
We provide in two formats. Download PDF & Practice Tests. Pass EC-Council 412-79v10 Exam quickly & easily. The 412-79v10 PDF type is available for reading and printing. You can print more and practice many times. With the help of our product and material, you can easily pass the 412-79v10 exam.
Check 412-79v10 free dumps before getting the full version:
NEW QUESTION 1
Which of the following equipment could a pen tester use to perform shoulder surfing?
Answer: A
NEW QUESTION 2
What are the security risks of running a "repair" installation for Windows XP?
Answer: D
NEW QUESTION 3
ARP spoofing is a technique whereby an attacker sends fake ("spoofed") Address Resolution Protocol (ARP) messages onto a Local Area Network. Generally, the aim is to associate the attacker's MAC address with the IP address of another host (such as the default gateway), causing any traffic meant for that IP address to be sent to the attacker instead.
ARP spoofing attack is used as an opening for other attacks.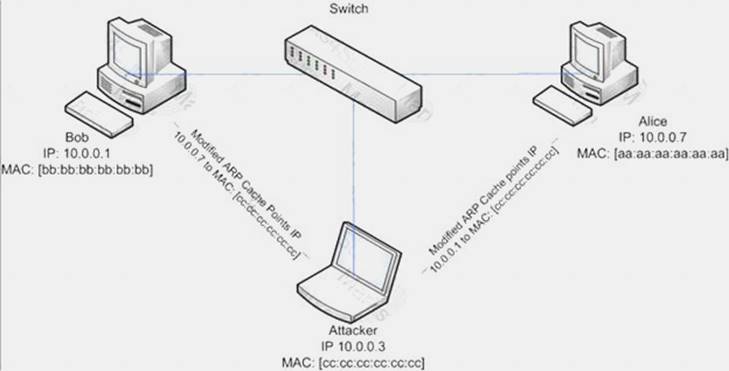
What type of attack would you launch after successfully deploying ARP spoofing?
Answer: D
NEW QUESTION 4
Which of the following is a framework of open standards developed by the Internet Engineering Task Force (IETF) that provides secure transmission of the sensitive data over an unprotected medium, such as the Internet?
Answer: D
NEW QUESTION 5
An automated electronic mail message from a mail system which indicates that the user does not exist on that server is called as?
Answer: D
NEW QUESTION 6
By default, the TFTP server listens on UDP port 69. Which of the following utility reports the port status of target TCP and UDP ports on a local or a remote computer and is used to troubleshoot TCP/IP connectivity issues?
Answer: A
NEW QUESTION 7
You are running through a series of tests on your network to check for any security vulnerabilities. After normal working hours, you initiate a DoS attack against your external firewall. The firewall quickly freezes up and becomes unusable.
You then initiate an FTP connection from an external IP into your internal network. The connection is successful even though you have FTP blocked at the external firewall. What has happened?
Answer: A
NEW QUESTION 8
Which one of the following acts related to the information security in the US fix the responsibility of management for establishing and maintaining an adequate internal control structure and procedures for financial reporting?
Answer: B
NEW QUESTION 9
Logs are the record of the system and network activities. Syslog protocol is used for delivering log information across an IP network. Syslog messages can be sent via which one of the following?
Answer: A
NEW QUESTION 10
The first and foremost step for a penetration test is information gathering. The main objective of this test is to gather information about the target system which can be used in a malicious manner to gain access to the target systems.
Which of the following information gathering terminologies refers to gathering information through social engineering on-site visits, face-to-face interviews, and direct questionnaires?
Answer: A
NEW QUESTION 11
What is the target host IP in the following command?
Answer: A
NEW QUESTION 12
In Linux, what is the smallest possible shellcode?
Answer: D
NEW QUESTION 13
What are the 6 core concepts in IT security?
Answer: B
NEW QUESTION 14
Which of the following reports provides a summary of the complete pen testing process, its outcomes, and recommendations?
Answer: B
NEW QUESTION 15
You just passed your ECSA exam and are about to start your first consulting job running security audits for a financial institution in Los Angeles. The IT manager of the company you will be working for tries to see if you remember your ECSA class. He asks about the methodology you will be using to test the company's network.
How would you answer?
Answer: B
NEW QUESTION 16
Which of the following is not the SQL injection attack character?
Answer: A
P.S. Exambible now are offering 100% pass ensure 412-79v10 dumps! All 412-79v10 exam questions have been updated with correct answers: https://www.exambible.com/412-79v10-exam/ (201 New Questions)