
Proper study guides for Regenerate GAQM Certified Ethical Hacker (CEH) certified begins with GAQM CEH-001 preparation products which designed to deliver the Precise CEH-001 questions by making you pass the CEH-001 test at your first time. Try the free CEH-001 demo right now.
GAQM CEH-001 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
What does black box testing mean?
Answer: B
Explanation:
Black box testing is conducted when you have no knowledge of the environment. It is more time consuming and expensive.
NEW QUESTION 2
A hacker was able to sniff packets on a company's wireless network. The following information was discovereD.
The Key 10110010 01001011
The Cyphertext 01100101 01011010
Using the Exlcusive OR, what was the original message?
Answer: B
NEW QUESTION 3
Which of the following Registry location does a Trojan add entries to make it persistent on Windows 7? (Select 2 answers)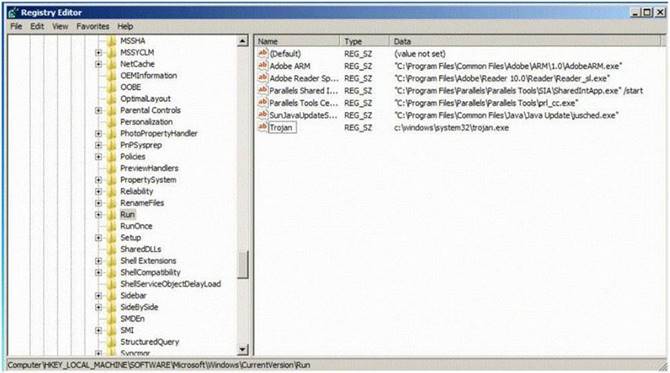
Answer: AD
NEW QUESTION 4
The Slammer Worm exploits a stack-based overflow that occurs in a DLL implementing the Resolution Service.
Which of the following Database Server was targeted by the slammer worm?
Answer: B
Explanation:
W32.Slammer is a memory resident worm that propagates via UDP Port 1434 and exploits a vulnerability in SQL Server 2000 systems and systems with MSDE 2000 that have not applied the patch released by Microsoft Security Bulletin MS02-039.
NEW QUESTION 5
The programmers on your team are analyzing the free, open source software being used to run FTP services on a server. They notice that there is an excessive number of fgets() and gets() on the source code. These C++ functions do not check bounds.
What kind of attack is this program susceptible to?
Answer: A
Explanation:
C users must avoid using dangerous functions that do not check bounds unless they've ensured that the bounds will never get exceeded. A buffer overflow occurs when you write a set of values (usually a string of characters) into a fixed length buffer and write at least one value outside that buffer's boundaries (usually past its end). A buffer overflow can occur when reading input from the user into a buffer, but it can also occur during other kinds of processing in a program.
NEW QUESTION 6
A security consultant is trying to bid on a large contract that involves penetration testing and reporting. The company accepting bids wants proof of work so the consultant prints out several audits that have been performed. Which of the following is likely to occur as a result?
Answer: B
NEW QUESTION 7
Every company needs a formal written document which spells out to employees precisely what they are allowed to use the company's systems for, what is prohibited, and what will happen to them if they break the rules. Two printed copies of the policy should be given to every employee as soon as possible after they join the organization. The employee should be asked to sign one copy, which should be safely filed by the company. No one should be allowed to use the company's computer systems until they have signed the policy in acceptance of its terms. What is this document called?
Answer: B
NEW QUESTION 8
A penetration tester is hired to do a risk assessment of a company's DMZ. The rules of engagement states that the penetration test be done from an external IP address with no prior knowledge of the internal IT systems. What kind of test is being performed?
Answer: D
NEW QUESTION 9
What framework architecture is shown in this exhibit?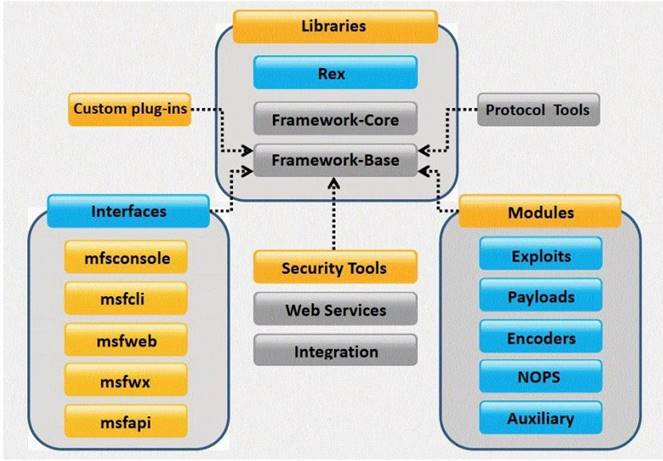
Answer: B
NEW QUESTION 10
Let's imagine three companies (A, B and C), all competing in a challenging global environment. Company A and B are working together in developing a product that will generate a major competitive advantage for them. Company A has a secure DNS server while company B has a DNS server vulnerable to spoofing. With a spoofing attack on the DNS server of company B, company C gains access to outgoing e-mails from company B. How do you prevent DNS spoofing? (Select the Best Answer.)
Answer: C
Explanation:
Implement DNS Anit-Spoofing measures to prevent DNS Cache Pollution to occur.
NEW QUESTION 11
A zone file consists of which of the following Resource Records (RRs)?
Answer: D
Explanation:
The zone file typically contains the following records: SOA – Start Of Authority
NS – Name Server record MX – Mail eXchange record A – Address record
NEW QUESTION 12
What type of port scan is shown below?
Answer: B
NEW QUESTION 13
Fingerprinting an Operating System helps a cracker because:
Answer: D
Explanation:
When a cracker knows what OS and Services you use he also knows which exploits might work on your system. If he would have to try all possible exploits for all possible Operating Systems and Services it would take too long time and the possibility of being detected increases.
NEW QUESTION 14
During a wireless penetration test, a tester detects an access point using WPA2 encryption. Which of the following attacks should be used to obtain the key?
Answer: A
NEW QUESTION 15
An Evil Cracker is attempting to penetrate your private network security. To do this, he must not be seen by your IDS, as it may take action to stop him. What tool might he use to bypass the IDS?
Select the best answer.
Answer: C
Explanation:
Explanations:
Firewalking is a way to disguise a portscan. Thus, firewalking is not a tool, but a method of
conducting a port scan in which it can be hidden from some firewalls. Synamtec Man-Hunt is an IDS, not a tool to evade an IDS.
Fragrouter is a tool that can take IP traffic and fragment it into multiple pieces. There is a legitimate reason that fragmentation is done, but it is also a technique that can help an attacker to evade detection while Fragids is a made-up tool and does not exist.
NEW QUESTION 16
What is the main advantage that a network-based IDS/IPS system has over a host-based solution?
Answer: A
NEW QUESTION 17
Which definition among those given below best describes a covert channel?
Answer: B
Explanation:
A covert channel is described as: "any communication channel that can be exploited by a process to transfer information in a manner that violates the systems security policy." Essentially, it is a method of communication that is not part of an actual computer system design, but can be used to transfer information to users or system processes that normally would not be allowed access to the information.
NEW QUESTION 18
A Trojan horse is a destructive program that masquerades as a benign application. The software initially appears to perform a desirable function for the user prior to installation
and/or execution, but in addition to the expected function steals information or harms the system.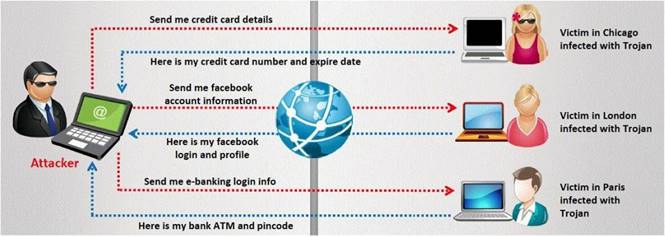
The challenge for an attacker is to send a convincing file attachment to the victim, which gets easily executed on the victim machine without raising any suspicion. Today's end users are quite knowledgeable about malwares and viruses. Instead of sending games and fun executables, Hackers today are quite successful in spreading the Trojans using Rogue security software.
What is Rogue security software?
Answer: B
NEW QUESTION 19
What type of session hijacking attack is shown in the exhibit?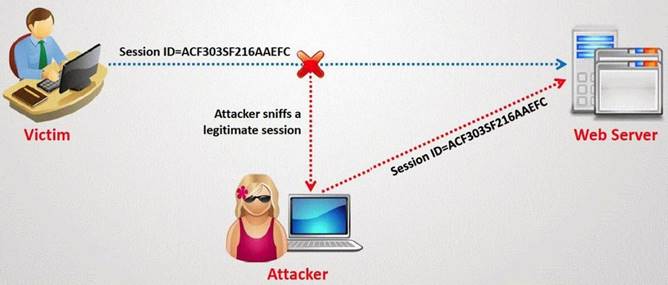
Answer: A
NEW QUESTION 20
Which of the following buffer overflow exploits are related to Microsoft IIS web server? (Choose three)
Answer: ABC
Explanation:
Both the buffer overflow in the Internet Printing Protocol and the ISAPI
extension buffer overflow is explained in Microsoft Security Bulletin MS01-023. The Code Red worm was a computer worm released on the Internet on July 13, 2001. It attacked computers running Microsoft's IIS web server.
NEW QUESTION 21
......
Thanks for reading the newest CEH-001 exam dumps! We recommend you to try the PREMIUM Certleader CEH-001 dumps in VCE and PDF here: https://www.certleader.com/CEH-001-dumps.html (878 Q&As Dumps)