
It is more faster and easier to pass the EC-Council 412-79v9 exam by using Breathing EC-Council EC-Council Certified Security Analyst (ECSA) v9 questuins and answers. Immediate access to the Renovate 412-79v9 Exam and find the same core area 412-79v9 questions with professionally verified answers, then PASS your exam with a high score now.
Also have 412-79v9 free dumps questions for you:
NEW QUESTION 1
The term social engineering is used to describe the various tricks used to fool people (employees, business partners, or customers) into voluntarily giving away information that would not normally be known to the general public.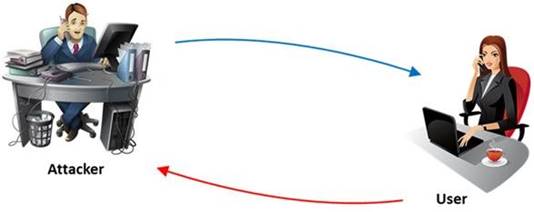
What is the criminal practice of social engineering where an attacker uses the telephone system in an attempt to scam the user into surrendering private information?
Answer: D
NEW QUESTION 2
An automated electronic mail message from a mail system which indicates that the user does not exist on that server is called as?
Answer: D
Explanation:
Reference: http://en.wikipedia.org/wiki/Bounce_message
NEW QUESTION 3
How many bits is Source Port Number in TCP Header packet?
Answer: D
NEW QUESTION 4
Which one of the following tools of trade is an automated, comprehensive penetration testing product for assessing the specific information security threats to an organization?
Answer: C
NEW QUESTION 5
A Demilitarized Zone (DMZ) is a computer host or small network inserted as a “neutral zone” between a company’s private network and the outside public network. Usage of a protocol within a DMZ environment is highly variable based on the specific needs of an organization. Privilege escalation, system is compromised when the code runs under root credentials, and DoS attacks are the basic weakness of which one of the following Protocol?
Answer: D
NEW QUESTION 6
Information gathering is performed to:
i) Collect basic information about the target company and its network
ii) Determine the operating system used, platforms running, web server versions, etc.
iii) Find vulnerabilities and exploits
Which of the following pen testing tests yields information about a company’s technology infrastructure?
Answer: D
NEW QUESTION 7
Identify the person who will lead the penetration-testing project and be the client point of contact.
Answer: C
Explanation:
Reference: http://www.scribd.com/doc/133635286/LPTv4-Module-15-Pre-Penetration-Testing-Checklist-NoRestriction (page 15)
NEW QUESTION 8
Identify the attack represented in the diagram below: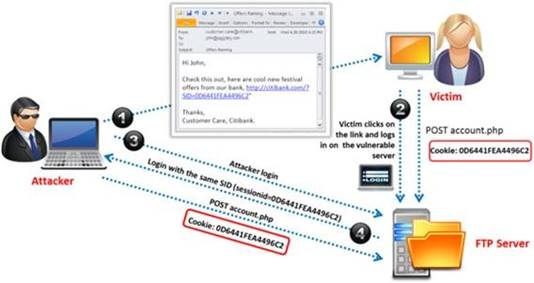
Answer: B
Explanation:
Reference: http://en.wikipedia.org/wiki/Session_hijacking
NEW QUESTION 9
Metasploit framework in an open source platform for vulnerability research, development, and penetration testing. Which one of the following metasploit options is used to exploit multiple systems at once?
Answer: A
NEW QUESTION 10
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram. Each ICMP message contains three fields: type, code, and checksum. Different types of Internet Control Message Protocols (ICMPs) are identified by a type and code field.
Which of the following ICMP messages will be generated if the destination port is not
reachable?
Answer: D
NEW QUESTION 11
Identify the transition mechanism to deploy IPv6 on the IPv4 network from the following diagram.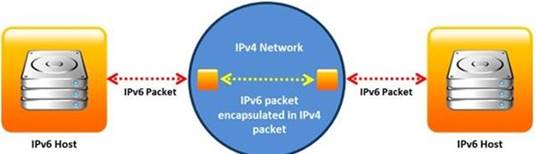
Answer: B
NEW QUESTION 12
Which of the following policy forbids everything with strict restrictions on all usage of the company systems and network?
Answer: B
NEW QUESTION 13
In which of the following IDS evasion techniques does IDS reject the packets that an end system accepts?
Answer: D
Explanation:
Reference: http://is.muni.cz/th/172999/fi_m/MT_Bukac.pdf (page 24)
NEW QUESTION 14
Which of the following is NOT generally included in a quote for penetration testing services?
Answer: B
NEW QUESTION 15
Identify the injection attack represented in the diagram below: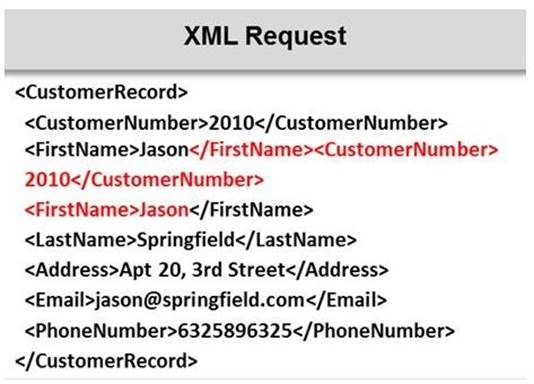
Answer: C
Explanation:
Reference: http://projects.webappsec.org/w/page/13247004/XML%20Injection
NEW QUESTION 16
In which of the following firewalls are the incoming or outgoing packets blocked from accessing services for which there is no proxy?
Answer: D
Explanation:
Reference: http://www.vicomsoft.com/learning-center/firewalls/
NEW QUESTION 17
When you are running a vulnerability scan on a network and the IDS cuts off your
connection, what type of IDS is being used?
Answer: B
NEW QUESTION 18
Which one of the following log analysis tools is used for analyzing the server’s log files?
Answer: C
NEW QUESTION 19
To locate the firewall, SYN packet is crafted using Hping or any other packet crafter and sent to the firewall. If ICMP unreachable type 13 message (which is an admin prohibited packet) with a source IP address of the access control device is received, then it means which of the following type of firewall is in place?
Answer: C
NEW QUESTION 20
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the authentication procedures. Creating a backdoor is a where an attacker obtains remote access to a computer on a network.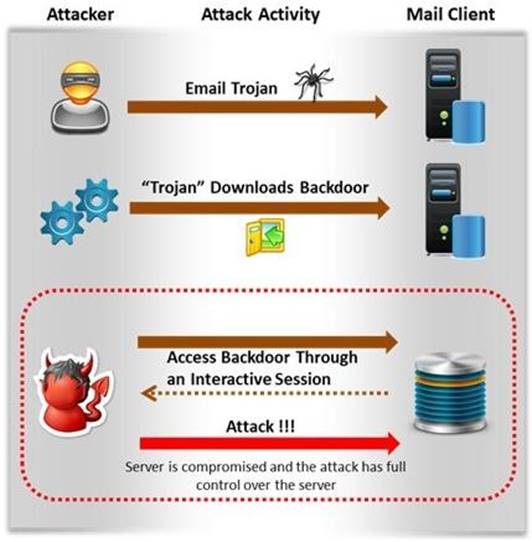
Which of the following techniques do attackers use to create backdoors to covertly gather
critical information about a target machine?
Answer: D
NEW QUESTION 21
You have compromised a lower-level administrator account on an Active Directory network of a small company in Dallas, Texas. You discover Domain Controllers through enumeration. You connect to one of the Domain Controllers on port 389 using Idp.exe. What are you trying to accomplish here?
Answer: D
NEW QUESTION 22
The first and foremost step for a penetration test is information gathering. The main objective of this test is to gather information about the target system which can be used in a malicious manner to gain access to the target systems.
Which of the following information gathering terminologies refers to gathering information through social engineering on-site visits, face-to-face interviews, and direct questionnaires?
Answer: A
NEW QUESTION 23
A WHERE clause in SQL specifies that a SQL Data Manipulation Language (DML) statement should only affect rows that meet specified criteria. The criteria are expressed in the form of predicates. WHERE clauses are not mandatory clauses of SQL DML statements, but can be used to limit the number of rows affected by a SQL DML statement or returned by a query.
A pen tester is trying to gain access to a database by inserting exploited query statements with a WHERE clause. The pen tester wants to retrieve all the entries from the database using the WHERE clause from a particular table (e.g. StudentTable).
What query does he need to write to retrieve the information?
Answer: C
NEW QUESTION 24
Amazon Consulting Corporation provides penetration testing and managed security services to companies. Legality and regulatory compliance is one of the important components in conducting a successful security audit.
Before starting a test, one of the agreements both the parties need to sign relates to limitations, constraints, liabilities, code of conduct, and indemnification considerations between the parties.
Which agreement requires a signature from both the parties (the penetration tester and the company)?
Answer: C
NEW QUESTION 25
Which of the following statements is true about the LM hash?
Answer: A
Explanation:
Reference: http://www.onlinehashcrack.com/how_to_crack_windows_passwords.php (first paragraph of the page)
NEW QUESTION 26
Variables are used to define parameters for detection, specifically those of your local network and/or specific servers or ports for inclusion or exclusion in rules. These are simple substitution variables set with the var keyword. Which one of the following operator is used to define meta-variables?
Answer: A
NEW QUESTION 27
In the TCP/IP model, the transport layer is responsible for reliability and flow control from source to the destination. TCP provides the mechanism for flow control by allowing the sending and receiving hosts to communicate. A flow control mechanism avoids the problem with a transmitting host overflowing the buffers in the receiving host.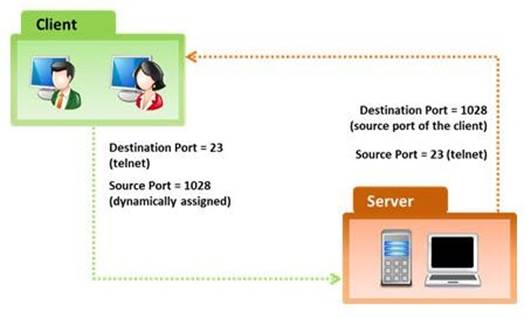
Which of the following flow control mechanism guarantees reliable delivery of data?
Answer: C
Explanation:
Reference: http://condor.depaul.edu/jkristof/technotes/tcp.html (1.1.3 Reliability)
NEW QUESTION 28
In Linux, /etc/shadow file stores the real password in encrypted format for user’s account with added properties associated with the user’s password.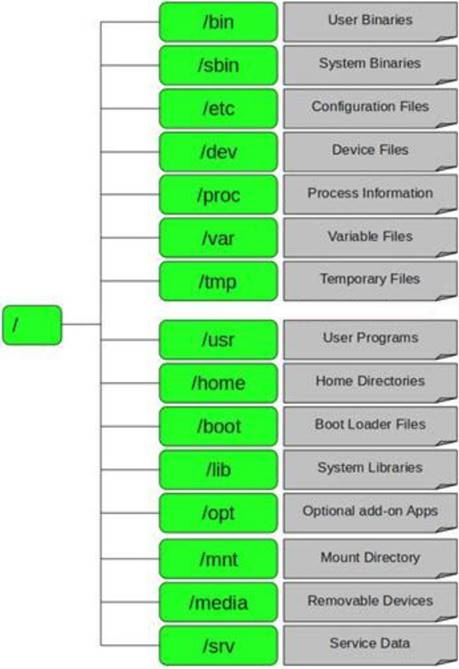
In the example of a /etc/shadow file below, what does the bold letter string indicate?
Vivek: $1$fnffc$GteyHdicpGOfffXX40w#5:13064:0:99999:7
Answer: B
Explanation:
Reference: http://www.cyberciti.biz/faq/understanding-etcshadow-file/ (bullet # 4)
NEW QUESTION 29
Packet filtering firewalls are usually a part of a router. In a packet filtering firewall, each packet is compared to a set of criteria before it is forwarded.
Depending on the packet and the criteria, the firewall can: i)Drop the packet
ii) Forward it or send a message to the originator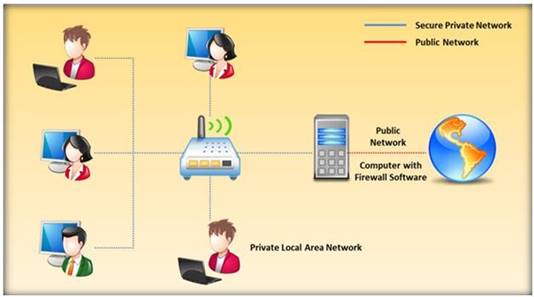
At which level of the OSI model do the packet filtering firewalls work?
Answer: D
Explanation:
Reference: http://books.google.com.pk/books?id=KPjLAyA7HgoC&pg=PA208&lpg=PA208&dq=At+whi ch+level+of+the+OSI+model+do+the+packet+filtering+firewalls+work&source=bl&ots=zRrbcmY3pj&sig=I3vuS3VA7r- 3VF8lC6xq_c_r31M&hl=en&sa=X&ei=wMcfVMetI8HPaNSRgPgD&ved=0CC8Q6AEwAg#v
=onepage&q=At%20which%20level%20of%20the%20OSI%20model%20do%20the%20pa cket%20filtering%20firewalls%20work&f=false (packet filters)
NEW QUESTION 30
......
Recommend!! Get the Full 412-79v9 dumps in VCE and PDF From Dumps-hub.com, Welcome to Download: https://www.dumps-hub.com/412-79v9-dumps.html (New 203 Q&As Version)