
Act now and download your GIAC GCIH test today! Do not waste time for the worthless GIAC GCIH tutorials. Download Far out GIAC GIAC Certified Incident Handler exam with real questions and answers and begin to learn GIAC GCIH with a classic professional.
Online GCIH free questions and answers of New Version:
NEW QUESTION 1
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to perform a stealth scan to discover open ports and applications running on the We-are-secure server. For this purpose, he wants to initiate scanning with the IP address of any third party. Which of the following scanning techniques will John use to accomplish his task?
Answer: B
NEW QUESTION 2
Adam has installed and configured his wireless network. He has enabled numerous security features such as changing the default SSID, enabling WPA encryption, and enabling MAC filtering on his wireless router. Adam notices that when he uses his wireless connection, the speed is sometimes 16 Mbps and sometimes it is only 8 Mbps or less. Adam connects to the management utility wireless router and finds out that a machine with an unfamiliar name is connected through his wireless connection. Paul checks the router's logs and notices that the unfamiliar machine has the same MAC address as his laptop.
Which of the following attacks has been occurred on the wireless network of Adam?
Answer: C
NEW QUESTION 3
An Active Attack is a type of steganography attack in which the attacker changes the carrier during the communication process. Which of the following techniques is used for smoothing the transition and controlling contrast on the hard edges, where there is significant color transition?
Answer: D
NEW QUESTION 4
Which of the following types of attacks come under the category of hacker attacks?
Each correct answer represents a complete solution. Choose all that apply.
Answer: BD
NEW QUESTION 5
Choose and reorder the steps of an incident handling process in their correct order.
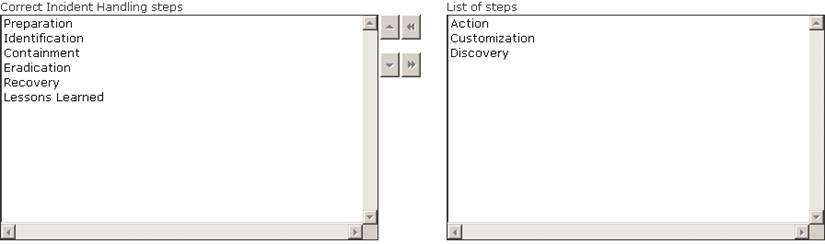
Answer: A
NEW QUESTION 6
Which of the following applications is an example of a data-sending Trojan?
Answer: D
NEW QUESTION 7
You run the following PHP script:
<?php $name = mysql_real_escape_string($_POST["name"]);
$password = mysql_real_escape_string($_POST["password"]); ?>
What is the use of the mysql_real_escape_string() function in the above script.
Each correct answer represents a complete solution. Choose all that apply.
Answer: BD
NEW QUESTION 8
Which of the following statements about smurf is true?
Answer: B
NEW QUESTION 9
You work as a System Administrator in SunSoft Inc. You are running a virtual machine on Windows Server 2003. The virtual machine is protected by DPM. Now, you want to move the virtual machine to another host. Which of the following steps can you use to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
Answer: ACD
NEW QUESTION 10
You work as a Network Administrator for Net Perfect Inc. The company has a Windows-based network. The company wants to fix potential vulnerabilities existing on the tested systems. You use Nessus as a vulnerability scanning program to fix the vulnerabilities. Which of the following vulnerabilities can be fixed using Nessus?
Each correct answer represents a complete solution. Choose all that apply.
Answer: ABC
NEW QUESTION 11
5.2.92:4079 ---------FIN--------->192.5.2.110:23
Answer: A
NEW QUESTION 12
Which of the following is a reason to implement security logging on a DNS server?
Answer: C
NEW QUESTION 13
CORRECT TEXT
Fill in the blank with the appropriate term.
______ is a free Unix subsystem that runs on top of Windows.
Answer: Cygwin
NEW QUESTION 14
Which of the following applications is NOT used for passive OS fingerprinting?
Answer: D
NEW QUESTION 15
John works as a Network Security Professional. He is assigned a project to test the security of www.we-are-secure.com. He establishes a connection to a target host running a Web service with netcat and sends a bad html request in order to retrieve information about the service on the host.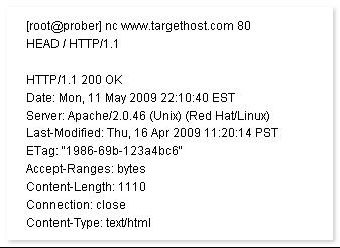
Which of the following attacks is John using?
Answer: D
NEW QUESTION 16
Which of the following protocols uses only User Datagram Protocol (UDP)?
Answer: D
NEW QUESTION 17
The IT administrator wants to implement a stronger security policy. What are the four most important security priorities for Exambible Software Systems Pvt. Ltd.? (Click the Exhibit button on the toolbar to see the case study.)
Answer: ACEF
NEW QUESTION 18
Session splicing is an IDS evasion technique in which an attacker delivers data in multiple small- sized packets to the target computer. Hence, it becomes very difficult for an IDS to detect the attack signatures of such attacks. Which of the following tools can be used to perform session splicing attacks?
Each correct answer represents a complete solution. Choose all that apply.
Answer: AC
NEW QUESTION 19
Which of the following systems is used in the United States to coordinate emergency preparedness and incident management among various federal, state, and local agencies?
Answer: D
NEW QUESTION 20
You are the Security Consultant and have been hired to check security for a client's network. Your client has stated that he has many concerns but the most critical is the security of Web applications on their Web server. What should be your highest priority then in checking his network?
Answer: C
NEW QUESTION 21
......
P.S. Dumpscollection.com now are offering 100% pass ensure GCIH dumps! All GCIH exam questions have been updated with correct answers: https://www.dumpscollection.net/dumps/GCIH/ (328 New Questions)