
It is impossible to pass GAQM CEH-001 exam without any help in the short term. Come to Pass4sure soon and find the most advanced, correct and guaranteed GAQM CEH-001 practice questions. You will get a surprising result by our Improve Certified Ethical Hacker (CEH) practice guides.
Free demo questions for GAQM CEH-001 Exam Dumps Below:
NEW QUESTION 1
Bluetooth uses which digital modulation technique to exchange information between paired devices?
Answer: A
NEW QUESTION 2
Your XYZ trainee Sandra asks you which are the four existing Regional Internet Registry (RIR's)?
Answer: B
Explanation:
All other answers include non existing organizations (PICNIC, NANIC, LATNIC). See http://www.arin.net/library/internet_info/ripe.html
NEW QUESTION 3
How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
Answer: B
Explanation:
When looking at an extracted LM hash, you will sometimes observe that the right most portion is always the same. This is padding that has been added to a password that is less than 8 characters long.
NEW QUESTION 4
Here is the ASCII Sheet.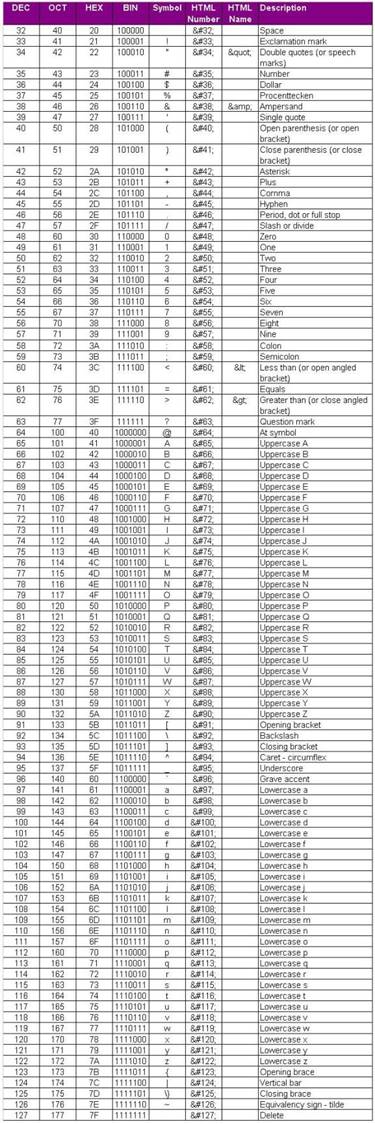
You want to guess the DBO username juggyboy (8 characters) using Blind SQL Injection
technique.
What is the correct syntax?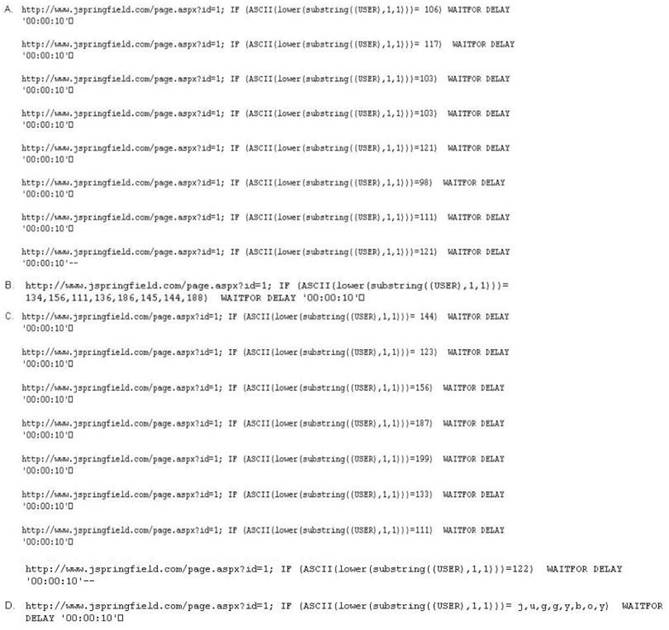
Answer: A
NEW QUESTION 5
SNMP is a connectionless protocol that uses UDP instead of TCP packets (True or False)
Answer: A
NEW QUESTION 6
Which of the following guidelines or standards is associated with the credit card industry?
Answer: D
NEW QUESTION 7
When discussing passwords, what is considered a brute force attack?
Answer: A
Explanation:
Brute force cracking is a time consuming process where you try every possible combination of letters, numbers, and characters until you discover a match.
NEW QUESTION 8
An attacker runs netcat tool to transfer a secret file between two hosts.
Machine A: netcat -l -p 1234 < secretfile Machine B: netcat 192.168.3.4 > 1234
He is worried about information being sniffed on the network. How would the attacker use netcat to encrypt the information before transmitting onto the wire?
Answer: D
Explanation:
Netcat cannot encrypt the file transfer itself but would need to use a third party application to encrypt/decrypt like openssl. Cryptcat is the standard netcat enhanced with twofish encryption.
NEW QUESTION 9
What is the name of the software tool used to crack a single account on Netware Servers using a dictionary attack?
Answer: B
Explanation:
NWPCrack is the software tool used to crack single accounts on Netware servers.
NEW QUESTION 10
Jacob would like your advice on using a wireless hacking tool that can save him time and get him better results with lesser packets. You would like to recommend a tool that uses KoreK's implementation. Which tool would you recommend from the list below?
Answer: C
Explanation:
Implementing KoreK's attacks as well as improved FMS, aircrack provides the fastest and most effective statistical attacks available.John the Ripper is a password cracker, Kismet is an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system, and
NEW QUESTION 11
How many bits encryption does SHA-1 use?
Answer: D
NEW QUESTION 12
Jackson discovers that the wireless AP transmits 128 bytes of plaintext, and the station responds by encrypting the plaintext. It then transmits the resulting ciphertext using the same key and cipher that are used by WEP to encrypt subsequent network traffic. What authentication mechanism is being followed here?
Answer: C
NEW QUESTION 13
A computer technician is using a new version of a word processing software package when it is discovered that a special sequence of characters causes the entire computer to crash. The technician researches the bug and discovers that no one else experienced the problem. What is the appropriate next step?
Answer: D
NEW QUESTION 14
Jack Hacker wants to break into Brown Co.'s computers and obtain their secret double fudge cookie recipe. Jack calls Jane, an accountant at Brown Co., pretending to be an administrator from Brown Co. Jack tells Jane that there has been a problem with some accounts and asks her to verify her password with him ''just to double check our records.'' Jane does not suspect anything amiss, and parts with her password. Jack can now access Brown Co.'s computers with a valid user name and password, to steal the cookie recipe. What kind of attack is being illustrated here?
Answer: C
NEW QUESTION 15
What is one thing a tester can do to ensure that the software is trusted and is not changing
or tampering with critical data on the back end of a system it is loaded on?
Answer: D
NEW QUESTION 16
A penetration tester was hired to perform a penetration test for a bank. The tester began searching for IP ranges owned by the bank, performing lookups on the bank's DNS servers, reading news articles online about the bank, watching what times the bank employees come into work and leave from work, searching the bank's job postings (paying special attention to IT related jobs), and visiting the local dumpster for the bank's corporate office. What phase of the penetration test is the tester currently in?
Answer: D
NEW QUESTION 17
In an attempt to secure his wireless network, Bob implements a VPN to cover the wireless communications. Immediately after the implementation, users begin complaining about how slow the wireless network is. After benchmarking the network’s speed. Bob discovers that throughput has dropped by almost half even though the number of users has remained the same.
Why does this happen in the VPN over wireless implementation?
Answer: B
Explanation:
By applying VPN the access point will have to recalculate all headers destined for client and from clients twice.
NEW QUESTION 18
While footprinting a network, what port/service should you look for to attempt a zone transfer?
Answer: B
Explanation:
IF TCP port 53 is detected, the opportunity to attempt a zone transfer is there.
NEW QUESTION 19
Jess the hacker runs L0phtCrack's built-in sniffer utility that grabs SMB password hashes and stores them for offline cracking. Once cracked, these passwords can provide easy access to whatever network resources the user account has access to. But Jess is not picking up hashes from the network. Why?
Answer: A
NEW QUESTION 20
What is the proper response for a NULL scan if the port is open?
Answer: F
Explanation:
A NULL scan will have no response if the port is open.
NEW QUESTION 21
......
P.S. Allfreedumps.com now are offering 100% pass ensure CEH-001 dumps! All CEH-001 exam questions have been updated with correct answers: https://www.allfreedumps.com/CEH-001-dumps.html (878 New Questions)