
Exam Code: CEH-001 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Certified Ethical Hacker (CEH)
Certification Provider: GAQM
Free Today! Guaranteed Training- Pass CEH-001 Exam.
Online GAQM CEH-001 free dumps demo Below:
NEW QUESTION 1
John is using a special tool on his Linux platform that has a signature database and is therefore able to detect hundred of vulnerabilities in UNIX, Windows, and commonly-used web CGI scripts. Additionally, the database detects DDoS zombies and Trojans. What would be the name of this multifunctional tool?
Answer: C
Explanation:
Nessus is the world's most popular vulnerability scanner, estimated to be used by over 75, 000 organizations world-wide. Nmap is mostly used for scanning, not for detecting vulnerabilities. Hping is a free packet generator and analyzer for the TCP/IP protocol and make is used to automatically build large applications on the *nix plattform.
NEW QUESTION 2
You work as security technician at XYZ.com. While doing web application testing, you might be required to look through multiple web pages online which can take a long time. Which of the processes listed below would be a more efficient way of doing this type of validation?
Answer: B
Explanation:
Wget is a utility used for mirroring websites, get* doesn’t work, as for the actual FTP command to work there needs to be a space between get and * (ie. get *), get(); is just bogus, that’s a C function that’s written 100% wrong. mget is a command used from “within” ftp itself, ruling out A. Which leaves B use wget, which is designed for mirroring and download files, especially web pages, if used with the –R option (ie. wget –R www.XYZ.com) it could mirror a site, all expect protected portions of course.
Note: GNU Wget is a free network utility to retrieve files from the World Wide Web using HTTP and FTP and can be used to make mirrors of archives and home pages thus enabling work in the background, after having logged off.
NEW QUESTION 3
Which type of antenna is used in wireless communication?
Answer: A
NEW QUESTION 4
What type of attack is shown here?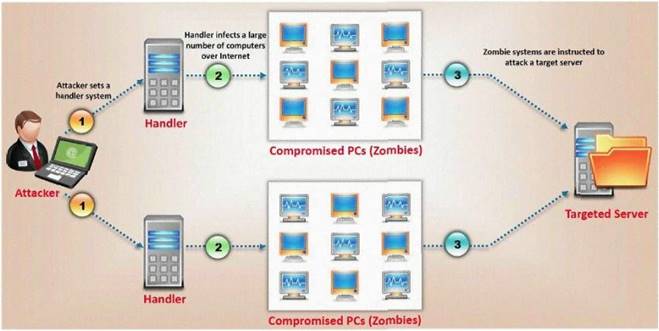
Answer: D
Explanation:
We think this is a DDoS attack not DoS because the attack is initialed in multiple zombies not single machine.
NEW QUESTION 5
You have performed the traceroute below and notice that hops 19 and 20 both show the same IP address.
What can be inferred from this output?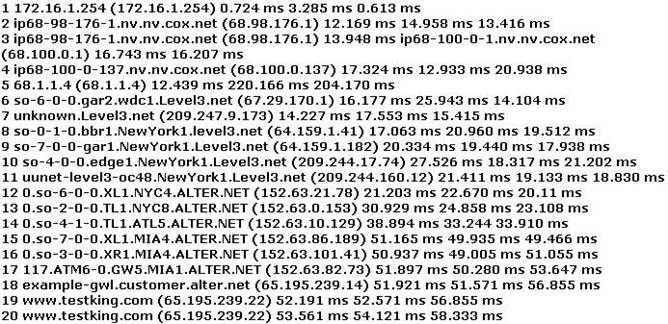
Answer: B
NEW QUESTION 6
Pentest results indicate that voice over IP traffic is traversing a network. Which of the following tools will decode a packet capture and extract the voice conversations?
Answer: A
NEW QUESTION 7
_____ is the process of converting something from one representation to the simplest form. It deals with the way in which systems convert data from one form to another.
Answer: A
Explanation:
Canonicalization (abbreviated c14n) is the process of converting data that has more than one possible representation into a "standard" canonical representation. This can be done to compare different representations for equivalence, to count the number of distinct data structures (e.g., in combinatorics), to improve the efficiency of various algorithms by eliminating repeated calculations, or to make it possible to impose a meaningful sorting order.
NEW QUESTION 8
A network security administrator is worried about potential man-in-the-middle attacks when users access a corporate web site from their workstations. Which of the following is the best remediation against this type of attack?
Answer: C
NEW QUESTION 9
Which type of hacker represents the highest risk to your network?
Answer: C
NEW QUESTION 10
Which of the following processes of PKI (Public Key Infrastructure) ensures that a trust relationship exists and that a certificate is still valid for specific operations?
Answer: B
NEW QUESTION 11
After gaining access to the password hashes used to protect access to a web based application, knowledge of which cryptographic algorithms would be useful to gain access to the application?
Answer: A
NEW QUESTION 12
A newly discovered flaw in a software application would be considered which kind of security vulnerability?
Answer: C
NEW QUESTION 13
An NMAP scan of a server shows port 25 is open. What risk could this pose?
Answer: D
NEW QUESTION 14
While checking the settings on the internet browser, a technician finds that the proxy server settings have been checked and a computer is trying to use itself as a proxy server. What specific octet within the subnet does the technician see?
Answer: B
NEW QUESTION 15
You are scanning into the target network for the first time. You find very few conventional ports open. When you attempt to perform traditional service identification by connecting to the open ports, it yields either unreliable or no results. You are unsure of which protocols are being used. You need to discover as many different protocols as possible.
Which kind of scan would you use to achieve this? (Choose the best answer)
Answer: D
Explanation:
Running Nmap with the –sO switch will do a IP Protocol Scan. The IP protocol scan is a bit different than the other nmap scans. The IP protocol scan is searching for additional IP protocols in use by the remote station, such as ICMP, TCP, and UDP. If a router is scanned, additional IP protocols such as EGP or IGP may be identified.
NEW QUESTION 16
Tess King, the evil hacker, is purposely sending fragmented ICMP packets to a remote target. The total size of this ICMP packet once reconstructed is over 65, 536 bytes. From the information given, what type of attack is Tess King attempting to perform?
Answer: C
Explanation:
Reference: http://insecure.org/sploits/ping-o-death.html
NEW QUESTION 17
The network administrator for a company is setting up a website with e-commerce capabilities. Packet sniffing is a concern because credit card information will be sent electronically over the Internet. Customers visiting the site will need to encrypt the data with HTTPS. Which type of certificate is used to encrypt and decrypt the data?
Answer: A
NEW QUESTION 18
"Testing the network using the same methodologies and tools employed by attackers" Identify the correct terminology that defines the above statement.
Answer: B
NEW QUESTION 19
Which of the following LM hashes represents a password of less than 8 characters?
Answer: BE
Explanation:
Any password that is shorter than 8 characters will result in the hashing of 7 null bytes, yielding the constant value of 0xAAD3B435B51404EE, hence making it easy to identify short passwords on sight.
NEW QUESTION 20
A company firewall engineer has configured a new DMZ to allow public systems to be located away from the internal network. The engineer has three security zones set:
Untrust (Internet) – (Remote network = 217.77.88.0/24) DMZ (DMZ) – (11.12.13.0/24)
Trust (Intranet) – (192.168.0.0/24)
The engineer wants to configure remote desktop access from a fixed IP on the remote network to a remote desktop server in the DMZ. Which rule would best fit this requirement?
Answer: B
NEW QUESTION 21
......
Thanks for reading the newest CEH-001 exam dumps! We recommend you to try the PREMIUM Dumpscollection.com CEH-001 dumps in VCE and PDF here: https://www.dumpscollection.net/dumps/CEH-001/ (878 Q&As Dumps)