
Actualtests offers free demo for GPEN exam. "GIAC Certified Penetration Tester", also known as GPEN exam, is a GIAC Certification. This set of posts, Passing the GIAC GPEN exam, will help you answer those questions. The GPEN Questions & Answers covers all the knowledge points of the real exam. 100% real GIAC GPEN exams and revised by experts!
Online GPEN free questions and answers of New Version:
NEW QUESTION 1
Which of the following layers of TCP/IP model is used to move packets between the Internet Layer interfaces of two different hosts on the same link?
Answer: D
NEW QUESTION 2
Which of the following are considered Bluetooth security violations?
Each correct answer represents a complete solution. Choose two.
Answer: CD
NEW QUESTION 3
You work as a Network Administrator in the Secure Inc. Your company is facing various network attacks due to the insecure wireless network. You are assigned a task to secure your wireless network. For this, you have turned off broadcasting of the SSID. However, the unauthorized users are still able to connect to the wireless network. Which of the following statements can be the reason for this issue?
Each correct answer represents a complete solution. Choose all that apply.
Answer: ACD
NEW QUESTION 4
Which of the following statements are true about session hijacking?
Each correct answer represents a complete solution. Choose all that apply.
Answer: ABC
NEW QUESTION 5
While performing a code audit, you discover a SQL injection vulnerability assuming the following vulnerable query, what user input could be injected to make the query true and return data?
select * from widgets where name = '[user-input]';
Answer: D
NEW QUESTION 6
Which of the following techniques are NOT used to perform active OS fingerprinting?
Each correct answer represents a complete solution. Choose all that apply.
Answer: BC
NEW QUESTION 7
Which of the following is the most common method for an attacker to spoof email?
Answer: D
NEW QUESTION 8
A customer has asked for a scan or vulnerable SSH servers. What is the penetration tester attempting to accomplish using the following Nmap command? 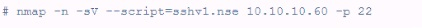
Answer: D
NEW QUESTION 9
You have compromised a Windows XP system and Injected the Meterpreter payload into the lsass process. While looking over the system you notice that there is a popular
password management program on the system. When you attempt to access the file that contains the password you find it is locked. Further investigation reveals that it is locked by the passmgr process. How can you use the Meterpreter to get access to this file?
Answer: C
NEW QUESTION 10
Which of the following layers of TCP/IP model is used to move packets between the Internet Layer interfaces of two different hosts on the same link?
Answer: B
NEW QUESTION 11
You want that some of your Web pages should not be crawled. Which one of the following options will you use to accomplish the task?
Answer: C
NEW QUESTION 12
A penetration tester obtains telnet access to a target machine using a captured credential. While trying to transfer her exploit to the target machine, the network intrusion detection
systems keeps detecting her exploit and terminating her connection. Which of the following actions will help the penetration tester transfer an exploit and compile it in the target system?
Answer: D
NEW QUESTION 13
What is the impact on pre-calculated Rainbow Tables of adding multiple salts to a set of passwords?
Answer: B
NEW QUESTION 14
Which of the following is a tool for SSH and SSL MITM attacks?
Answer: C
NEW QUESTION 15
Which of the following tools connects to and executes files on remote systems?
Answer: C
NEW QUESTION 16
You suspect that system administrators In one part of the target organization are turning off their systems during the times when penetration tests are scheduled, what feature could you add to the ' Rules of engagement' that could help your team test that part of the target organization?
Answer: C
NEW QUESTION 17
Which of the following standards is used in wireless local area networks (WLANs)?
Answer: A
NEW QUESTION 18
Which of the following tools can be used to automate the MITM attack?
Answer: B
NEW QUESTION 19
During a penetration test we determine that TCP port 22 is listening on a target host. Knowing that SSHD is the typical service that listens on that port we attempt to validate that assumption with an SSH client but our effort Is unsuccessful. It turns out that it is actually an Apache webserver listening on the port, which type of scan would have helped us to determine what service was listening on port 22?
Answer: C
NEW QUESTION 20
......
Thanks for reading the newest GPEN exam dumps! We recommend you to try the PREMIUM Dumps-hub.com GPEN dumps in VCE and PDF here: https://www.dumps-hub.com/GPEN-dumps.html (385 Q&As Dumps)