
Master the ECSAv10 EC-Council Certified Security Analyst (ECSA) v10 : Penetration Testing content and be ready for exam day success quickly with this Pass4sure ECSAv10 free exam questions. We guarantee it!We make it a reality and give you real ECSAv10 questions in our EC-Council ECSAv10 braindumps.Latest 100% VALID EC-Council ECSAv10 Exam Questions Dumps at below page. You can use our EC-Council ECSAv10 braindumps and pass your exam.
Free ECSAv10 Demo Online For EC-Council Certifitcation:
NEW QUESTION 1
HTTP protocol specifies that arbitrary binary characters can be passed within the URL by using %xx notation, where 'xx' is the
Answer: D
NEW QUESTION 2
You are running through a series of tests on your network to check for any security vulnerabilities. After normal working hours, you initiate a DoS attack against your external firewall. The firewall quickly freezes up and becomes unusable.
You then initiate an FTP connection from an external IP into your internal network. The connection is successful even though you have FTP blocked at the external firewall. What has happened?
Answer: A
NEW QUESTION 3
Which of the following approaches to vulnerability assessment relies on the administrator providing baseline of system configuration and then scanning continuously without incorporating any information found at the time of scanning?
Answer: C
NEW QUESTION 4
What is a good security method to prevent unauthorized users from "tailgating"?
Answer: B
NEW QUESTION 5
The objective of social engineering pen testing is to test the strength of human factors in a security chain within the organization. It is often used to raise the level of security awareness among employees.
The tester should demonstrate extreme care and professionalism during a social engineering pen test as it might involve legal issues such as violation of privacy and may result in an embarrassing situation for the organization.
Which of the following methods of attempting social engineering is associated with bribing, handing out gifts, and becoming involved in a personal relationship to befriend someone inside the company?
Answer: A
NEW QUESTION 6
Which of the following statements is true about Multi-Layer Intrusion Detection Systems (mIDSs)?
Answer: A
NEW QUESTION 7
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast.
On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away. Eventually the wireless signal shows back up, but drops intermittently.
What could be Tyler issue with his home wireless network?
Answer: A
NEW QUESTION 8
Which one of the following 802.11 types uses either FHSS or DSSS for modulation?
Answer: D
NEW QUESTION 9
Which of the following is a framework of open standards developed by the Internet Engineering Task Force (IETF) that provides secure transmission of the sensitive data over an unprotected medium, such as the Internet?
Answer: D
NEW QUESTION 10
What is a difference between host-based intrusion detection systems (HIDS) and network-based intrusion detection systems (NIDS)?
Answer: C
NEW QUESTION 11
Which of the following statement holds true for TCP Operation?
Answer: D
NEW QUESTION 12
What are the 6 core concepts in IT security?
Answer: B
NEW QUESTION 13
NTP protocol is used to synchronize the system clocks of computers with a remote time server or time source over a network. Which one of the following ports is used by NTP as its transport layer?
Answer: C
NEW QUESTION 14
After attending a CEH security seminar, you make a list of changes you would like to perform on your
network to increase its security. One of the first things you change is to switch the Restrict Anonymous setting from 0 to 1 on your servers. This, as you were told, would prevent anonymous users from establishing a null session on the server.
Using User info tool mentioned at the seminar, you succeed in establishing a null session with one of the servers. Why is that?
Answer: A
NEW QUESTION 15
In the process of hacking a web application, attackers manipulate the HTTP requests to subvert the application authorization schemes by modifying input fields that relate to the user ID, username, access group, cost, file names, file identifiers, etc.
They first access the web application using a low privileged account and then escalate privileges to access protected resources. What attack has been carried out?
Answer: B
NEW QUESTION 16
Simon is a former employee of Trinitron XML Inc. He feels he was wrongly terminated and wants to hack into his former company's network. Since Simon remembers some of the server names, he attempts to run the AXFR and IXFR commands using DIG.
What is Simon trying to accomplish here?
Answer: D
NEW QUESTION 17
You are carrying out the last round of testing for your new website before it goes live. The website has
many dynamic pages and connects to a SQL backend that accesses your product inventory in a database. You come across a web security site that recommends inputting the following code into a search field on web pages to check for vulnerabilities:
<script>alert("This is a test.")</script>
When you type this and click on search, you receive a pop-up window that says: "This is a test."
What is the result of this test?
Answer: B
NEW QUESTION 18
Julia is a senior security analyst for Berber Consulting group. She is currently working on a contract for a small accounting firm in Florida. They have given her permission to perform social engineering attacks on the company to see if their in-house training did any good. Julia calls the main number for the accounting firm and talks to the receptionist. Julia says that she is an IT technician from the company's main office in Iowa.
She states that she needs the receptionist's network username and password to troubleshoot a problem they are having. Julia says that Bill Hammond, the CEO of the company, requested this information. After hearing the name of the CEO, the receptionist gave Julia all the information she asked for.
What principal of social engineering did Julia use?
Answer: A
NEW QUESTION 19
Which one of the following log analysis tools is used for analyzing the server’s log files?
Answer: C
NEW QUESTION 20
An antenna is a device that is designed to transmit and receive the electromagnetic waves that are generally called radio waves. Which one of the following types of antenna is developed from waveguide technology?
Answer: B
NEW QUESTION 21
Which one of the following scans starts, but does not complete the TCP handshake sequence for each port selected, and it works well for direct scanning and often works well through firewalls?
Answer: A
NEW QUESTION 22
Jim performed a vulnerability analysis on his network and found no potential problems. He runs another utility that executes exploits against his system to verify the results of the vulnerability test. The second utility executes five known exploits against his network in which the vulnerability analysis said were not exploitable.
What kind of results did Jim receive from his vulnerability analysis?
Answer: B
NEW QUESTION 23
Which of the following is the range for assigned ports managed by the Internet Assigned Numbers Authority (IANA)?
Answer: D
NEW QUESTION 24
Besides the policy implications of chat rooms, Internet Relay Chat (IRC) is frequented by attackers and used as a command and control mechanism. IRC normally uses which one of the following TCP ports?
Answer: C
NEW QUESTION 25
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the authentication procedures. Creating a backdoor is a where an attacker obtains remote access to a computer on a network.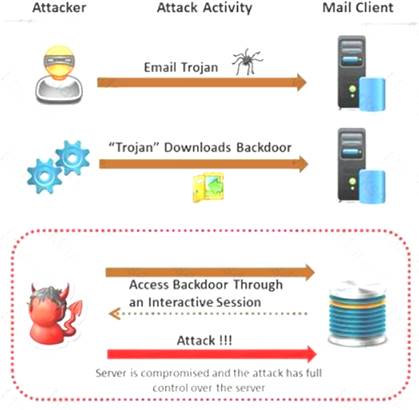
Which of the following techniques do attackers use to create backdoors to covertly gather critical information about a target machine?
Answer: D
NEW QUESTION 26
Harold is a web designer who has completed a website for ghttech.net. As part of the maintenance agreement he signed with the client, Harold is performing research online and seeing how much exposure the site has received so far. Harold navigates to google.com and types in the following search.
link:www.ghttech.net
What will this search produce?
Answer: A
NEW QUESTION 27
The objective of this act was to protect consumers personal financial information held by financial institutions and their service providers.
Answer: C
NEW QUESTION 28
......
100% Valid and Newest Version ECSAv10 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/ECSAv10-dumps.html (New 201 Q&As)