
are updated and are verified by experts. Once you have completely prepared with our you will be ready for the real CAS-003 exam without a problem. We have . PASSED First attempt! Here What I Did.
Check CAS-003 free dumps before getting the full version:
NEW QUESTION 1
Click on the exhibit buttions to view the four messages.
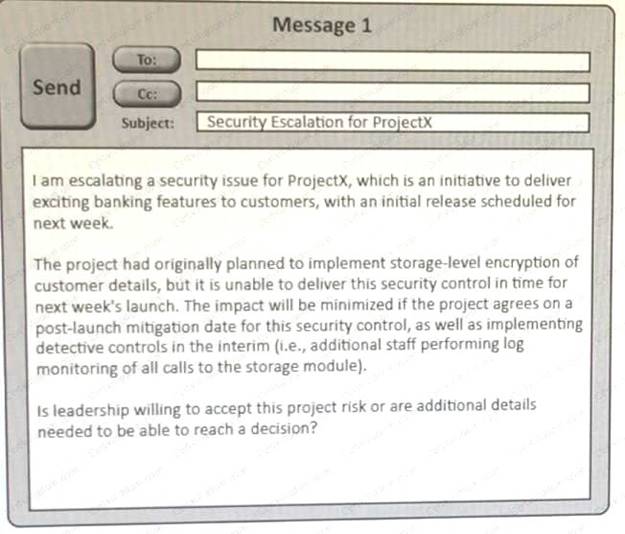
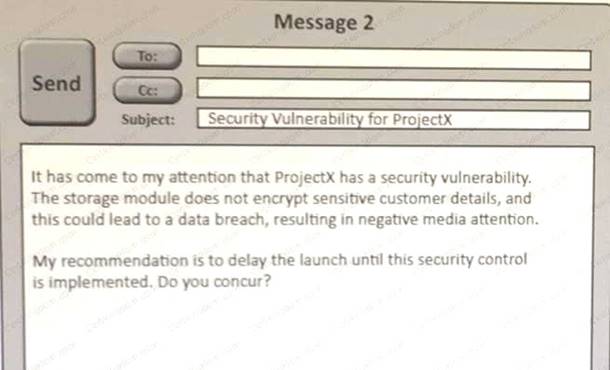
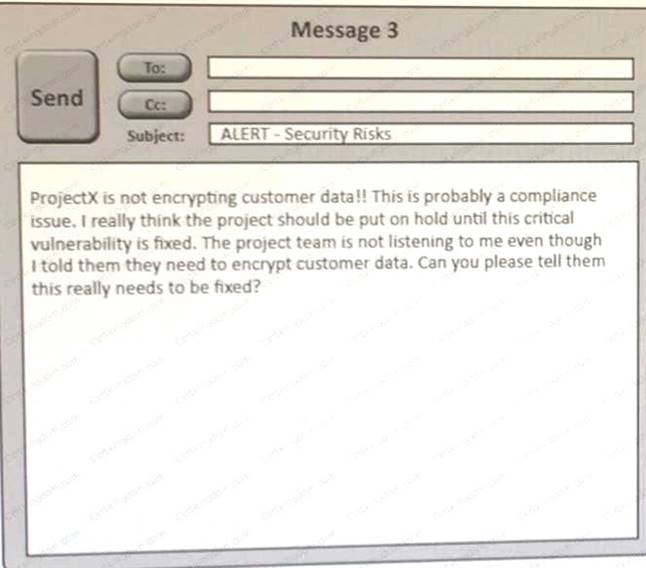

A security architect is working with a project team to deliver an important service that stores and processes customer banking details. The project, internally known as ProjectX, is due to launch its first set of features publicly within a week, but the team has not been able to implement encryptionat- rest of the customer records. The security architect is drafting an escalation email to senior leadership.
Which of the following BEST conveys the business impact for senior leadership?
Answer: D
NEW QUESTION 2
A security manager is looking into the following vendor proposal for a cloud-based SIEM solution. The intention is that the cost of the SIEM solution will be justified by having reduced the number of incidents and therefore saving on the amount spent investigating incidents.
Proposal:
External cloud-based software as a service subscription costing $5,000 per month. Expected to reduce the number of current incidents per annum by 50%.
The company currently has ten security incidents per annum at an average cost of $10,000 per incident. Which of the following is the ROI for this proposal after three years?
Answer: A
Explanation: Return on investment = Net profit / Investment where: Net profit = gross profit - expenses.
or
Return on investment = (gain from investment – cost of investment) / cost of investment Subscriptions = 5,000 x 12 = 60,000 per annum
10 incidents @ 10,000 = 100.000 per annum reduce by 50% = 50,000 per annum
Thus the rate of Return is -10,000 per annum and that makes for -$30,000 after three years. References:
http://www.finHYPERLINK "http://www.financeformulas.net/Return_on_Investment.html"anceformulas.net/Return_on_Invest ment.html
NEW QUESTION 3
A cybersecurity analyst has received an alert that well-known "call home" messages are continuously observed by network sensors at the network boundary. The proxy firewall successfully drops the massages. After determining the alert was a true positive, which of the following represents OST
likely cause?
Answer: B
NEW QUESTION 4
An organization is in the process of integrating its operational technology and information technology areas. As part of the integration, some of the cultural aspects it would like to see include more efficient use of resources during change windows, better protection of critical infrastructure, and the ability to respond to incidents. The following observations have been identified:
The ICS supplier has specified that any software installed will result in lack of support.
There is no documented trust boundary defined between the SCADA and corporate networks.
Operational technology staff have to manage the SCADA equipment via the engineering workstation. There is a lack of understanding of what is within the SCADA network.
Which of the following capabilities would BEST improve the security position?
Answer: A
NEW QUESTION 5
Which of the following BEST represents a risk associated with merging two enterprises during an acquisition?
Answer: C
NEW QUESTION 6
An SQL database is no longer accessible online due to a recent security breach. An investigation reveals that unauthorized access to the database was possible due to an SQL injection vulnerability. To prevent this type of breach in the future, which of the following security controls should be put in place before bringing the database back online? (Choose two.)
Answer: CF
NEW QUESTION 7
The senior security administrator wants to redesign the company DMZ to minimize the risks associated with both external and internal threats. The DMZ design must support security in depth, change management and configuration processes, and support incident reconstruction. Which of the following designs BEST supports the given requirements?
Answer: A
Explanation: Security in depth is the concept of creating additional layers of security. The traditional approach of securing the IT infrastructure is no longer enough. Today’s threats are multifaceted and often persistent, and traditional network perimeter security controls cannot effectively mitigate them. Organizations need to implement more effective, multi-level security controls that are embedded with their electronic assets. They need to protect key assets from both external and internal threats. This security in depth approach is meant to sustain attacks even when perimeter and traditional controls have been breached.
In this question, using two firewalls to secure the DMZ from both external and internal attacks is the best approach. Having each firewall managed by a separate administrator will reduce the chance of a configuration error being made on both firewalls. The remote logging will enable incident reconstruction.
Incorrect Answers:
B: Depending on the number of interfaces on the firewall, you could protect from external and internal threats with a single firewall although two firewalls is a better solution. However, it is not practical to have separate interfaces on the same firewall managed by different administrators. The firewall rules work together in a hierarchy to determine what traffic is allowed through each interface.
C: A SaaS based firewall can be used to protect cloud resources. However, it is not the best solution for protecting the network in this question.
D: A virtualized firewall could be used. However, multiple instances of the same firewall should be identical. They should not be configured separately by different administrators.
References:
http://www.oracle.com/technetwork/topics/entarch/oracle-wp-securiHYPERLINK "http://www.oracle.com/technetwork/topics/entarch/oracle-wp-security-ref-arch-1918345.pdf"tyref- arch-1918345.pdf
NEW QUESTION 8
A security consultant is attempting to discover if the company is utilizing databases on client machines to store the customer data.
The consultant reviews the following information: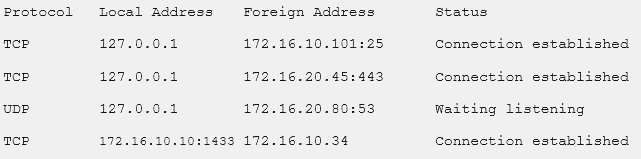
Which of the following commands would have provided this output?
Answer: B
NEW QUESTION 9
During the decommissioning phase of a hardware project, a security administrator is tasked with ensuring no sensitive data is released inadvertently. All paper records are scheduled to be shredded in a crosscut shredded, and the waste will be burned. The system drives and removable media have been removed prior to e-cycling the hardware.
Which of the following would ensure no data is recovered from the system droves once they are disposed of?
Answer: C
NEW QUESTION 10
An administrator wishes to replace a legacy clinical software product as it has become a security risk. The legacy product generates $10,000 in revenue a month. The new software product has an initial cost of $180,000 and a yearly maintenance of $2,000 after the first year. However, it will generate
$15,000 in revenue per month and be more secure. How many years until there is a return on investment for this new package?
Answer: D
Explanation: Return on investment = Net profit / Investment where:
Profit for the first year is $60 000, second year = $ 120 000 ; third year = $ 180 000 ; and fourth year =
$ 240 000
investment in first year = $ 180 000, by year 2 = $ 182 000; by year 3 = $ 184 000 ; and by year 4 = $
186 000
Thus you will only get a return on the investment in 4 years’ time. References: http://www.financeformulas.net/Return_on_InvestmentHYPERLINK "http://www.financeformulas.net/Return_on_Investment.html".html
NEW QUESTION 11
A security controls assessor intends to perform a holistic configuration compliance test of networked assets. The assessor has been handed a package of definitions provided in XML format, and many of the files have two common tags within them: “<object object_ref=… />” and “<state state_ref=… />”. Which of the following tools BEST supports the use of these definitions?
Answer: D
NEW QUESTION 12
A penetration tester has been contracted to conduct a physical assessment of a site. Which of the following is the MOST plausible method of social engineering to be conducted during this engagement?
Answer: A
NEW QUESTION 13
Which of the following is the GREATEST security concern with respect to BYOD?
Answer: D
NEW QUESTION 14
The board of a financial services company has requested that the senior security analyst acts as a cybersecurity advisor in order to comply with recent federal legislation. The analyst is required to give a report on current cybersecurity and threat trends in the financial services industry at the next board meeting. Which of the following would be the BEST methods to prepare this report? (Choose two.)
Answer: AD
NEW QUESTION 15
An architect was recently hired by a power utility to increase the security posture of the company’s power generation and distribution sites. Upon review, the architect identifies legacy hardware with highly vulnerable and unsupported software driving critical operations. These systems must exchange data with each other, be highly synchronized, and pull from the Internet time sources.
Which of the following architectural decisions would BEST reduce the likelihood of a successful attack without harming operational capability? (Choose two.)
Answer: BE
NEW QUESTION 16
An insurance company has an online quoting system for insurance premiums. It allows potential customers to fill in certain details about their car and obtain a quote. During an investigation, the following patterns were detected:
Pattern 1 – Analysis of the logs identifies that insurance premium forms are being filled in but only single fields are incrementally being updated.
Pattern 2 – For every quote completed, a new customer number is created; due to legacy systems, customer numbers are running out.
Which of the following is the attack type the system is susceptible to, and what is the BEST way to defend against it? (Select TWO).
Answer: CF
Explanation: A resource exhaustion attack involves tying up predetermined resources on a system, thereby making the resources unavailable to others.
Implementing an inline WAF would allow for protection from attacks, as well as log and alert admins to what's going on. Integrating in into SIEM allows for logs and other security-related documentation to be collected for analysis.
Incorrect Answers:
A: SIEM technology analyses security alerts generated by network hardware and applications. B: Cross site scripting attacks occur when malicious scripts are injected into otherwise trusted websites.
D: Traditional firewalls block or allow traffic. It is not, however, the best way to defend against a resource exhaustion attack.
E: A SQL injection attack occurs when the attacker makes use of a series of malicious SQL queries to directly influence the SQL database.
G: A distributed denial-of-service (DDoS) attack occurs when many compromised systems attack a single target. This results in denial of service for users of the targeted system.
H: Traditional firewalls block or allow traffic. It is not, however, the best way to defend against a resource exhaustion attack.
References:
http://searchsecurity.techtarget.com/feature/Four-questions-to-ask-befoHYPERLINK "http://searchsecurity.techtarget.com/feature/Four-questions-to-ask-before-buying-a-Webapplication- firewall"re-buying-a-Web-application-firewall
http://searchsecurity.techtarget.comHYPERLINK "http://searchsecurity.techtarget.com/definition/security-information-and-event-management- SIEM"/definition/security-information-and-event-management-SIEM https://en.wikipedia.org/wiki/Security_information_and_event_management
http:HYPERLINK "http://searchsecurity.techtarget.com/definition/distributed-denial-of-serviceattack"// searchsecurity.techtarget.com/definitHYPERLINK "http://searchsecurity.techtarget.com/definition/distributed-denial-of-serviceattack"
ion/distributed-denial-of-service-attack
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 150, 153
NEW QUESTION 17
An analyst has noticed unusual activities in the SIEM to a .cn domain name. Which of the following should the analyst use to identify the content of the traffic?
Answer: D
P.S. Certstest now are offering 100% pass ensure CAS-003 dumps! All CAS-003 exam questions have been updated with correct answers: https://www.certstest.com/dumps/CAS-003/ (434 New Questions)