
Want to know features? Want to lear more about experience? Study . Gat a success with an absolute guarantee to pass EC-Council 412-79v10 (EC-Council Certified Security Analyst (ECSA) V10) test on your first attempt.
Also have 412-79v10 free dumps questions for you:
NEW QUESTION 1
Transmission control protocol accepts data from a data stream, divides it into chunks, and adds a TCP header creating a TCP segment. The TCP header is the first 24 bytes of a TCP segment that contains the parameters and state of an end-to-end TCP socket. It is used to track the state of communication between two TCP endpoints.
For a connection to be established or initialized, the two hosts must synchronize. The synchronization requires each side to send its own initial sequence number and to receive a confirmation of exchange in an acknowledgment (ACK) from the other side
The below diagram shows the TCP Header format: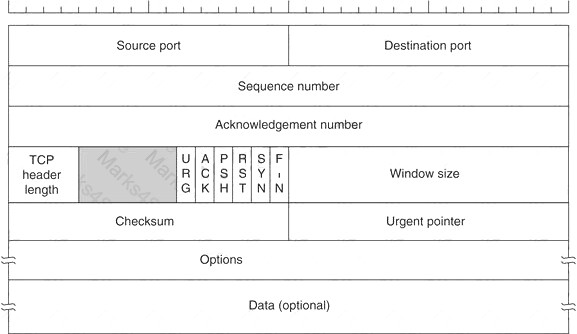
Answer: B
NEW QUESTION 2
Which one of the following is a useful formatting token that takes an int * as an argument, and writes the number of bytes already written, to that location?
Answer: A
NEW QUESTION 3
The term social engineering is used to describe the various tricks used to fool people (employees, business partners, or customers) into voluntarily giving away information that would not normally be known to the general public.
What is the criminal practice of social engineering where an attacker uses the telephone system in an attempt to scam the user into surrendering private information?
Answer: D
NEW QUESTION 4
You are the security analyst working for a private company out of France. Your current assignment is to obtain credit card information from a Swiss bank owned by that company. After initial reconnaissance, you discover that the bank security defenses are very strong and would take too long to penetrate. You decide to get the information by monitoring the traffic between the bank and one of its subsidiaries in London.
After monitoring some of the traffic, you see a lot of FTP packets traveling back and forth. You want to sniff the traffic and extract usernames and passwords. What tool could you use to get this information?
Answer: C
NEW QUESTION 5
Metasploit framework in an open source platform for vulnerability research, development, and penetration testing. Which one of the following metasploit options is used to exploit multiple systems at once?
Answer: A
NEW QUESTION 6
Which of the following statements is true about Multi-Layer Intrusion Detection Systems (mIDSs)?
Answer: A
NEW QUESTION 7
Variables are used to define parameters for detection, specifically those of your local network and/or specific servers or ports for inclusion or exclusion in rules. These are simple substitution variables set with the var keyword.
Which one of the following operator is used to define meta-variables?
Answer: A
NEW QUESTION 8
Which of the following statement holds true for TCP Operation?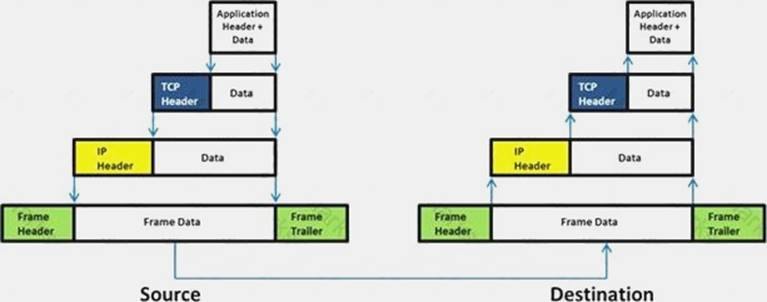
Answer: D
NEW QUESTION 9
SQL injection attacks are becoming significantly more popular amongst hackers and there has been an estimated 69 percent increase of this attack type.
This exploit is used to great effect by the hacking community since it is the primary way to steal sensitive data from web applications. It takes advantage of non-validated input vulnerabilities to pass SQL commands through a web application for execution by a back-end database.
The below diagram shows how attackers launched SQL injection attacks on web applications.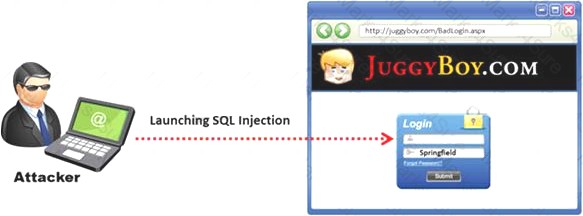
Which of the following can the attacker use to launch an SQL injection attack?
Answer: D
NEW QUESTION 10
In the process of hacking a web application, attackers manipulate the HTTP requests to subvert the application authorization schemes by modifying input fields that relate to the user ID, username, access group, cost, file names, file identifiers, etc.
They first access the web application using a low privileged account and then escalate privileges to access protected resources. What attack has been carried out?
Answer: B
NEW QUESTION 11
Harold is a security analyst who has just run the rdisk /s command to grab the backup SAM file on a computer. Where should Harold navigate on the computer to find the file?
Answer: B
NEW QUESTION 12
Snort, an open source network-based intrusion detection sensor, is the most widely installed NIDS in the world. It can be configured to run in the four modes. Which one of the following modes reads the packets off the network and displays them in a continuous stream on the console (screen)?
Answer: A
NEW QUESTION 13
Paulette works for an IT security consulting company that is currently performing an audit for the firm
ACE Unlimited. Paulette's duties include logging on to all the company's network equipment to ensure IOS versions are up-to-date and all the other security settings are as stringent as possible.
Paulette presents the following screenshot to her boss so he can inform the clients about necessary changes need to be made. From the screenshot, what changes should the client company make?
Exhibit:
Answer: B
NEW QUESTION 14
You are running known exploits against your network to test for possible vulnerabilities. To test the strength of your virus software, you load a test network to mimic your production network. Your software successfully blocks some simple macro and encrypted viruses.
You decide to really test the software by using virus code where the code rewrites itself entirely and the signatures change from child to child, but the functionality stays the same. What type of virus is this that you are testing?
Answer: A
NEW QUESTION 15
Which type of vulnerability assessment tool provides security to the IT system by testing for vulnerabilities in the applications and operation system?
Answer: D
NEW QUESTION 16
Which of the following attributes has a LM and NTLMv1 value as 64bit + 64bit + 64bit and NTLMv2 value as 128 bits?
Answer: B
Recommend!! Get the Full 412-79v10 dumps in VCE and PDF From Surepassexam, Welcome to Download: https://www.surepassexam.com/412-79v10-exam-dumps.html (New 201 Q&As Version)