
Exam Code: GCIA (Practice Exam Latest Test Questions VCE PDF)
Exam Name: GIAC Certified Intrusion Analyst
Certification Provider: GIAC
Free Today! Guaranteed Training- Pass GCIA Exam.
Also have GCIA free dumps questions for you:
NEW QUESTION 1
You work as a Network Administrator for Tech Perfect Inc. The office network is configured as an IPv6 network. You have to configure a computer with the IPv6 address, which is equivalent to an IPv4 publicly routable address. Which of the following types of addresses will you choose?
Answer: B
NEW QUESTION 2
Which of the following honeypots is a low-interaction honeypot and is used by companies or corporations for capturing limited information about malicious hackers?
Answer: A
NEW QUESTION 3
You work as a Network Administrator for Net Perfect Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest single domain network. Active Directory integrated zone has been configured on the network. You want to create a text file that lists the resource records of a specified zone for your record. Which of the following commands will you use to accomplish the task?
Answer: C
NEW QUESTION 4
Which of the following utilities provides information as per the format given below?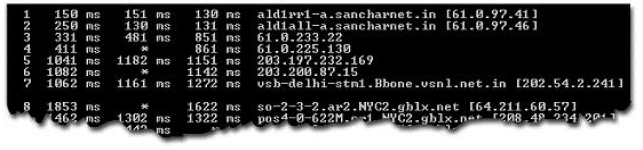
Answer: A
NEW QUESTION 5
John enters a URL http://www.cisco.com/web/learning in the web browser. A web page appears after he enters the URL. Which of the following protocols is used to resolve www.cisco.com into the correct IP address?
Answer: A
NEW QUESTION 6
Peter works as a Technical Representative in a CSIRT for SecureEnet Inc. His team is called to investigate the computer of an employee, who is suspected for classified data theft. Suspect's computer runs on Windows operating system. Peter wants to collect data and evidences for further analysis. He knows that in Windows operating system, the data is searched in pre-defined steps for proper and efficient analysis. Which of the following is the correct order for searching data on a Windows based system?
Answer: B
NEW QUESTION 7
Adam works on a Linux system. He is using Sendmail as the primary application to transmit e-mails.
Linux uses Syslog to maintain logs of what has occurred on the system. Which of the following log files contains e-mail information such as source and destination IP addresses, date and time stamps etc?
Answer: C
NEW QUESTION 8
Which of the following techniques allows probing firewall rule-sets and finding entry points into the targeted system or network?
Answer: D
NEW QUESTION 9
Andrew works as a Forensic Investigator for CertLeader Inc. The company has a Windows-based environment. The company's employees use Microsoft Outlook Express as their e-mail client program. E-mails of some employees have been deleted due to a virus attack on the network.
Andrew is therefore assigned the task to recover the deleted mails. Which of the following tools can Andrew use to accomplish the task?
Each correct answer represents a complete solution. Choose two.
Answer: BD
NEW QUESTION 10
Which of the following is known as a message digest?
Answer: A
NEW QUESTION 11
Which of the following tools performs comprehensive tests against web servers for multiple items, including over 6100 potentially dangerous files/CGIs?
Answer: C
NEW QUESTION 12
Which of the following is designed to protect the Internet resolvers (clients) from forged DNS data that are created by the DNS cache poisoning?
Answer: C
NEW QUESTION 13
You work as a professional Computer Hacking Forensic Investigator. A project has been assigned to you to investigate Plagiarism occurred in the source code files of C#. Which of the following tools will you use to detect the software plagiarism?
Answer: B
NEW QUESTION 14
Which of the following command-line utilities is used to show the state of current TCP/IP connections?
Answer: C
NEW QUESTION 15
You work as a Network Administrator for Net Perfect Inc. The company has a TCP/IP-based network. You are configuring an Internet connection on a server. Which of the following servers filters outbound Web traffic on the network?
Answer: C
NEW QUESTION 16
At which port does a DHCPv6 client listen for DHCP messages?
Answer: C
NEW QUESTION 17
Which of the following best describes the term protocol?
Answer: C
NEW QUESTION 18
Which of the following are open-source vulnerability scanners?
Answer: ACD
NEW QUESTION 19
Which of the following commands will you use with the tcpdump command to display the contents of the packets?
Answer: D
NEW QUESTION 20
......
P.S. Allfreedumps.com now are offering 100% pass ensure GCIA dumps! All GCIA exam questions have been updated with correct answers: https://www.allfreedumps.com/GCIA-dumps.html (508 New Questions)