
we provide Exact GIAC GPEN actual exam which are the best for clearing GPEN test, and to get certified by GIAC GIAC Certified Penetration Tester. The GPEN Questions & Answers covers all the knowledge points of the real GPEN exam. Crack your GIAC GPEN Exam with latest dumps, guaranteed!
Also have GPEN free dumps questions for you:
NEW QUESTION 1
Which of the following tools is NOT used for wireless sniffing?
Answer: D
NEW QUESTION 2
Which of the following tools automates password guessing in the NetBIOS session?
Answer: C
NEW QUESTION 3
Which of the following tools can be used to perform Windows password cracking, Windows
enumeration, and VoIP session sniffing?
Answer: A
NEW QUESTION 4
You have gained shell on a Windows host and want to find other machines to pivot to, but the rules of engagement state that you can only use tools that are already available. How could you find other machines on the target network?
Answer: B
Explanation:
Reference:
http://www.slashroot.in/what-ping-sweep-and-how-do-ping-sweep
NEW QUESTION 5
Which of the following options holds the strongest password?
Answer: B
NEW QUESTION 6
When a DNS server transfers its zone file to a remote system, what port does it typically use?
Answer: D
Explanation:
Reference:
http://www.networkworld.com/article/2231682/cisco-subnet/cisco-subnet-allow-both-tcp-and-udp-port-53-to-your-dns-servers.html
NEW QUESTION 7
You work as a Penetration Tester for the Infosec Inc. Your company takes the projects of security auditing. Recently, your company has assigned you a project to test the security of the we-aresecure. com network. Now, when you have finished your penetration testing, you find that the weare- secure.com server is highly vulnerable to SNMP enumeration. You advise the we-are-secure Inc. to turn off SNMP; however, this is not possible as the company is using various SNMP services on its remote nodes. What other step can you suggest to remove SNMP vulnerability?
Each correct answer represents a complete solution. Choose two.
Answer: BC
NEW QUESTION 8
You are a Web Administrator of Millennium Inc. The company has hosted its Web site within its network. The management wants the company's vendors to be able to connect to the corporate site from their locations through the Internet. As a public network is involved in this process, you are concerned about the security of data transmitted between the vendors and the corporate site.
Which of the following can help you?
Answer: D
NEW QUESTION 9
LM hash is one of the password schemes that Microsoft LAN Manager and Microsoft Windows versions prior to the Windows Vista use to store user passwords that are less than 15 characters long. If you provide a password seven characters or less, the second half of the LM hash is always
__________.
Answer: D
NEW QUESTION 10
__________ firewall architecture uses two NICs with a screening router inserted between the host and the untrusted network.
Answer: B
NEW QUESTION 11
Analyze the screenshot below, which of the following sets of results will be retrieved using this search? 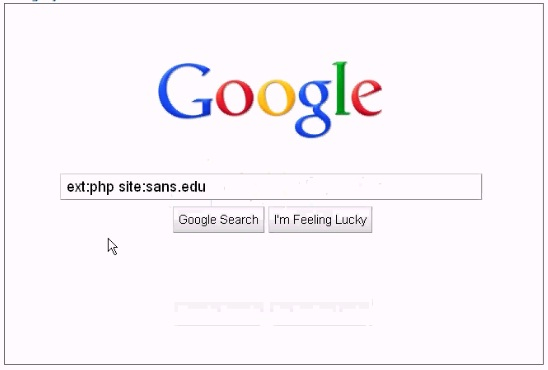
Answer: A
NEW QUESTION 12
You have connected to a Windows system remotely and have shell access via netcat. While connected to the remote system you notice that some Windows commands work normally while others do not An example of this is shown in the picture below Which of the following best describes why tins is happening? 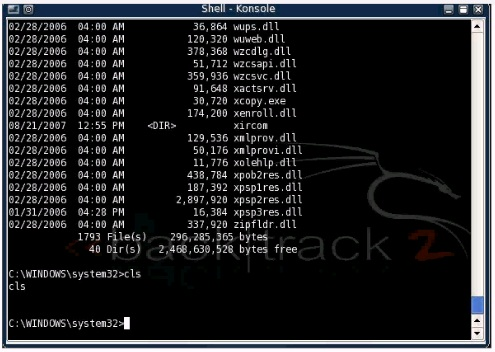
Answer: D
NEW QUESTION 13
Which of the following is a Windows-based tool that is used for the detection of wireless LANs using the IEEE 802.11a, 802.11b, and 802.11g standards and also detects wireless networks marking their relative position with a GPS?
Answer: B
NEW QUESTION 14
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He has successfully performed the following steps of the preattack phase to check the security of the We-are-secure network:
l Gathering information
l Determining the network range
l Identifying active systems
Now, he wants to find the open ports and applications running on the network. Which of the following tools will he use to accomplish his task?
Answer: B
NEW QUESTION 15
Which of the following methods will free up bandwidth in a Wireless LAN (WLAN)?
Answer: B
NEW QUESTION 16
You work as a Penetration Tester for the Infosec Inc. Your company takes the projects of security auditing. Recently, your company has assigned you a project to test the security of the we-aresecure. com Website. The we-are-secure.com Web server is using Linux operating system. When you port scanned the we-are-secure.com Web server, you got that TCP port 23, 25, and 53 are open. When you tried to telnet to port 23, you got a blank screen in response. When you tried to type the dir, copy, date, del, etc. commands you got only blank spaces or underscores symbols on the screen. What may be the reason of such unwanted situation?
Answer: B
NEW QUESTION 17
Which of the following is a WEP weakness that makes it easy to Inject arbitrary clear text packets onto a WEP network?
Answer: D
NEW QUESTION 18
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. In order to do so, he performs the following steps of the preattack phase successfully:
Information gathering
Determination of network range
Identification of active systems
Location of open ports and applications
Now, which of the following tasks should he perform next?
Answer: A
NEW QUESTION 19
You are pen testing a system and want to use Metasploit 3.X to open a listening port on the system so you can access it via a netcat shell. Which stager would you use to have the system listen on TCP port 50000?
Answer: B
NEW QUESTION 20
......
Thanks for reading the newest GPEN exam dumps! We recommend you to try the PREMIUM Thedumpscentre.com GPEN dumps in VCE and PDF here: https://www.thedumpscentre.com/GPEN-dumps/ (385 Q&As Dumps)