
Cause all that matters here is passing the Isaca CISA exam. Cause all that you need is a high score of CISA Isaca CISA exam. The only one thing you need to do is downloading Actualtests CISA exam study guides now. We will not let you down with our money-back guarantee.
Check CISA free dumps before getting the full version:
NEW QUESTION 1
Which of the following should be seen as one of the most significant factors considered when determining the frequency of IS audits within your organization?
Answer: D
Explanation:
You use a risk assessment process to describe and analyze the potential audit risks inherent in a given line of business. You should update such risk assessment at least annually to reflect changes. The level and nature of risk should be the most significant factors to be considered when determining the frequency of audits.
NEW QUESTION 2
Which of the following does a lack of adequate security controls represent?
Answer: D
Explanation:
The lack of adequate security controls represents a vulnerability, exposing sensitive information and data to the risk of malicious damage, attack or unauthorized access by hackers. This could result in a loss of sensitive information and lead to theloss of goodwill for the organization. A succinct definition of risk is provided by the Guidelines for the Management of IT Security published by the International Organization for Standardization (ISO), which defines risk as the 'potential that a given threat will exploit the vulnerability of an asset or group of assets to cause loss or damage to the assets.' The various elements of the definition are vulnerability, threat, asset and impact. Lack of adequate security functionalityin this context is a vulnerability.
NEW QUESTION 3
During an exit interview, in cases where there is disagreement regarding the impact of a finding, an IS auditor should:
Answer: B
Explanation:
If the auditee disagrees with the impact of a finding, it is important for an IS auditor to elaborate and clarify the risks and exposures, as the auditee may not fully appreciate the magnitude of the exposure. The goal should be to enlighten the auditee or uncover new information of which an IS auditor may not have been aware. Anything that appears to threaten the auditee will lessen effective communications and set up an adversarial relationship. By the same token, an IS auditor should not automatically agree just because the auditee expresses an alternate point of view.
NEW QUESTION 4
As a driver of IT governance, transparency of IT's cost, value and risks is primarily achieved through:
Answer: A
Explanation:
Performance measurement includes setting and monitoring measurable objectives of what the IT processes need to deliver {process outcome) and how they deliver it (process capability and performance). Strategic alignment primarily focuses on ensuring linkage of business and IT plans. Value delivery is about executing the value proposition throughout the delivery cycle. Resource management is about the optimal investment in and proper management of critical IT resources. Transparency is primarily achieved through performance measurement as it provides information to the stakeholders on how well the enterprise is performing when compared to objectives.
NEW QUESTION 5
Which of the following encrypt/decrypt steps provides the GREATEST assurance of achieving confidentiality, message integrity and nonrepudiation by either sender or recipient?
Answer: D
Explanation:
Most encrypted transactions use a combination of private keys, public keys, secret keys, hash functions and digital certificates to achieve confidentiality, message integrity and nonrepudiation by either sender or recipient. The recipient uses the sender's public key to decrypt the prehash code into a posthash code, which when equaling the prehash code, verifies the identity of the sender and that the message has not been changed in route; this would provide the greatest assurance. Each sender and recipient has a private key known only to themselves and a public key, which can be known by anyone. Each encryption/decryption process requires at least one public key and one private key, and both must be from the same party. A single, secret key is used to encrypt the message, because secret key encryption requires less processing power than using public and private keys. A digital certificate, signed by a certificate authority, validates senders' and recipients' public keys.
NEW QUESTION 6
Which of the following should be included in an organization's IS security policy?
Answer: B
Explanation:
The security policy provides the broad framework of security, as laid down and approved by senior management. It includes a definition of those authorized to grant access and the basis for granting the access. Choices A, B and C are more detailed than that which should be included in a policy.
NEW QUESTION 7
Which of the following would be the MOST effective audit technique for identifying segregation of duties violations in a new enterprise resource planning (ERP) implementation?
Answer: C
Explanation:
Since the objective is to identify violations in segregation of duties, it is necessary to define the logic that will identify conflicts in authorization. A program could be developed to identify these conflicts. A report of security rights in the enterprise resource planning (ERP) system would be voluminous and time consuming to review; therefore, this technique is not as effective as building a program. As complexities increase, it becomes more difficult to verify the effectiveness of the systems and complexity is not, in itself, a link to segregation of duties. It is good practice to review recent access rights violation cases; however, it may require a significant amount of time to truly identify which violations actually resulted froman inappropriate segregation of duties.
NEW QUESTION 8
Which of the following refers to a method of bypassing normal system authentication procedures?
Answer: F
Explanation:
A backdoor is a method of bypassing normal authentication procedures. Many computer manufacturers used to preinstall backdoors on their systems to provide technical support for customers. Hackers typically use backdoors to secure remote access to a computer, while attempting to remain hidden from casual inspection. To install backdoors, hackers prefer to use either Trojan horse or computer worm.
NEW QUESTION 9
A structured walk-through test of a disaster recovery plan involves:
Answer: B
Explanation:
A structured walk-through test of a disaster recovery plan involves representatives from each of the functional areas coming together to review the plan to determine if the plan pertaining to their area is accurate and complete and can be implemented when required. Choice B is a simulation test to prepare and train the personnel who will be required to respond to disasters and disruptions. Choice C is a form of parallel testing to ensure that critical systems will perform satisfactorily in the alternate site. Choice D is a checklist test.
NEW QUESTION 10
In the course of performing a risk analysis, an IS auditor has identified threats and
potential impacts. Next, the IS auditor should:
Answer: D
Explanation:
It is important for an IS auditor to identify and evaluate the existing controls and security once the potential threats and possible impacts are identified. Upon completion of an audit an IS auditor should describe and discuss with management the threats and potential impacts on the assets.
NEW QUESTION 11
An IS auditor reviewing an accounts payable system discovers that audit logs are not being reviewed. When this issue is raised with management the response is that additional controls are not necessary because effective system access controls are inplace. The BEST response the auditor can make is to:
Answer: C
Explanation:
Experience has demonstrated that reliance purely on preventative controls is dangerous. Preventative controls may not prove to be as strong as anticipated or their effectiveness can deteriorate over time. Evaluating the cost of controls versus the quantum of risk is a valid management concern. However, in a high-risk system a comprehensive control framework is needed, intelligent design should permit additional detective and corrective controls to be established that don't have high ongoing costs, e.g., automated interrogation of logs to highlight suspicious individual transactions or data patterns. Effective access controls are, in themselves, a positive but, for reasons outlined above, may not sufficiently compensate for other control weaknesses. In this situation the IS auditor needs to be proactive. The IS auditor has a fundamental obligation to point out control weaknesses that give rise to unacceptable risks to the organization and work with management to have these corrected. Reviewing background checks on accounts payable staff does not provide evidence that fraud will not occur.
NEW QUESTION 12
During a disaster recovery test, an IS auditor observes that the performance of the
disaster recovery site's server is slow. To find the root cause of this, the IS auditor should FIRST review the:
Answer: D
Explanation:
Since the configuration of the system is the most probable cause, the IS auditor should review that first. If the issue cannot be clarified, the IS auditor should then review the event error log. The disaster recovery test plan and the disaster recovery plan (DRP) would not contain information about the system configuration.
NEW QUESTION 13
Assuming this diagram represents an internal facility and the organization is implementing a firewall protection program, where should firewalls be installed? 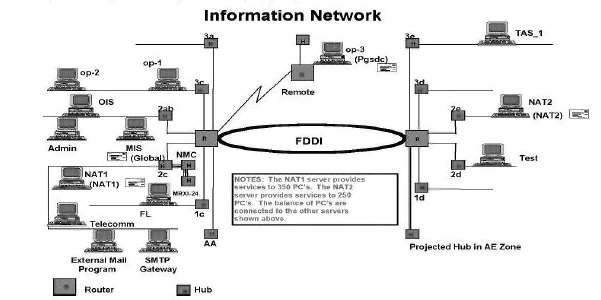
Answer: D
Explanation:
The objective of a firewall is to protect a trusted network from an untrusted network; therefore, locations needing firewall implementations would be at the existence of the external connections. All other answers are incomplete or represent internal connections.
NEW QUESTION 14
Who is responsible for the overall direction, costs, and timetables for systems-development projects?
Answer: B
Explanation:
The project steering committee is responsible for the overall direction, costs, and timetables for systems-development projects.
NEW QUESTION 15
Which of the following recovery strategies is MOST appropriate for a business having multiple offices within a region and a limited recovery budget?
Answer: C
Explanation:
For a business having many offices within a region, a reciprocal arrangement among its offices would be most appropriate. Each office could be designated as a recovery site for some other office. This would be the least expensive approach to providing an acceptable level of confidence. A hot site maintained by the business would be a costly solution but would provide a high degree of confidence. Multiple cold sites leased for the multiple offices would lead to a costly solution with a high degree of confidence. A third-party facility for recovery is provided by a traditional hot site. This would be a costly approach providing a high degree of confidence.
NEW QUESTION 16
Which of the following provides the GREATEST assurance of message authenticity?
Answer: B
Explanation:
Encrypting the prehash code using the sender's private key provides assurance of the authenticity of the message. Mathematically deriving the prehash code provides integrity to the message. Encrypting the prehash code and the message using the secretkey provides confidentiality.
NEW QUESTION 17
Which of the following would effectively verify the originator of a transaction?
Answer: D
Explanation:
A digital signature is an electronic identification of a person, created by using a public key algorithm, to verify to a recipient the identity of the source of a transaction and the integrity of its content. Since they are a 'shared secret' between the user and the system itself, passwords are considered a weaker means of authentication. Encrypting the transaction with the recipient's public key will provide confidentiality for the information, while using a portable document format(PDF) will probe the integrity of the content but not necessarily authorship.
NEW QUESTION 18
Which of the following is the MOST important action in recovering from a cyberattack?
Answer: C
Explanation:
The most important key step in recovering from cyberattacks is the execution of a business continuity plan to quickly and cost-effectively recover critical systems, processes and datA. The incident response team should exist prior to a cyberattack. When a cyberattack is suspected, cyberforensics investigators should be used to set up alarms, catch intruders within the network, and track and trace them over the Internet. After taking the above steps, an organization may have a residual risk thatneeds to be insured and claimed for traditional and electronic exposures.
NEW QUESTION 19
......
100% Valid and Newest Version CISA Questions & Answers shared by Dumps-hub.com, Get Full Dumps HERE: https://www.dumps-hub.com/CISA-dumps.html (New 980 Q&As)