
It is impossible to pass EC-Council 412-79v10 exam without any help in the short term. Come to us soon and find the most advanced, correct and guaranteed . You will get a surprising result by our .
Online 412-79v10 free questions and answers of New Version:
NEW QUESTION 1
Which vulnerability assessment phase describes the scope of the assessment, identifies and ranks the critical assets, and creates proper information protection procedures such as effective planning, scheduling, coordination, and logistics?
Answer: B
NEW QUESTION 2
An attacker injects malicious query strings in user input fields to bypass web service authentication mechanisms and to access back-end databases. Which of the following attacks is this?
Answer: D
NEW QUESTION 3
Identify the framework that comprises of five levels to guide agency assessment of their security programs and assist in prioritizing efforts for improvement:
Answer: D
NEW QUESTION 4
SQL injection attack consists of insertion or "injection" of either a partial or complete SQL query via the data input or transmitted from the client (browser) to the web application. A successful SQL injection attack can:
i) Read sensitive data from the database
iii) Modify database data (insert/update/delete)
iii) Execute administration operations on the database (such as shutdown the DBMS)
iV) Recover the content of a given file existing on the DBMS file system or write files into the file system
v) Issue commands to the operating system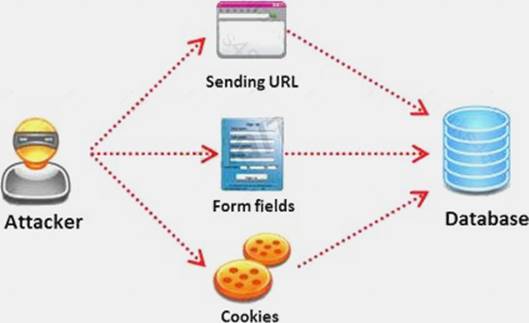
Pen tester needs to perform various tests to detect SQL injection vulnerability. He has to make a list of all input fields whose values could be used in crafting a SQL query, including the hidden fields of POST requests and then test them separately, trying to interfere with the query and to generate an error.
In which of the following tests is the source code of the application tested in a non-runtime environment to detect the SQL injection vulnerabilities?
Answer: D
NEW QUESTION 5
Rules of Engagement (ROE) document provides certain rights and restriction to the test team for performing the test and helps testers to overcome legal, federal, and policy-related restrictions to use different penetration testing tools and techniques.
What is the last step in preparing a Rules of Engagement (ROE) document?
Answer: C
NEW QUESTION 6
DNS information records provide important data about:
Answer: B
NEW QUESTION 7
Which one of the following acts makes reputational risk of poor security a reality because it requires public disclosure of any security breach that involves personal information if it is unencrypted or if it is reasonably believed that the information has been acquired by an unauthorized person?
Answer: A
NEW QUESTION 8
Which one of the following Snort logger mode commands is associated to run a binary log file through Snort in sniffer mode to dump the packets to the screen?
Answer: C
NEW QUESTION 9
An antenna is a device that is designed to transmit and receive the electromagnetic waves that are generally called radio waves. Which one of the following types of antenna is developed from waveguide technology?
Answer: B
NEW QUESTION 10
A Demilitarized Zone (DMZ) is a computer host or small network inserted as a “neutral zone” between a company’s private network and the outside public network. Usage of a protocol within a DMZ environment is highly variable based on the specific needs of an organization.
Privilege escalation, system is compromised when the code runs under root credentials, and DoS attacks are the basic weakness of which one of the following Protocol?
Answer: D
NEW QUESTION 11
Which of the following methods is used to perform server discovery?
Answer: B
NEW QUESTION 12
The Internet is a giant database where people store some of their most private information on the cloud, trusting that the service provider can keep it all safe. Trojans, Viruses, DoS attacks, website defacement, lost computers, accidental publishing, and more have all been sources of major leaks over the last 15 years.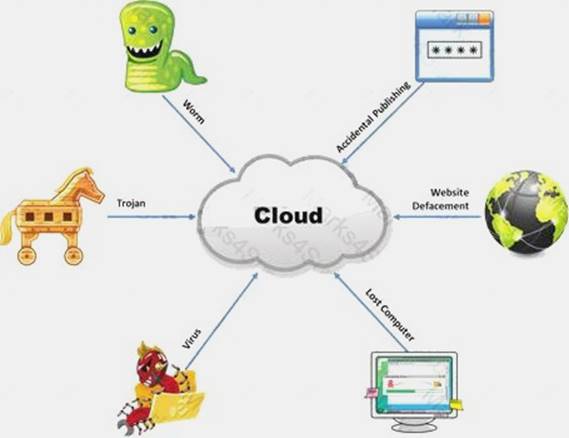
What is the biggest source of data leaks in organizations today?
Answer: C
NEW QUESTION 13
An external intrusion test and analysis identify security weaknesses and strengths of the client's systems and networks as they appear from outside the client's security perimeter, usually from the Internet.
The goal of an external intrusion test and analysis is to demonstrate the existence of known vulnerabilities that could be exploited by an external attacker.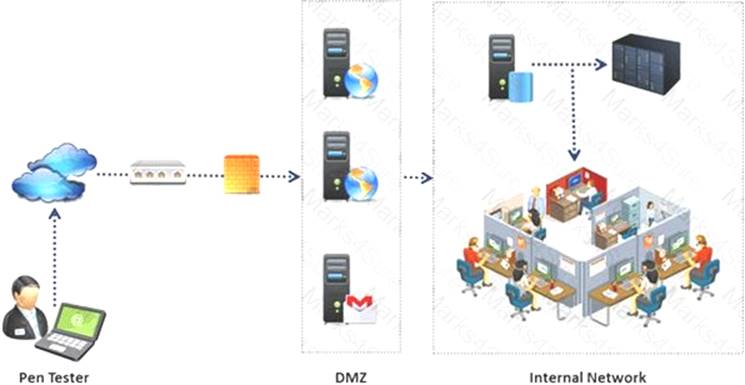
During external penetration testing, which of the following scanning techniques allow you to determine a port’s state without making a full connection to the host?
Answer: B
NEW QUESTION 14
What is the following command trying to accomplish?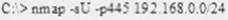
Answer: C
NEW QUESTION 15
You work as a penetration tester for Hammond Security Consultants. You are currently working on a contract for the state government of California. Your next step is to initiate a DoS attack on their network. Why would you want to initiate a DoS attack on a system you are testing?
Answer: C
NEW QUESTION 16
If a web application sends HTTP cookies as its method for transmitting session tokens, it may be vulnerable which of the following attacks?
Answer: D
Thanks for reading the newest 412-79v10 exam dumps! We recommend you to try the PREMIUM Exambible 412-79v10 dumps in VCE and PDF here: https://www.exambible.com/412-79v10-exam/ (201 Q&As Dumps)