
Passleader offers free demo for CEH-001 exam. "Certified Ethical Hacker (CEH)", also known as CEH-001 exam, is a GAQM Certification. This set of posts, Passing the GAQM CEH-001 exam, will help you answer those questions. The CEH-001 Questions & Answers covers all the knowledge points of the real exam. 100% real GAQM CEH-001 exams and revised by experts!
NEW QUESTION 1
Michael is a junior security analyst working for the National Security Agency (NSA) working primarily on breaking terrorist encrypted messages. The NSA has a number of methods they use to decipher encrypted messages including Government Access to Keys (GAK) and inside informants. The NSA holds secret backdoor keys to many of the encryption algorithms used on the Internet. The problem for the NSA, and Michael, is that terrorist organizations are starting to use custom-built algorithms or obscure algorithms purchased from corrupt governments. For this reason, Michael and other security analysts like him have been forced to find different methods of deciphering terrorist messages. One method that Michael thought of using was to hide malicious code inside seemingly harmless programs. Michael first monitors sites and bulletin boards used by known terrorists, and then he is able to glean email addresses to some of these suspected terrorists. Michael then inserts a stealth keylogger into a mapping program file readme.txt and then sends that as an attachment to the terrorist. This keylogger takes screenshots every 2 minutes and also logs all keyboard activity into a hidden file on the terrorist's computer. Then, the keylogger emails those files to Michael twice a day with a built in SMTP server. What technique has Michael used to disguise this keylogging software?
Answer: C
NEW QUESTION 2
Which type of security document is written with specific step-by-step details?
Answer: B
NEW QUESTION 3
Which of the following identifies the three modes in which Snort can be configured to run?
Answer: A
NEW QUESTION 4
A newly discovered flaw in a software application would be considered which kind of security vulnerability?
Answer: C
NEW QUESTION 5
Which security control role does encryption meet?
Answer: A
NEW QUESTION 6
Harold works for Jacobson Unlimited in the IT department as the security manager. Harold has created a security policy requiring all employees to use complex 14 character passwords. Unfortunately, the members of management do not want to have to use such long complicated passwords so they tell Harold's boss this new password policy should not apply to them. To comply with the management's wishes, the IT department creates
another Windows domain and moves all the management users to that domain. This new domain has a password policy only requiring 8 characters.
Harold is concerned about having to accommodate the managers, but cannot do anything about it. Harold is also concerned about using LanManager security on his network instead of NTLM or NTLMv2, but the many legacy applications on the network prevent using the more secure NTLM and NTLMv2. Harold pulls the SAM files from the DC's on the original domain and the new domain using Pwdump6.
Harold uses the password cracking software John the Ripper to crack users' passwords to make sure they are strong enough. Harold expects that the users' passwords in the original domain will take much longer to crack than the management's passwords in the new domain. After running the software, Harold discovers that the 14 character passwords only took a short time longer to crack than the 8 character passwords.
Why did the 14 character passwords not take much longer to crack than the 8 character passwords?
Answer: D
NEW QUESTION 7
In the context of using PKI, when Sven wishes to send a secret message to Bob, he looks up Bob’s public key in a directory, uses it to encrypt the message before sending it off. Bob then uses his private key to decrypt the message and reads it. No one listening on can decrypt the message.
Anyone can send an encrypted message to Bob but only Bob can read it. Thus, although many people may know Bob’s public key and use it to verify Bob’s signature, they cannot discover Bob’s private key and use it to forge digital signatures.
What does this principle refer to?
Answer: D
Explanation:
PKI uses asymmetric key pair encryption. One key of the pair is the only way to decrypt data encrypted with the other.
NEW QUESTION 8
Blake is in charge of securing all 20 of his company's servers. He has enabled hardware and software firewalls, hardened the operating systems, and disabled all unnecessary services on all the servers. Unfortunately, there is proprietary AS400 emulation software that must run on one of the servers that requires the telnet service to function properly. Blake is especially concerned about this since telnet can be a very large security risk in an organization. Blake is concerned about how this particular server might look to an outside attacker so he decides to perform some footprinting, scanning, and penetration tests on the server. Blake telnets into the server using Port 80 and types in the following command:
HEAD / HTTP/1.0
After pressing enter twice, Blake gets the following results: What has Blake just accomplished?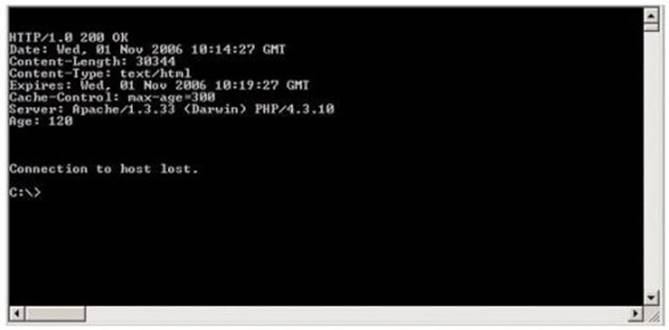
Answer: D
NEW QUESTION 9
ViruXine.W32 virus hides their presence by changing the underlying executable code. This Virus code mutates while keeping the original algorithm intact, the code changes itself each time it runs, but the function of the code (its semantics) will not change at all.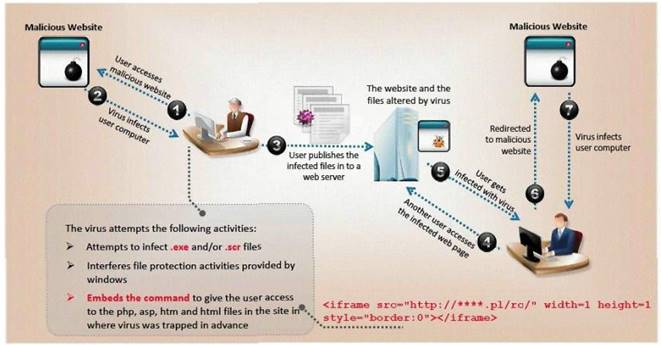
Here is a section of the Virus code:
What is this technique called?
Answer: A
NEW QUESTION 10
What does FIN in TCP flag define?
Answer: B
NEW QUESTION 11
Let's imagine three companies (A, B and C), all competing in a challenging global environment. Company A and B are working together in developing a product that will generate a major competitive advantage for them. Company A has a secure DNS server while company B has a DNS server vulnerable to spoofing. With a spoofing attack on the DNS server of company B, company C gains access to outgoing e-mails from company B. How do you prevent DNS spoofing? (Select the Best Answer.)
Answer: C
Explanation:
Implement DNS Anit-Spoofing measures to prevent DNS Cache Pollution to occur.
NEW QUESTION 12
What are the three phases involved in security testing?
Answer: C
Explanation:
Preparation phase - A formal contract is executed containing non-disclosure of the client's data and legal protection for the tester. At a minimum, it also lists the IP addresses to be tested and time to test.
Conduct phase - In this phase the penetration test is executed, with the tester looking for potential vulnerabilities.
Conclusion phase - The results of the evaluation are communicated to the pre-defined organizational contact, and corrective action is advised.
NEW QUESTION 13
A covert channel is a channel that _____
Answer: A
NEW QUESTION 14
Your boss Tess King is attempting to modify the parameters of a Web-based application in order to alter the SQL statements that are parsed to retrieve data from the database. What would you call such an attack?
Answer: D
Explanation:
This technique is known as SQL injection attack
NEW QUESTION 15
If you receive a RST packet while doing an ACK scan, it indicates that the port is open.(True/False).
Answer: A
Explanation:
When and ACK is sent to an open port, a RST is returned.
NEW QUESTION 16
Jayden is a network administrator for her company. Jayden wants to prevent MAC spoofing on all the Cisco switches in the network. How can she accomplish this?
Answer: D
NEW QUESTION 17
Jess the hacker runs L0phtCrack's built-in sniffer utility that grabs SMB password hashes and stores them for offline cracking. Once cracked, these passwords can provide easy access to whatever network resources the user account has access to. But Jess is not picking up hashes from the network. Why?
Answer: A
NEW QUESTION 18
What is the name of the software tool used to crack a single account on Netware Servers using a dictionary attack?
Answer: B
Explanation:
NWPCrack is the software tool used to crack single accounts on Netware servers.
NEW QUESTION 19
SNMP is a connectionless protocol that uses UDP instead of TCP packets (True or False)
Answer: A
NEW QUESTION 20
In keeping with the best practices of layered security, where are the best places to place intrusion detection/intrusion prevention systems? (Choose two.)
Answer: AC
NEW QUESTION 21
In this attack, a victim receives an e-mail claiming from PayPal stating that their account has been disabled and confirmation is required before activation. The attackers then scam to collect not one but two credit card numbers, ATM PIN number and other personal details.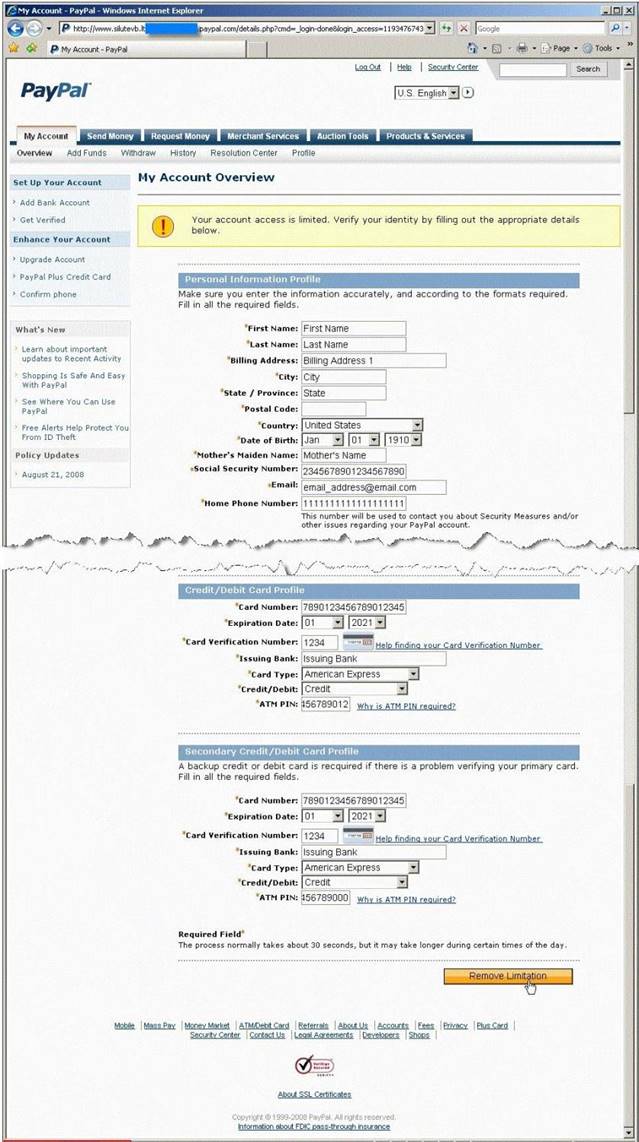
Ignorant users usually fall prey to this scam. Which of the following statement is incorrect
related to this attack?
Answer: D
NEW QUESTION 22
____ is a tool that can hide processes from the process list, can hide files, registry entries, and intercept keystrokes.
Answer: B
Explanation:
Rootkits are tools that can hide processes from the process list, can hide files, registry entries, and intercept keystrokes.
NEW QUESTION 23
Passive reconnaissance involves collecting information through which of the following?
Answer: D
NEW QUESTION 24
While footprinting a network, what port/service should you look for to attempt a zone transfer?
Answer: B
Explanation:
IF TCP port 53 is detected, the opportunity to attempt a zone transfer is there.
NEW QUESTION 25
What does a type 3 code 13 represent?(Choose two.
Answer: BD
Explanation:
Type 3 code 13 is destination unreachable administratively prohibited. This type of message is typically returned from a device blocking a port.
NEW QUESTION 26
......
Recommend!! Get the Full CEH-001 dumps in VCE and PDF From 2passeasy, Welcome to Download: https://www.simply-pass.com/{factory}-exam/{productsort}-dumps.html (New 878 Q&As Version)