
we provide High value GIAC GPEN book which are the best for clearing GPEN test, and to get certified by GIAC GIAC Certified Penetration Tester. The GPEN Questions & Answers covers all the knowledge points of the real GPEN exam. Crack your GIAC GPEN Exam with latest dumps, guaranteed!
Free GPEN Demo Online For GIAC Certifitcation:
NEW QUESTION 1
The employees of CCN Inc. require remote access to the company's proxy servers. In order to provide solid wireless security, the company uses LEAP as the authentication protocol. Which of the following is supported by the LEAP protocol?
Each correct answer represents a complete solution. Choose all that apply.
Answer: BC
NEW QUESTION 2
In which of the following attacks is a malicious packet rejected by an IDS, but accepted by the host system?
Answer: B
NEW QUESTION 3
All of the following are advantages of using the Metasploitpriv module for dumping hashes from a local Windows machine EXCEPT:
Answer: B
Explanation:
Reference:
http://www.vita.virginia.gov/uploadedFiles/VITA_Main_Public/Security/Meetings/ISOAG/2012/2012_Jan_ISOAG.pdf
NEW QUESTION 4
Which of the following techniques are NOT used to perform active OS fingerprinting?
Each correct answer represents a complete solution. Choose all that apply.
Answer: AB
NEW QUESTION 5
Adam works as a professional Computer Hacking Forensic Investigator. He wants to investigate a suspicious email that is sent using a Microsoft Exchange server. Which of the following files will he review to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
Answer: ACD
NEW QUESTION 6
You work as a professional Computer Hacking Forensic Investigator for DataEnet Inc. You want to investigate e-mail information of an employee of the company. The suspected employee is using an online e-mail system such as Hotmail or Yahoo. Which of the following folders on the local computer will you review to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Answer: ABC
NEW QUESTION 7
Which of the following security policies will you implement to keep safe your data when you connect your Laptop to the office network over IEEE 802.11 WLANs?
Each correct answer represents a complete solution. Choose two.
Answer: AD
NEW QUESTION 8
In which of the following attacks does the attacker overload the CAM table of the switch?
Answer: A
NEW QUESTION 9
You want to perform an active session hijack against Secure Inc. You have found a target that allows Telnet session. You have also searched an active session due to the high level of traffic on the network. What should you do next?
Answer: B
NEW QUESTION 10
Identify the network activity shown below; 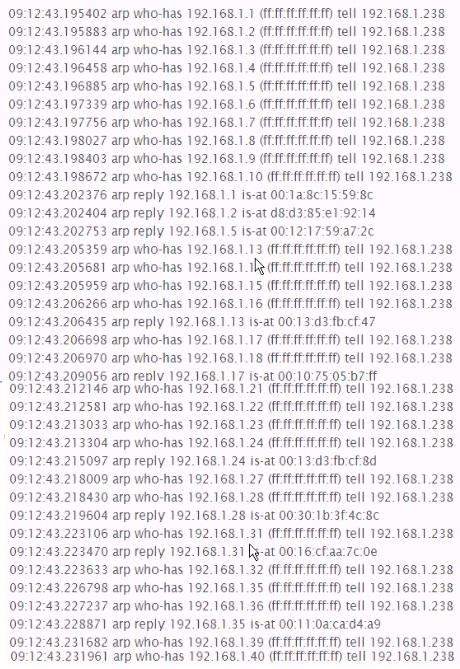
Answer: D
NEW QUESTION 11
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He performs Web vulnerability scanning on the We-are-secure server.
The output of the scanning test is as follows:
C:whisker.pl -h target_IP_address
-- whisker / v1.4.0 / rain forest puppy / www.wiretrip.net -- = - = - = - = - =
= Host: target_IP_address
= Server: Apache/1.3.12 (Win32) ApacheJServ/1.1
mod_ssl/2.6.4 OpenSSL/0.9.5a mod_perl/1.22
+ 200 OK: HEAD /cgi-bin/printenv
John recognizes /cgi-bin/printenv vulnerability ('Printenv' vulnerability) in the We_are_secure server. Which of the following statements about 'Printenv' vulnerability are true?
Each correct answer represents a complete solution. Choose all that apply.
Answer: BCD
NEW QUESTION 12
Which of the following tasks is NOT performed by antiviruses?
Answer: D
NEW QUESTION 13
Which of the following statements about SSID is NOT true?
Answer: A
NEW QUESTION 14
Which of the following standards is used in wireless local area networks (WLANs)?
Answer: C
NEW QUESTION 15
Which of the following is the frequency range to tune IEEE 802.11a network?
Answer: B
NEW QUESTION 16
How can a non-privileged user on a Unix system determine if shadow passwords are being used?
Answer: B
NEW QUESTION 17
Adam works as a professional Computer Hacking Forensic Investigator. He works with the local police. A project has been assigned to him to investigate an iPod, which was seized from a student of the high school. It is suspected that the explicit child pornography contents are stored in the iPod. Adam wants to investigate the iPod extensively. Which of the following operating systems will Adam use to carry out his investigations in more extensive and elaborate manner?
Answer: D
NEW QUESTION 18
You have been contracted to perform a black box pen test against the Internet facing servers for a company. They want to know, with a high level of confidence, if their servers are vulnerable to external attacks. Your contract states that you can use all tools available to you to pen test the systems. What course of action would you use to generate a report with the lowest false positive rate?
Answer: B
NEW QUESTION 19
Which of the following tools uses exploits to break into remote operating systems?
Answer: B
NEW QUESTION 20
......
P.S. Easily pass GPEN Exam with 385 Q&As Dumps-hub.com Dumps & pdf Version, Welcome to Download the Newest Dumps-hub.com GPEN Dumps: https://www.dumps-hub.com/GPEN-dumps.html (385 New Questions)