
Want to know features? Want to lear more about experience? Study . Gat a success with an absolute guarantee to pass CompTIA CAS-003 (CompTIA Advanced Security Practitioner (CASP)) test on your first attempt.
Online CompTIA CAS-003 free dumps demo Below:
NEW QUESTION 1
A business is growing and starting to branch out into other locations. In anticipation of opening an office in a different country, the Chief Information Security Officer (CISO) and legal team agree they need to meet the following criteria regarding data to open the new office:
Store taxation-related documents for five years Store customer addresses in an encrypted format Destroy customer information after one year Keep data only in the customer’s home country
Which of the following should the CISO implement to BEST meet these requirements? (Choose three.)
Answer: BCH
NEW QUESTION 2
A security administrator wants to prevent sensitive data residing on corporate laptops and desktops from leaking outside of the corporate network. The company has already implemented full-disk encryption and has disabled all peripheral devices on its desktops and laptops. Which of the following additional controls MUST be implemented to minimize the risk of data leakage? (Select TWO).
Answer: BD
Explanation: Web mail, Instant Messaging and personal networking sites are some of the most common means by which corporate data is leaked.
Data loss prevention (DLP) is a strategy for making sure that end users do not send sensitive or critical information outside the corporate network. The term is also used to describe software products that help a network administrator control what data end users can transfer.
DLP software products use business rules to classify and protect confidential and critical information so that unauthorized end users cannot accidentally or maliciously share data whose disclosure could put the organization at risk. For example, if an employee tried to forward a business email outside the corporate domain or upload a corporate file to a consumer cloud storage service like Dropbox, the employee would be denied permission.
Full-tunnel VPN should be required for all network communication. This will ensure that all data transmitted over the network is encrypted which would prevent a malicious user accessing the data by using packet sniffing.
Incorrect Answers:
A: This question is asking which of the following additional controls MUST be implemented to minimize the risk of data leakage. Implementing a full system backup does not minimize the risk of data leakage.
C: Strong authentication implemented via external biometric devices will ensure that only authorized people can access the network. However, it does not minimize the risk of data leakage.
E: Full-drive file hashing is not required because we already have full drive encryption.
F: Split-tunnel VPN is used when a user a remotely accessing the network. Communications with company servers go over a VPN whereas private communications such as web browsing does not use a VPN. A more secure solution is a full tunnel VPN.
References:
http://whatis.techtarget.com/defHYPERLINK "http://whatis.techtarget.com/definition/data-lossprevention- DLP"inition/data-loss-prevention-DLP
NEW QUESTION 3
A company has issued a new mobile device policy permitting BYOD and company-issued devices. The company-issued device has a managed middleware client that restricts the applications allowed on company devices and provides those that are approved. The middleware client provides
configuration standardization for both company owned and BYOD to secure data and communication to the device according to industry best practices. The policy states that, “BYOD clients must meet the company’s infrastructure requirements to permit a connection.” The company also issues a memorandum separate from the policy, which provides instructions for the purchase, installation, and use of the middleware client on BYOD. Which of the following is being described?
Answer: B
Explanation: It governance is aimed at managing information security risks. It entails educating users about risk and implementing policies and procedures to reduce risk.
Incorrect Answers:
A: Asset management is the process of organizing, t racking, and supporting the assets of a company. However, bring your own device (BYOD) entail the use of personal devices, which are not company assets.
C: Change management is the process of managing changes to the system and programs to ensure that changes occur in an ordered process. It should minimize the risk of unauthorized changes and help reverse any unauthorized change.
D: Transference of risk is the process of having a third party carry the risk for a company, through insurance, for example.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 80-81, 133-134, 209-210, 218, 231-233
NEW QUESTION 4
A large enterprise acquires another company which uses antivirus from a different vendor. The CISO has requested that data feeds from the two different antivirus platforms be combined in a way that allows management to assess and rate the overall effectiveness of antivirus across the entire organization. Which of the following tools can BEST meet the CISO’s requirement?
Answer: A
Explanation: GRC is a discipline that aims to coordinate information and activity across governance, risk management and compliance with the purpose of operating more efficiently, enabling effective information sharing, more effectively reporting activities and avoiding wasteful overlaps. An integrated GRC (iGRC) takes data feeds from one or more sources that detect or sense abnormalities, faults or other patterns from security or business applications.
Incorrect Answers:
B: IPS is a typical sensor type that is included in an iGRC.
C: A configuration management database (CMDB) is defined as a repository that acts as a data warehouse for IT organizations.
D: syslog-ng sends incoming log messages from specified sources to the correct destinations. E: IDS is a typical sensor type that is included in an iGRC.
References: https://en.wikipedia.org/wHYPERLINK
"https://en.wikipedia.org/wiki/Governance,_risk_management,_and_compliance#Integrated_gover nance.2C_risk_and_compliancy"iki/Governance,_risk_managemeHYPERLINK "https://en.wikipedia.org/wiki/Governance,_risk_management,_and_compliance#Integrated_gover nance.2C_risk_and_compliancy"nt,_and_HYPERLINK "https://en.wikipedia.org/wiki/Governance,_risk_management,_and_compliance#Integrated_gover nance.2C_risk_and_compliancy"compliance#Integrated_governance.2C_risk_and_compliancy https://wiki.archlinux.org/index.php/Syslog-ng
NEW QUESTION 5
A recent CRM upgrade at a branch office was completed after the desired deadline. Several technical issues were found during the upgrade and need to be discussed in depth before the next branch office is upgraded. Which of the following should be used to identify weak processes and other vulnerabilities?
Answer: D
NEW QUESTION 6
A completely new class of web-based vulnerabilities has been discovered. Claims have been made that all common web-based development frameworks are susceptible to attack. Proof-of-concept details have emerged on the Internet. A security advisor within a company has been asked to provide recommendations on how to respond quickly to these vulnerabilities. Which of the following BEST describes how the security advisor should respond?
Answer: A
Explanation: The first thing you should do is verify the reliability of the claims. From there you can assess the likelihood of the vulnerability affecting your systems. If it is determined that your systems are likely to be affected by the explogt, you need to determine what impact an attack will have on your hosted dat
A. Now that you know what the impact will be, you can test the explogt by using the proof-ofconcept code. That should help you determine your options for dealing with the threat
(remediation). Incorrect Answers:
B: While penetration testing your system is a good idea, it is unnecessary to hire an independent security consulting agency to perform a penetration test of the web servers. You know what the vulnerability is so you can test it yourself with the proof-of-concept code.
C: Security response should be proactive. Waiting for the threat to be verified by the software vendor will leave the company vulnerable if the vulnerability is real.
D: Bringing down the web servers would prevent the vulnerability but would also render the system useless. Furthermore, customers would expect a certain level of service and may even have a service level agreement in place with guarantees of uptime.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 375-376
NEW QUESTION 7
ABC Company must achieve compliance for PCI and SOX. Which of the following would BEST allow the organization to achieve compliance and ensure security? (Select THREE).
Answer: BDF
Explanation: Payment card industry (PCI) compliance is adherence to a set of specific security standards that were
developed to protect card information during and after a financial transaction. PCI compliance is required by all card brands.
There are six main requirements for PCI compliance. The vendor must: Build and maintain a secure network
Protect cardholder data
Maintain a vulnerability management program Implement strong access control measures Regularly monitor and test networks Maintain an information security policy
To achieve PCI and SOX compliance you should:
Establish a list of devices that must meet each regulation. List all the devices that contain the sensitive data.
Compartmentalize the network. Compartmentalize the devices that contain the sensitive data to form a security boundary.
Apply technical controls to meet compliance with the regulation. Secure the data as required. Incorrect Answers:
A: It is not necessary to establish a list of users that must work with each regulation. All users should be trained to manage sensitive dat
A. However, PCI and SOX compliance is more about the security of the data on the computers that contain the data.
C: Central management of all devices on the network makes device management easier for administrators. However, it is not a requirement for PCI and SOX compliance.
E: A company framework is typically related to the structure of employee roles and departments. It is not a requirement for PCI and SOX compliance.
References:
http://searchcompliance.techtarget.com/definition/PCI-compliaHYPERLINK "http://searchcompliance.techtarget.com/definition/PCI-compliance"nce
NEW QUESTION 8
In a situation where data is to be recovered from an attacker’s location, which of the following are the FIRST things to capture? (Select TWO).
Answer: CE
Explanation: An exact copy of the attacker’s system must be captured for further investigation so that the original data can remain unchanged. An analyst will then start the process of capturing data from the most volatile to the least volatile.
The order of volatility from most volatile to least volatile is as follows: Data in RAM, including CPU cache and recently used data and applications Data in RAM, including system and network processes
Swap files (also known as paging files) stored on local disk drives Data stored on local disk drives
Logs stored on remote systems Archive media
Incorrect Answers:
A: Removable media is not regarded as volatile data.
B: Passwords written on scrap paper is not regarded as volatile data. D: Documents on the printer is not regarded as volatile data.
F: Data stored on the system hard drive is lower in the order of volatility compared to system memory.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 250-254
http://blogs.getcertifiedgetahead.com/security-forensic-pHYPERLINK "http://blogs.getcertifiedgetahead.com/security-forensic-performance-basedquestion/" erformaHYPERLINK "http://blogs.getcertifiedgetahead.com/security-forensicperformance- based-question/"nce-based-question/
NEW QUESTION 9
Wireless users are reporting issues with the company’s video conferencing and VoIP systems. The security administrator notices internal DoS attacks from infected PCs on the network causing the VoIP system to drop calls. The security administrator also notices that the SIP servers are unavailable
during these attacks. Which of the following security controls will MOST likely mitigate the VoIP DoS attacks on the network? (Select TWO).
Answer: AD
Explanation: Host-based intrusion prevention system (HIPS) is an installed software package that will monitor a single host for suspicious activity by analyzing events taking place within that host.
IEEE 802.11e is deemed to be of significant consequence for delay-sensitive applications, such as Voice over Wireless LAN and streaming multimedia.
Incorrect Answers:
B: 802.1X is used by devices to attach to a LAN or WLAN.
C: Updating the corporate firewall will not work as the DoS attacks are from an internal source. E: 802.1q is used for VLAN tagging.
References: https:HYPERLINK
"https://en.wikipedia.org/wiki/Intrusion_prevention_system"//en.wikipedia.org/wiki/Intrusion_pre vention_system
https://en.wikipedia.orHYPERLINK "https://en.wikipedia.org/wiki/IEEE_802.11e- 2005"g/wiki/IEEE_802.11e-2005
https://en.wikipedia.org/wiki/IEEE_802.1X https://en.wikipedia.org/wiki/IEEE_802.1Q
NEW QUESTION 10
An external penetration tester compromised one of the client organization’s authentication servers and retrieved the password database. Which of the following methods allows the penetration tester to MOST efficiently use any obtained administrative credentials on the client organization’s other systems, without impacting the integrity of any of the systems?
Answer: A
Explanation: With passing the hash you can grab NTLM credentials and you can manipulate the Windows logon sessions maintained by the LSA component. This will allow you to operate as an administrative user and not impact the integrity of any of the systems when running your tests.
Incorrect Answers:
B: Making use of rainbow tables and cracking passwords will have a definite impact on the integrity of the other systems that are to be penetration tested.
C: Changing passwords will impact the integrity of the other systems and is not a preferable method to conduct penetration testing.
D: Social engineering is not the preferred way to accomplish the goal of penetration testing and
gaining administrative credentials on the client’s network. References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 17, 351
NEW QUESTION 11
During an incident involving the company main database, a team of forensics experts is hired to respond to the breach. The team is in charge of collecting forensics evidence from the company’s database server. Which of the following is the correct order in which the forensics team should engage?
Answer: D
Explanation: The scene has to be secured first to prevent contamination. Once a forensic copy has been created,
an analyst will begin the process of moving from most volatile to least volatile information. The chain of custody helps to protect the integrity and reliability of the evidence by keeping an evidence log that shows all access to evidence, from collection to appearance in court.
Incorrect Answers:
A: To prevent contamination, the scene should be secured first. B: The scene should be secured before taking inventory.
C: Implementing a chain of custody can only occur once evidence has been accessed. References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 250-254
NEW QUESTION 12
A company has decided to lower costs by conducting an internal assessment on specific devices and various internal and external subnets. The assessment will be done during regular office hours, but it must not affect any production servers. Which of the following would MOST likely be used to complete the assessment? (Select two.)
Answer: AC
NEW QUESTION 13
A database administrator is required to adhere to and implement privacy principles when executing daily tasks. A manager directs the administrator to reduce the number of unique instances of PII stored within an organization’s systems to the greatest extent possible. Which of the following principles is being demonstrated?
Answer: D
NEW QUESTION 14
Due to a recent breach, the Chief Executive Officer (CEO) has requested the following activities be conducted during incident response planning:
Involve business owners and stakeholders Create an applicable scenario
Conduct a biannual verbal review of the incident response plan Report on the lessons learned and gaps identified
Which of the following exercises has the CEO requested?
Answer: C
NEW QUESTION 15
An organization is preparing to develop a business continuity plan. The organization is required to meet regulatory requirements relating to confidentiality and availability, which are well-defined. Management has expressed concern following initial meetings that the organization is not fully aware of the requirements associated with the regulations. Which of the following would be MOST appropriate for the project manager to solicit additional resources for during this phase of the project?
Answer: B
NEW QUESTION 16
After investigating virus outbreaks that have cost the company $1,000 per incident, the company’s Chief Information Security Officer (CISO) has been researching new antivirus software solutions to use and be fully supported for the next two years. The CISO has narrowed down the potential solutions to four candidates that meet all the company’s performance and capability requirements: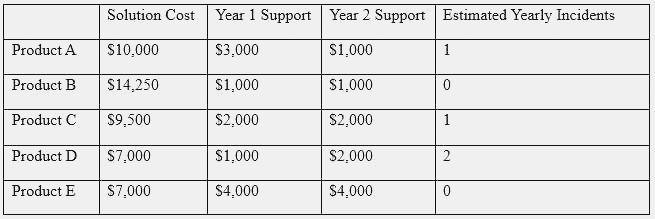
Using the table above, which of the following would be the BEST business-driven choice among five possible solutions?
Answer: E
NEW QUESTION 17
A company has adopted and established a continuous-monitoring capability, which has proven to be effective in vulnerability management, diagnostics, and mitigation. The company wants to increase
the likelihood that it is able to discover and therefore respond to emerging threats earlier in the life cycle.
Which of the following methodologies would BEST help the company to meet this objective? (Choose two.)
Answer: AD
P.S. Certshared now are offering 100% pass ensure CAS-003 dumps! All CAS-003 exam questions have been updated with correct answers: https://www.certshared.com/exam/CAS-003/ (434 New Questions)