security auditor hired by a law firm in Boston. You have been assigned the responsibility to audit the client for security risks. When assessing the risk to the clients network, what step should you take first?
Answer: C
NEW QUESTION 7
Which of the following are the default ports used by NetBIOS service?
Answer: A
NEW QUESTION 8
Choose the correct option to define the Prefix Length.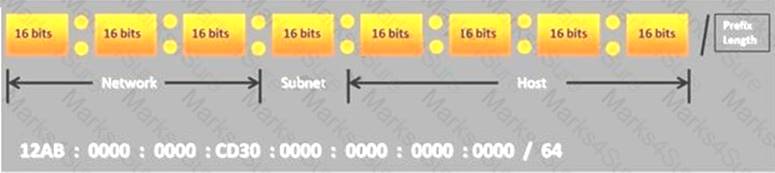
Answer: C
NEW QUESTION 9
What does ICMP Type 3/Code 13 mean?
Answer: D
NEW QUESTION 10
Which of the following is not a characteristic of a firewall?
Answer: D
NEW QUESTION 11
Jessica works as systems administrator for a large electronics firm. She wants to scan her network quickly to detect live hosts by using ICMP ECHO Requests. What type of scan is Jessica going to perform?
Answer: D
NEW QUESTION 12
During the process of fingerprinting a web application environment, what do you need to do in order to analyze HTTP and HTTPS request headers and the HTML source code?
Answer: D
NEW QUESTION 13
John, the penetration testing manager in a pen testing firm, needs to prepare a pen testing pricing report for a client. Which of the following factors does he need to consider while preparing the pen testing pricing report?
Answer: C
NEW QUESTION 14
Which of the following statements is true about the LM hash?
Answer: A
NEW QUESTION 15
Which of the following policies states that the relevant application owner must authorize requests for additional access to specific business applications in writing to the IT Department/resource?
Answer: B
NEW QUESTION 16
The Web parameter tampering attack is based on the manipulation of parameters exchanged between client and server in order to modify application data, such as user credentials and permissions, price and quantity of products, etc.
Usually, this information is stored in cookies, hidden form fields, or URL Query Strings, and is used to increase application functionality and control. This attack takes advantage of the fact that many programmers rely on hidden or fixed fields (such as a hidden tag in a form or a parameter in a URL) as the only security measure for certain operations.
Attackers can easily modify these parameters to bypass the security mechanisms that rely on them.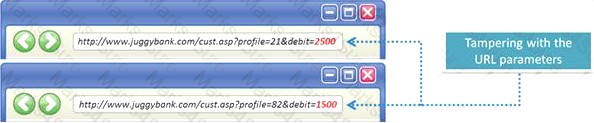
What is the best way to protect web applications from parameter tampering attacks?
Answer: D
P.S. Certifytools now are offering 100% pass ensure 412-79v10 dumps! All 412-79v10 exam questions have been updated with correct answers: https://www.certifytools.com/412-79v10-exam.html (201 New Questions)