
Passleader offers free demo for GPEN exam. "GIAC Certified Penetration Tester", also known as GPEN exam, is a GIAC Certification. This set of posts, Passing the GIAC GPEN exam, will help you answer those questions. The GPEN Questions & Answers covers all the knowledge points of the real exam. 100% real GIAC GPEN exams and revised by experts!
GIAC GPEN Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
During a penetration test you discover a valid set of SSH credentials to a remote system. How can this be used to your advantage in a Nessus scan?
Answer: C
NEW QUESTION 2
You are performing a wireless penetration lest and are currently looking for rogue access points in one of their large facilities. You need to select an antenna that you can setup in a building and monitor the area for several days to see if any access points are turned on during the duration of the test. What type of antenna will you be selecting for this task?
Answer: B
NEW QUESTION 3
In which layer of the OSI model does a sniffer operate?
Answer: D
NEW QUESTION 4
Analyze the command output below. What information can the tester infer directly from the information shown? 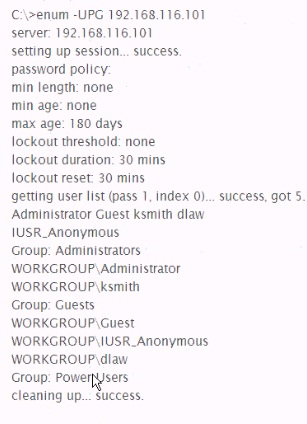
Answer: C
NEW QUESTION 5
You work as a Web developer in the IBM Inc. Your area of proficiency is PHP. Since you have proper knowledge of security, you have bewared from rainbow attack. For mitigating this attack, you design the PHP code based on the following algorithm:
key = hash(password + salt)
for 1 to 65000 do
key = hash(key + salt)
Which of the following techniques are you implementing in the above algorithm?
Answer: A
NEW QUESTION 6
168.1 200, which of the following would you see?
Answer: A
NEW QUESTION 7
What happens when you scan a broadcast IP address of a network?
Each correct answer represents a complete solution. Choose all that apply.
Answer: CD
NEW QUESTION 8
You have been contracted to map me network and try to compromise the servers for a client. Which of the following would be an example of scope creep' with respect to this penetration testing project?
Answer: B
NEW QUESTION 9
Which of the following TCSEC classes defines verified protection?
Answer: C
NEW QUESTION 10
What is the MOST important document to obtain before beginning any penetration testing?
Answer: A
Explanation:
Reference:
Before starting a penetration test, all targets must be identified. These targets should be obtained from the customer during the initial questionnaire phase. Targets can be given in the form of specific IP addresses, network ranges, or domain names by the customer. In some instances, the only target the customer provides is the name of the organization and expects the testers be able to identify the rest on their own. It is important to define if systems like firewalls and IDS/IPS or networking equipment that are between the tester and the final target are also part of the scope. Additional elements such as upstream providers, and other 3rd party providers should be identified and defined whether they are in scope or not.
NEW QUESTION 11
Which of the following penetration testing phases involves gathering data from whois, DNS, and network scanning, which helps in mapping a target network and provides valuable information regarding the operating system and applications running on the systems?
Answer: C
NEW QUESTION 12
The employees of CCN Inc. require remote access to the company's proxy servers. In order to provide solid wireless security, the company uses LEAP as the authentication protocol. Which of the following is supported by the LEAP protocol?
Each correct answer represents a complete solution. Choose all that apply.
Answer: BD
NEW QUESTION 13
Which of the following are the drawbacks of the NTLM Web authentication scheme?
Each correct answer represents a complete solution. Choose all that apply.
Answer: AB
NEW QUESTION 14
Answer: A
NEW QUESTION 15
Which of the following wireless security standards supported by Windows Vista provides the highest level of security?
Answer: A
NEW QUESTION 16
Which of the following types of Penetration testing provides the testers with complete knowledge of the infrastructure to be tested?
Answer: A
NEW QUESTION 17
Which of the following is the second half of the LAN manager Hash?
Answer: C
NEW QUESTION 18
Victor works as a professional Ethical Hacker for SecureEnet Inc. He wants to scan the wireless network of the company. He uses a tool that is a free open-source utility for network exploration.
The tool uses raw IP packets to determine the following:
What ports are open on our network systems.
What hosts are available on the network.
Identify unauthorized wireless access points.
What services (application name and version) those hosts are offering.
What operating systems (and OS versions) they are running.
What type of packet filters/firewalls are in use.
Which of the following tools is Victor using?
Answer: A
NEW QUESTION 19
Which of the following United States laws protects stored electronic information?
Answer: D
NEW QUESTION 20
......
Thanks for reading the newest GPEN exam dumps! We recommend you to try the PREMIUM Surepassexam GPEN dumps in VCE and PDF here: https://www.surepassexam.com/GPEN-exam-dumps.html (385 Q&As Dumps)