
We offers . "Identity with Windows Server 2021", also known as 70-742 exam, is a Microsoft Certification. This set of posts, Passing the 70-742 exam with , will help you answer those questions. The covers all the knowledge points of the real exam. 100% real and revised by experts!
Online 70-742 free questions and answers of New Version:
NEW QUESTION 1
Your network contains an Active Directory domain named contoso.com. The domain contains an enterprise certification authority (CA) named CA1.
You duplicate the Computer certificate template, and you name the template Cont_Computers.
You need to ensure that all of the certificates issued based on Cont_Computers have a key size of 4,096 bits. What should you do?
Answer: C
NEW QUESTION 2
Note: This question is part of a series of questions that use the same or similar answer choice. An answer choice may be correct for more than one question in the series. Each question is Independent of the other questions in this series. Information and details provided in a question apply only to that question.
Your network contains an Active Directory domain named contoso.com. The domain functional level is Windows Server 2012 R2.
Your company hires 3 new security administrators to manage sensitive user data. You create a user account named Secunty1 for the security administrator.
You need to ensure that the password for Secunty1 has at least 12 characters and is modified every 10 days. The solution must apply to Security 1 only.
Which tool should you use?
Answer: C
Explanation: Using Fine-Grained Password Policies you specify multiple password policies in a single domain and apply different restrictions for password and account lockout policies to different sets of users in a domain. You can apply stricter settings to privileged accounts and less strict settings to the accounts of other users.To enable Fine-Grained Password Policies (FGPP), you need to open the Active Directory Administrative Center (ADAC)https://blogs.technet.microsoft.com/canitpro/2013/05/29/step-by-step-enabling-and-using-fine-grained-
NEW QUESTION 3
Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
Your network contains an Active Directory domain named contoso.com. The domain contains a single site named Site1. All computers are in Site1.
The Group Policy objects (GPOs) for the domain are configured as shown in the exhibit. (Click the Exhibit button.)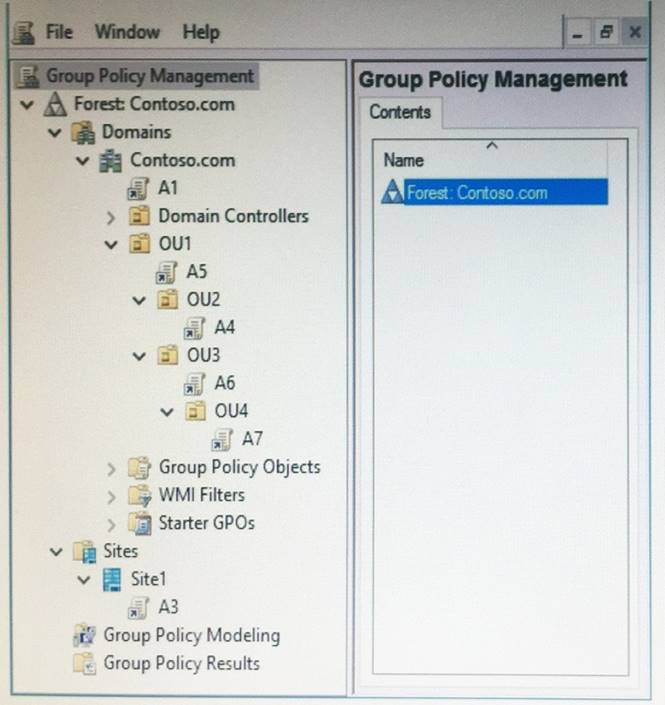
The relevant users and client computer in the domain are configured as shown in the following table.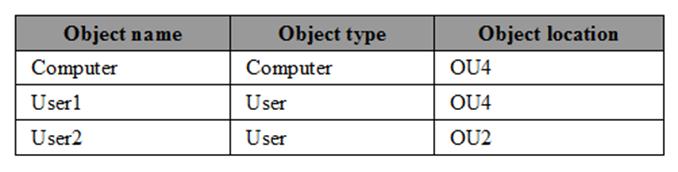
End of repeated scenario.
You are evaluating what will occur when you disable the Group Policy link for A6.
Which GPOs will apply to User2 when the user signs in to Computer1 after the link for A6 is disabled?
Answer: C
NEW QUESTION 4
Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
Your network contains an Active Directory domain named contoso.com. The domain contains a single site named Site1. All computers are in Site1.
The Group Policy objects (GPOs) for the domain are configured as shown in the exhibit. (Click the Exhibit button.)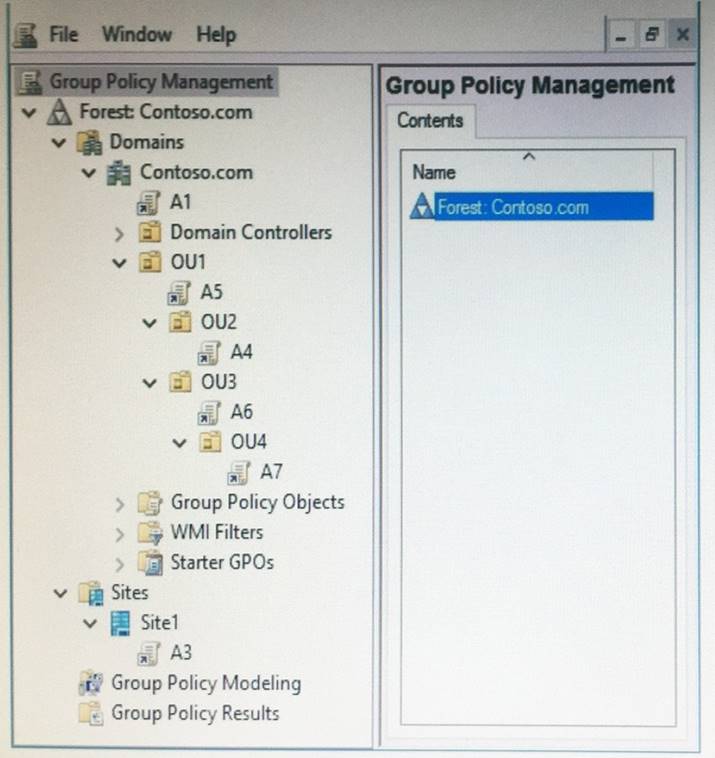
The relevant users and client computer in the domain are configured as shown in the following table.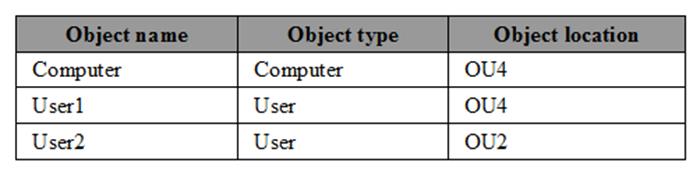
End of repeated scenario.
You plan to enforce the GPO link for A6.
Which five GPOs will apply to User1 in sequence when the user signs in to Computer1 after the link is enforced? To answer, move the appropriate GPOs from the list of GPOs to the answer area and arrange them in the correct order.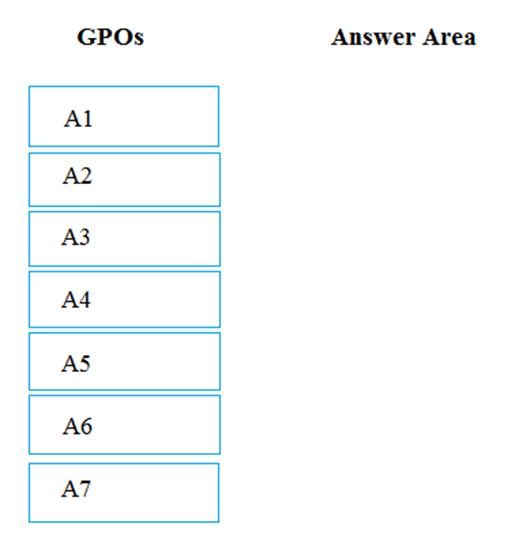
Answer:
Explanation: 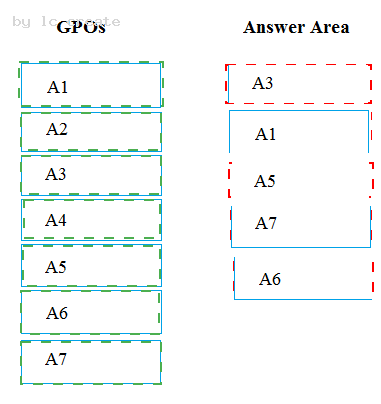
NEW QUESTION 5
Note: This question is part of a series of questions that use the same or similar answer choices. An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series.
Information and details provided in a question apply only to that question.
Your network contains an Active Directory domain named contoso.com. The domain contains 5,000 user accounts.
You have a Group Policy object (GPO) named DomainPolicy that is linked to the domain and a GPO named DCPolicy that is linked to the Domain Controllers organizational unit (OU).
You need to use the application control policy settings to prevent several applications from running on the network.
What should you do?
Answer: B
NEW QUESTION 6
Your network contains an Active Directory domain named contos.com.
You need to create a central store for Group Policy administrative templates. What should you use?
Answer: B
NEW QUESTION 7
Note: This question is part of a series of questions that use the same or similar answer choices. An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series. Information and details provided in a question apply only to that question.
Your network contains an Active Directory forest named contoso.com. The forest functional level is Windows Server 2012 R2.
You need to ensure that a domain administrator can recover a deleted Active Directory object quickly. Which tool should you use?
Answer: C
NEW QUESTION 8
Your network contains an Active Directory domain named contoso.com. The domain contains a read-only domain controller (RODC) named R0DC1.
You need to retrieve a list of accounts that have their password cached on RODC1. Which command should you run?
Answer: C
Explanation: https://technet.microsoft.com/en-us/library/rodc-guidance-for-administering-the-password-replication-policy(v=
NEW QUESTION 9
Your network contains an Active Directory domain named contoso.com. All the accounts of the users in the sales department are in an organizational unit (OU) named SalesOU.
An application named App1 is deployed to the user accounts in SalesOU by using a Group Policy object (GPO) named Sales GPO.
You need to set the registry value of HKEY_CURRENT_USERSoftwareApp1Collaboration to 0. Solution: You add a computer preference that has a Replace action.
Does this meet the goal?
Answer: A
NEW QUESTION 10
Your company has two offices. The offices are located in Montreal and Seattle. The network contains an Active Directory forest named contoso.com.
The forest contains three domain controllers configured as shown in the following table.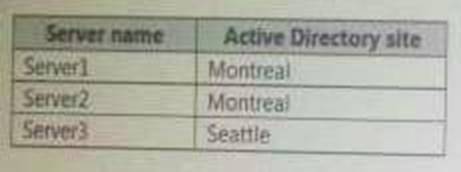
The company physically relocates Server2 from the Montreal office the Seattle office.
You discover that both Server1 and Server2 authenticate users who sign in to the client computers in the Montreal office. Only Server3 authentications users who sign in to the computers in the Seattle office.
You need to ensure that Server2 authenticates the users in the Seattle office during normal network operations. What should you do?
Answer: C
NEW QUESTION 11
A technician named Tech1 is assigned the task of joining the laptops to the domain. The computer accounts of each laptop must be in an organizational unit (OU) that is associated to the department of the user who will use that laptop. The laptop names must start with four characters indicating the department followed by a
four-digit number
Tech1 is a member of the Domain Users group only. Tech1 has the administrator logon credentials for all the laptops.
You need Tech1 to join the laptops to the domain. The solution must ensure that the laptops are named
correctly, and that the computer accounts of the laptops are in the correct OUs.
Solution: You script the creation of files for an offline domain join, and then you give the files to Tech1. You instruct Tech1 to sign in to each laptop, and then to run djoin.exe.
Does this meet the goal?
Answer: A
NEW QUESTION 12
Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated Scenario:
You work for a company named Contoso, Ltd.
The network contains an Active Directory forest named contoso.com. A forest trust exists between contoso.com and an Active Directory forest named adatum.com.
The contoso.com forest contains the objects configured as shown in the following table. Scenario:
Refer to following table: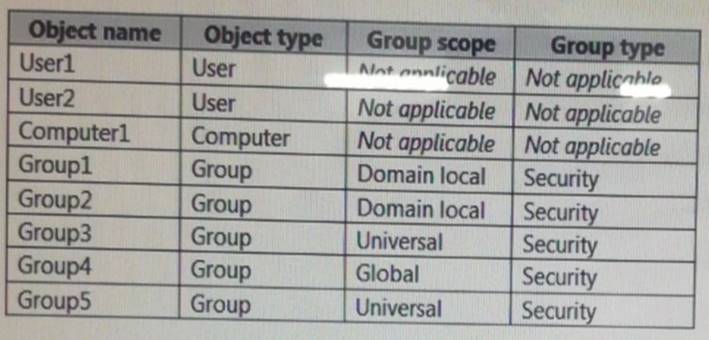
Group1 and Group 2 contain only user accounts.
Contoso hires a new remote user named User3. User3 will work from home and will use a computer named Computed that runs Windows 10. Computed is currently in a workgroup.
An administrator named Admin1 is a member of the Domain Admins group in the contoso.com domain. From Active Directory Users and Computers, you create an organizational unit (OU) named OU1 in the
contoso.com domain, and then you create a contact named Contact1 in OU1,
An administrator of the adatum.com domain runs the Set-ADUser cmdlet to configure a user named User1 to have a user logon name of User1@litwareinc.com.
End of Scenario:
Admin1 attempts to delete OU1 and receives an error message. You need to ensure that Admin1 can delete OU1. What should you do first?
Answer: C
NEW QUESTION 13
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You deploy a new Active Directory forest.
You need to ensure that you can create a group Managed Service Account (gMSA) for multiple member servers.
Solution: You configure Kerberos constrained delegation on the computer account of each member server. Does this meet the goal?
Answer: B
NEW QUESTION 14
Your network contains an Active Directory domain named contoso.com. The network contains several IP subnets. One of the subnets uses a network ID if 192.168.10.0/24.
You link a Group Policy object (GPO) named GPO1 to the domain.
You need to map a drive to a specific file share on the computers in the 192.168.10.0/24 network only. What should you do?
Answer: C
NEW QUESTION 15
Your network contains an Active Directory forest named contoso.com
Your company plans to hire 500 temporary employees for a project that will last 90 days.
You create a new user account for each employee. An organizational unit (OU) named Temp contains the user accounts for the employees.
You need to prevent the new users from accessing any of the resources in the domain after 90 days. What should you do?
Answer: A
NEW QUESTION 16
Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated Scenario
You work for a company named Contoso, Ltd.
The network contains an Active Directory forest named contoso.com. A forest trust exists between contoso.com and an Active Directory forest named adatum.com.
The contoso.com forest contains the objects configured as shown in the following table.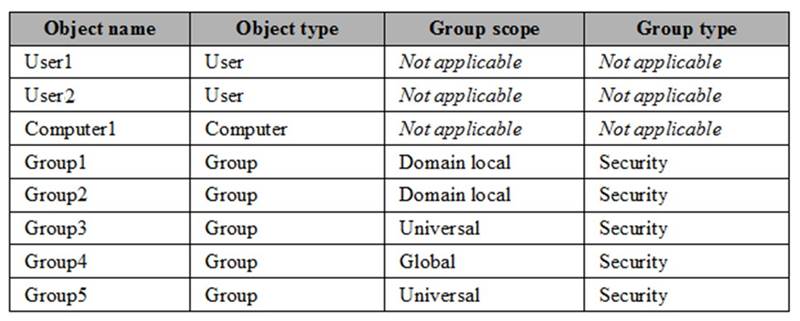
Group 1 and Group2 contain only user accounts.
Contoso hires a new remote user named User3. User3 will work from home and will use a computer named
Computer3 that runs Windows 10. Computer3 is currently in a workgroup.
An administrator named Admin1 is a member of the Domain Admins group in the contoso.com domain. From Active Directory Users and Computers, you create an organizational unit (OU) named OU1 in the
contoso.com domain, and then you create a contact named Contact1 in OU1.
An administrator of the adatum.com domain runs the Set-ADUser cmdlet to configure a user named User1 to have a user logon name of user1@litwareinc.com.
End of repeated scenario
You need to ensure that Admin1 can convert Group1 to a global group. What should you do?
Answer: B
P.S. Easily pass 70-742 Exam with 222 Q&As Certleader Dumps & pdf Version, Welcome to Download the Newest Certleader 70-742 Dumps: https://www.certleader.com/70-742-dumps.html (222 New Questions)