
Proper study guides for 412-79v10 EC-Council Certified Security Analyst (ECSA) V10 certified begins with preparation products which designed to deliver the by making you pass the 412-79v10 test at your first time. Try the free right now.
Also have 412-79v10 free dumps questions for you:
NEW QUESTION 1
In the TCP/IP model, the transport layer is responsible for reliability and flow control from source to the destination. TCP provides the mechanism for flow control by allowing the sending and receiving hosts to communicate.
A flow control mechanism avoids the problem with a transmitting host overflowing the buffers in the receiving host.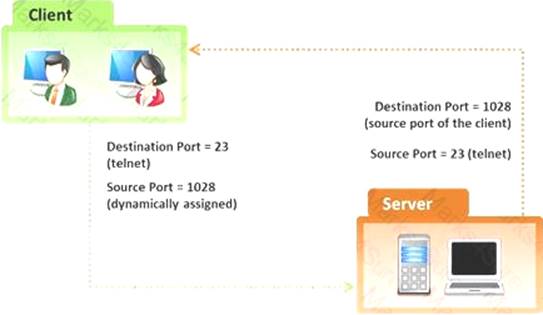
Answer: C
NEW QUESTION 2
Harold is a web designer who has completed a website for ghttech.net. As part of the maintenance agreement he signed with the client, Harold is performing research online and seeing how much exposure the site has received so far. Harold navigates to google.com and types in the following search. link:www.ghttech.net
What will this search produce?
Answer: A
NEW QUESTION 3
What are placeholders (or markers) in an HTML document that the web server will dynamically replace with data just before sending the requested documents to a browser?
Answer: A
NEW QUESTION 4
What will the following URL produce in an unpatched IIS Web Server?
Answer: D
NEW QUESTION 5
A chipset is a group of integrated circuits that are designed to work together and are usually marketed as a single product.” It is generally the motherboard chips or the chips used on the expansion card.
Which one of the following is well supported in most wireless applications?
Answer: B
NEW QUESTION 6
Simon is a former employee of Trinitron XML Inc. He feels he was wrongly terminated and wants to hack into his former company's network. Since Simon remembers some of the server names, he attempts to run the AXFR and IXFR commands using DIG. What is Simon trying to accomplish here?
Answer: D
NEW QUESTION 7
Vulnerability assessment is an examination of the ability of a system or application, including current security procedures and controls, to withstand assault. It recognizes, measures, and classifies security vulnerabilities in a computer system, network, and communication channels.
A vulnerability assessment is used to identify weaknesses that could be exploited and predict the effectiveness of additional security measures in protecting information resources from attack.
Which of the following vulnerability assessment technique is used to test the web server infrastructure for any misconfiguration and outdated content?
Answer: D
NEW QUESTION 8
A framework is a fundamental structure used to support and resolve complex issues. The framework that delivers an efficient set of technologies in order to develop applications which are more secure in using Internet and Intranet is:
Answer: A
NEW QUESTION 9
Besides the policy implications of chat rooms, Internet Relay Chat (IRC) is frequented by attackers and used as a command and control mechanism. IRC normally uses which one of the following TCP ports?
Answer: C
NEW QUESTION 10
Wireless communication allows networks to extend to places that might otherwise go untouched by the wired networks. When most people say ‘Wireless’ these days, they are referring to one of the 802.11 standards. There are three main 802.11 standards: B, A, and G.
Which one of the following 802.11 types uses DSSS Modulation, splitting the 2.4ghz band into channels?
Answer: A
NEW QUESTION 11
In Linux, /etc/shadow file stores the real password in encrypted format for user’s account with added properties associated with the user’s password.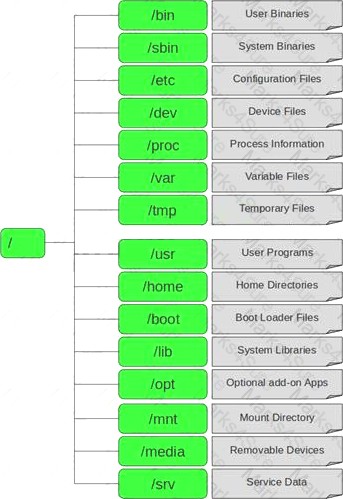
In the example of a /etc/shadow file below, what does the bold letter string indicate?
Vivek: $1$fnffc$GteyHdicpGOfffXX40w#5:13064:0:99999:7
Answer: B
NEW QUESTION 12
Vulnerability assessment is an examination of the ability of a system or application, including the current security procedures and controls, to withstand assault.
What does a vulnerability assessment identify?
Answer: B
NEW QUESTION 13
Which of the following will not handle routing protocols properly?
Answer: B
NEW QUESTION 14
Hackers today have an ever-increasing list of weaknesses in the web application structure at their disposal, which they can exploit to accomplish a wide variety of malicious tasks.
New flaws in web application security measures are constantly being researched, both by hackers and by security professionals. Most of these flaws affect all dynamic web applications whilst others are dependent on specific application technologies.
In both cases, one may observe how the evolution and refinement of web technologies also brings about new exploits which compromise sensitive databases, provide access to theoretically secure networks, and pose a threat to the daily operation of online businesses.
What is the biggest threat to Web 2.0 technologies?
Answer: A
NEW QUESTION 15
You are trying to locate Microsoft Outlook Web Access Default Portal using Google search on the Internet. What search string will you use to locate them?
Answer: D
NEW QUESTION 16
Information gathering is performed to:
i) Collect basic information about the target company and its network
ii) Determine the operating system used, platforms running, web server versions, etc.
iii) Find vulnerabilities and exploits
Which of the following pen testing tests yields information about a company’s technology infrastructure?
Answer: D
100% Valid and Newest Version 412-79v10 Questions & Answers shared by Exambible, Get Full Dumps HERE: https://www.exambible.com/412-79v10-exam/ (New 201 Q&As)