
It is more faster and easier to pass the by using . Immediate access to the and find the same core area with professionally verified answers, then PASS your exam with a high score now.
Online 412-79v10 free questions and answers of New Version:
NEW QUESTION 1
You have compromised a lower-level administrator account on an Active Directory network of a small company in Dallas, Texas. You discover Domain Controllers through enumeration. You connect to one of the Domain Controllers on port 389 using Idp.exe.
What are you trying to accomplish here?
Answer: D
NEW QUESTION 2
Michael works for Kimball Construction Company as senior security analyst. As part of yearly security audit, Michael scans his network for vulnerabilities. Using Nmap, Michael conducts XMAS scan and most of the ports scanned do not give a response. In what state are these ports?
Answer: D
NEW QUESTION 3
A pen tester has extracted a database name by using a blind SQL injection. Now he begins to test the table inside the database using the below query and finds the table:
http://juggyboy.com/page.aspx?id=1; IF (LEN(SELECT TOP 1 NAME from sysobjects where xtype='U')=3) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),1,1)))=101) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),2,1)))=109) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((SELECT TOP 1 NAME from sysobjects where xtype=char(85)),3,1)))=112) WAITFOR DELAY '00:00:10'—
What is the table name?
Answer: C
NEW QUESTION 4
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast.
On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away. Eventually the wireless signal shows back up, but drops intermittently.
What could be Tyler issue with his home wireless network?
Answer: A
NEW QUESTION 5
Identify the injection attack represented in the diagram below: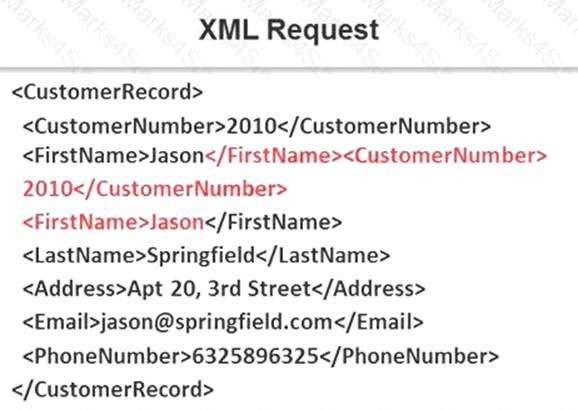
Answer: C
NEW QUESTION 6
How many possible sequence number combinations are there in TCP/IP protocol?
Answer: C
NEW QUESTION 7
What is a good security method to prevent unauthorized users from "tailgating"?
Answer: B
NEW QUESTION 8
Which of the following has an offset field that specifies the length of the header and data?
Answer: D
NEW QUESTION 9
Wireshark is a network analyzer. It reads packets from the network, decodes them, and presents them in an easy-to-understand format. Which one of the following is the command-line version of Wireshark, which can be used to capture the live packets from the wire or to read the saved capture files?
Answer: B
NEW QUESTION 10
Identify the port numbers used by POP3 and POP3S protocols.
Answer: C
NEW QUESTION 11
Which of the following policy forbids everything with strict restrictions on all usage of the company systems and network?
Answer: B
NEW QUESTION 12
Which one of the following is a command line tool used for capturing data from the live network and copying those packets to a file?
Answer: D
NEW QUESTION 13
Amazon, an IT based company, conducts a survey on the usage of the Internet. They found that company employees spend most of the time at work surfing the web for their personal use and for inappropriate web site viewing. Management decide to block all such web sites using URL filtering software.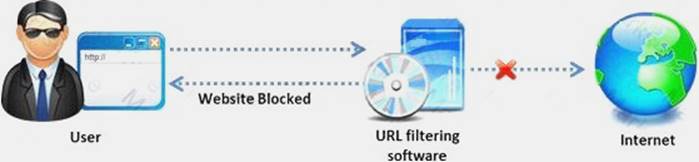
How can employees continue to see the blocked websites?
Answer: B
NEW QUESTION 14
Which of the following is the objective of Gramm-Leach-Bliley Act?
Answer: A
NEW QUESTION 15
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the authentication procedures. Creating a backdoor is a where an attacker obtains remote access to a computer on a network.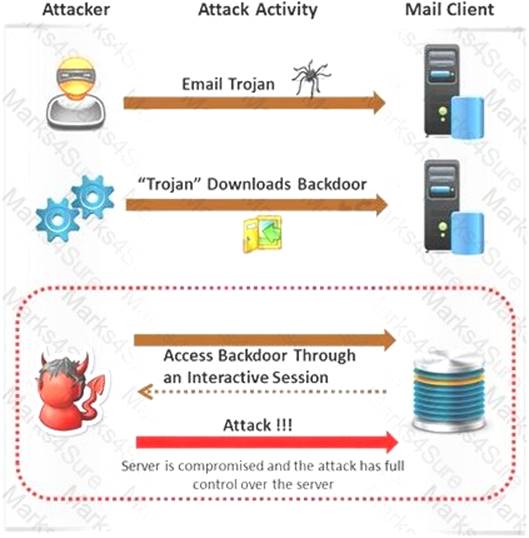
Which of the following techniques do attackers use to create backdoors to covertly gather critical information about a target machine?
Answer: D
NEW QUESTION 16
Windows stores user passwords in the Security Accounts Manager database (SAM), or in the Active Directory database in domains. Passwords are never stored in clear text; passwords are hashed and the results are stored in the SAM.
NTLM and LM authentication protocols are used to securely store a user's password in the SAM database using different hashing methods.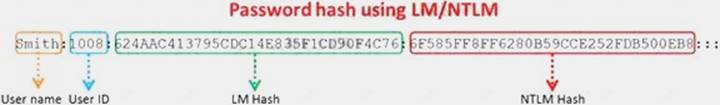
The SAM file in Windows Server 2008 is located in which of the following locations?
Answer: D
100% Valid and Newest Version 412-79v10 Questions & Answers shared by Passcertsure, Get Full Dumps HERE: https://www.passcertsure.com/412-79v10-test/ (New 201 Q&As)