
We provide real CAS-004 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass CompTIA CAS-004 Exam quickly & easily. The CAS-004 PDF type is available for reading and printing. You can print more and practice many times. With the help of our CompTIA CAS-004 dumps pdf and vce product and material, you can easily pass the CAS-004 exam.
Check CAS-004 free dumps before getting the full version:
NEW QUESTION 1
A small company recently developed prototype technology for a military program. The company’s security engineer is concerned about potential theft of the newly developed, proprietary information.
Which of the following should the security engineer do to BEST manage the threats proactively?
Answer: D
NEW QUESTION 2
A company is looking to fortify its cybersecurity defenses and is focusing on its network infrastructure. The solution cannot affect the availability of the company’s services to ensure false positives do not drop legitimate traffic.
Which of the following would satisfy the requirement?
Answer: B
Explanation:
Reference: https://subscription.packtpub.com/book/networking-and-servers/9781782174905/5/ch05lvl1sec38/differentiatingbetween-nids-and-nips
NEW QUESTION 3
Ann, a CIRT member, is conducting incident response activities on a network that consists of several hundred virtual servers and thousands of endpoints and users. The network generates more than 10,000 log messages per second. The enterprise belong to a large, web-based cryptocurrency startup, Ann has distilled the relevant information into an easily digestible report for executive management. However, she still needs to collect evidence of the intrusion that caused the incident .
Which of the following should Ann use to gather the required information?
Answer: B
NEW QUESTION 4
A shipping company that is trying to eliminate entire classes of threats is developing an SELinux policy to ensure its custom Android devices are used exclusively for package tracking.
After compiling and implementing the policy, in which of the following modes must the company ensure the devices are configured to run?
Answer: B
Explanation:
Reference: https://source.android.com/security/selinux/customize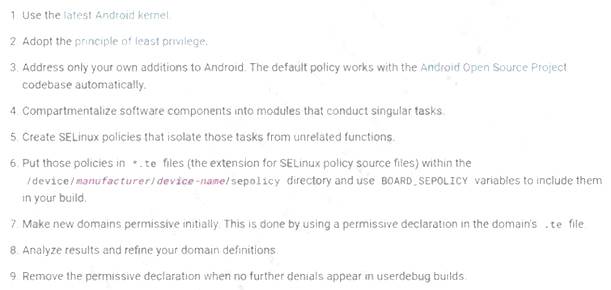
NEW QUESTION 5
A security analyst receives an alert from the SIEM regarding unusual activity on an authorized public SSH jump server. To further investigate, the analyst pulls the event logs directly from /var/log/ auth.log: graphic.ssh_auth_log.
Which of the following actions would BEST address the potential risks by the activity in the logs?
Answer: C
Explanation:
Reference: https://www.rapid7.com/blog/post/2017/10/04/how-to-secure-ssh-server-using-port-knocking-on-ubuntu-linux/
NEW QUESTION 6
A developer implement the following code snippet.
Which of the following vulnerabilities does the code snippet resolve?
Answer: D
NEW QUESTION 7
A technician is reviewing the logs and notices a large number of files were transferred to remote sites over the course of three months. This activity then stopped. The files were transferred via TLSprotected HTTP sessions from systems that do not send traffic to those sites.
The technician will define this threat as:
Answer: A
Explanation:
Reference: https://www.internetsociety.org/deploy360/tls/basics/
NEW QUESTION 8
A security analyst is reviewing the following output:
Which of the following would BEST mitigate this type of attack?
Answer: A
NEW QUESTION 9
The Chief information Officer (CIO) wants to establish a non-banding agreement with a third party that outlines the objectives of the mutual arrangement dealing with data transfers between both organizations before establishing a format partnership .
Which of the follow would MOST likely be used?
Answer: A
NEW QUESTION 10
A developer is creating a new mobile application for a company. The application uses REST API and TLS 1.2 to communicate securely with the external back- end server. Due to this configuration, the company is concerned about HTTPS interception attacks.
Which of the following would be the BEST solution against this type of attack?
Answer: C
Explanation:
Reference: https://cloud.google.com/security/encryption-in-transit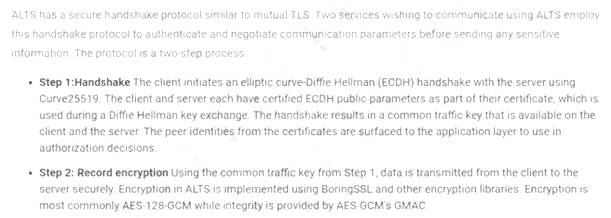
NEW QUESTION 11
After a security incident, a network security engineer discovers that a portion of the company’s sensitive external traffic has been redirected through a secondary ISP that is not normally used.
Which of the following would BEST secure the routes while allowing the network to function in the event of a single provider failure?
Answer: B
NEW QUESTION 12
During a remodel, a company’s computer equipment was moved to a secure storage room with cameras positioned on both sides of the door. The door is locked using a card reader issued by the security team, and only the security team and department managers have access to the room. The company wants to be able to identify any unauthorized individuals who enter the storage room by following an authorized employee.
Which of the following processes would BEST satisfy this requirement?
Answer: A
Explanation:
Reference: https://www.getkisi.com/access-control
NEW QUESTION 13
An application developer is including third-party background security fixes in an application. The fixes seem to resolve a currently identified security issue. However, when the application is released to the public, report come In that a previously vulnerability has returned .
Which of the following should the developer integrate into the process to BEST prevent this type of behavior?
Answer: A
NEW QUESTION 14
A company processes data subject to NDAs with partners that define the processing and storage constraints for the covered data. The agreements currently do not permit moving the covered data to the cloud, and the company would like to renegotiate the terms of the agreements.
Which of the following would MOST likely help the company gain consensus to move the data to the cloud?
Answer: A
NEW QUESTION 15
Clients are reporting slowness when attempting to access a series of load-balanced APIs that do not require authentication. The servers that host the APIs are showing heavy CPU utilization. No alerts are found on the WAFs sitting in front of the APIs. Which of the following should a security engineer recommend to BEST remedy the performance issues in a timely manner?
Answer: C
NEW QUESTION 16
A home automation company just purchased and installed tools for its SOC to enable incident identification and response on software the company develops. The company would like to prioritize defenses against the following attack scenarios:
Unauthorized insertions into application development environments
Authorized insiders making unauthorized changes to environment configurations Which of the following actions will enable the data feeds needed to detect these types of attacks on development environments? (Choose two.)
Answer: CD
NEW QUESTION 17
A company that all mobile devices be encrypted, commensurate with the full disk encryption scheme of
assets, such as workstation, servers, and laptops.
Which of the following will MOST likely be a limiting factor when selecting mobile device managers for the
company?
Answer: A
NEW QUESTION 18
A security analyst is concerned that a malicious piece of code was downloaded on a Linux system. After some research, the analyst determines that the suspected piece of code is performing a lot of input/ output (I/O) on the disk drive.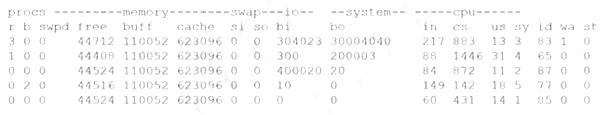
Based on the output above, from which of the following process IDs can the analyst begin an investigation?
Answer: D
NEW QUESTION 19
......
Recommend!! Get the Full CAS-004 dumps in VCE and PDF From Certshared, Welcome to Download: https://www.certshared.com/exam/CAS-004/ (New 128 Q&As Version)