
we provide Realistic GIAC GSNA question which are the best for clearing GSNA test, and to get certified by GIAC GIAC Systems and Network Auditor. The GSNA Questions & Answers covers all the knowledge points of the real GSNA exam. Crack your GIAC GSNA Exam with latest dumps, guaranteed!
Free GSNA Demo Online For GIAC Certifitcation:
NEW QUESTION 1
The Security Auditor's Research Assistant (SARA) is a third generation network security analysis tool. Which of the following statements are true about SARA? (Choose two)
Answer: AD
Explanation:
The Security Auditor's Research Assistant (SARA) is a third generation network security analysis tool. It has the following functions: It operates under Unix, Linux, MAC OS/X, or Windows (through coLinux) OS. It integrates the National Vulnerability Database (NVD). It can be used to perform SQL injection tests. It can be used to perform exhaustive XSS tests. It can be adapted to multiple firewalled environments. It supports remote self scan and API facilities. It is used for CIS benchmark initiatives. It also supports plug-in facility for third party apps. It supports CVE standards. It works as an enterprise search module. It works in both standalone or demo mode. Answer C is incorrect. SARA can be used to perform SQL injection tests. Answer B is incorrect. SARA can be used to perform exhaustive XSS tests.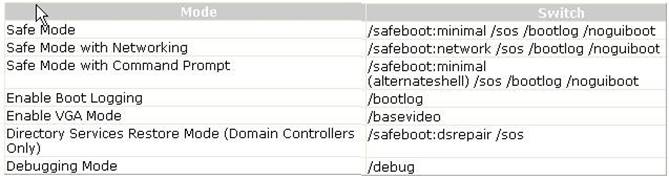
NEW QUESTION 2
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. You want to run two programs, foo and bar. You also want to ensure that bar is executed if and
only if foo has executed successfully. Which of the following command sequences will John use to accomplish the task?
Answer: D
Explanation:
According to the scenario, John will execute the foo && bar; command. Because of the && operator, bar will execute if and only if foo completes successfully. Answer A is incorrect. The foo; bar; command sequence will run foo and bar in a sequential manner, but the successful completion of the first command does not matter. Answer B is incorrect. The foo || bar; command sequence will run the bar if and only if foo fails to complete successfully. Answer C is incorrect. In the foo | bar; command sequence, the output of the foo command will be the input for the bar command.
NEW QUESTION 3
You work as a professional Ethical Hacker. You are assigned a project to perform blackbox testing of the security of www.we-are-secure.com. Now you want to perform banner grabbing to retrieve information about the Webserver being used by we-are-secure. Which of the following tools can you use to accomplish the task?
Answer: D
Explanation:
According to the scenario, you want to perform banner grabbing to retrieve information about the Webserver being used by we-are-secure. For this, you will use the httprint tool to accomplish the task. httprint is a fingerprinting tool that is based on Web server characteristics to accurately identify Web servers. It works even when Web server may have been obfuscated by changing the server banner strings, or by plug-ins such as mod_security or servermask. It can also be used to detect Web enabled devices that do not contain a server banner string, such as wireless access points, routers, switches, cable modems, etc. httprint uses text signature strings for identification, and an attacker can also add signatures to the signature database. Answer A is incorrect. Wget is a Website copier that is used to analyze the vulnerabilities of a Website offline. Answer C is incorrect. Whisker is an HTTP/Web vulnerability scanner that is written in the PERL language. Whisker runs on both the Windows and UNIX environments. It provides functions for testing HTTP servers for many known security holes, particularly the presence of dangerous CGIs. Answer B is incorrect. WinSSLMiM is an HTTPS Man in the Middle attacking tool. It includes FakeCert, a tool used to make fake certificates. It can be used to exploit the Certificate Chain vulnerability in Internet Explorer. The tool works under Windows 9x/2000. Which of the following tools can be used to automate the MITM attack? A. Airjack B. Kismet C. Hotspotter D. IKECrack Answer A
Airjack is a collection of wireless card drivers and related programs. It uses a program called monkey_jack that is used to automate the MITM attack. Wlan_jack is a DoS tool in the set of airjack tools, which accepts a target source and BSSID to send continuous deauthenticate frames to a single client or an entire network. Another tool, essid_jack is used to send a disassociate frame to a target client in order to force the client to reassociate with the network and giving up the network SSID. Answer C is incorrect. Hotspotter is a wireless hacking tool that is used to detect rogue access point. It fools users to connect, and authenticate with the hacker's tool. It sends the deauthenticate frame to the victim's computer that causes the victim's wireless connection to be switched to a non- preferred connection. Answer D is incorrect. IKECrack is an IKE/IPSec authentication crack tool, which uses brute force for searching password and key combinations of Pre- Shared-Key authentication networks. The IKECrack tool undermines the latest Wi-Fi security protocol with repetitive attempts at authentication with random passphrases or keys. Answer B is incorrect. Kismet is a Linux-based 802.11 wireless network sniffer and intrusion detection system. It can work with any wireless card that supports raw monitoring (rfmon) mode. Kismet can sniff 802.11b, 802.11a, 802.11g, and 802.11n traffic. Kismet can be used for the following tasks: To identify networks by passively collecting packets To detect standard named networks To detect masked networks To collect the presence of non-beaconing networks via data traffic
NEW QUESTION 4
One of the sales people in your company complains that sometimes he gets a lot of unsolicited messages on his PD A. After asking a few questions, you determine that the issue only occurs in crowded areas like airports. What is the most likely problem?
Answer: D
Explanation:
Blue jacking is the process of using another bluetooth device that is within range (about 30' or less) and sending unsolicited messages to the target. Answer B is incorrect. Blue snarfing is a process whereby the attacker actually takes control of the phone. Perhaps copying data or even making calls. Answer C is incorrect. A virus would not cause unsolicited messages. Adware might, but not a virus. Answer A is incorrect. Spam would not be limited to when the person was in a crowded area.
NEW QUESTION 5
Which of the following does an anti-virus program update regularly from its manufacturer's Web site?
Answer: D
Explanation:
An anti-virus program updates the virus definition file regularly from the anti- virus manufacturer's Web site. Antivirus (or anti-virus) software is used to prevent, detect, and remove malware, including computer viruses, worms, and trojan horses. Such programs may also prevent and remove adware, spyware, and other forms of malware. Traditional antivirus software solutions run virus scanners on schedule, on demand and some run scans in real time. If a virus or malware is located, the suspect file is usually placed into a quarantine to terminate its chances of disrupting the system. Traditional antivirus solutions scan and compare against a publicized and regularly updated dictionary of malware otherwise known as a blacklist. Some antivirus solutions have additional options that employ a heuristic engine which further examines the file to see if it is behaving in a similar manner to previous examples of malware. A new technology utilized by a few antivirus solutions is whitelisting; this technology first checks if the file is trusted and only questions those that are not. With the addition of wisdom of crowds, antivirus solutions backup other antivirus techniques by harnessing the intelligence and advice of a community of trusted users to protect each other. Answer C is incorrect. A service pack is a collection of Fixes and Patches in a single product. A service pack can be used to handle a large number of viruses and bugs or to update an operating system with advanceB, Detter capabilities. A service pack usually contains a number of file replacements. Answer A is incorrect. Hotfix is a collection of files used by Microsoft for software updates that are released between major service pack releases. A hotfix is about a problem, occurring under specific circumstances, which cannot wait to be fixed till the next service pack release. Hotfixes are generally related to security problems. Hence, it is essential to fix these problems as soon as possible. Answer B is incorrect. An anti-virus program does not update Permissions regularly from its manufacturer's Web site.
NEW QUESTION 6
You work as the Network Administrator for XYZ CORP. The company has a Linux-based network. You are a root user on the Red Hat operating system. You want to see first five lines of the file /etc/passwd. Which of the following commands should you use to accomplish the task?
Answer: A
Explanation:
The head -n 5 /etc/passwd command will show the first 5 lines of the file
/etc/passwd.
NEW QUESTION 7
Mark works as a Database Administrator for MarLinc Inc. How will he execute a SQL command from the SQL buffer?
Answer: BE
Explanation:
SQL buffer stores the most recently used SQL commands and PL/SQL blocks. It does not store the SQL* Plus commands. The SQL buffer can be edited or saved to a file. A SQL command or a PL/SQL block can be executed by entering a semicolon (;) or a slash (/), or by using the RUN command at the command prompt. When a semicolon (;) is entered at the end of a command, the command is completed and executed. When a slash (/) is entered on a new line, the command in the buffer is executed. It can also be used to execute a PL/SQL block. The RUN command is used to execute a command in the buffer. A SQL command can be saved in the buffer by entering a blank line. Reference: Oracle8i Online Documentation, Contents: "SQL*PLUS Users Guide and Reference", "Learning SQL*PLUS Basics, 3 of 4"
NEW QUESTION 8
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He begins to perform a pre-attack test before conducting an attack on the We-are-secure server. Which of the following will John perform in the pre-attack phase?
Answer: ABDE
Explanation:
In the pre-attack phase, there are seven steps, which have been defined by the EC-Council, as follows: 1.Information gathering 2.Determining network range 3.Identifying active machines 4.Finding open ports and applications 5.OS fingerprinting 6.Fingerprinting services 7.Mapping the network Answer C is incorrect. In the enumeration phase, the attacker gathers information such as the network user and group names, routing tables, and Simple Network Management Protocol (SNMP) data. The techniques used in this phase are as follows: 1.Obtaining Active Directory information and identifying vulnerable user accounts 2.Discovering NetBIOS names 3.Employing Windows DNS queries 4.Establishing NULL sessions and queries
NEW QUESTION 9
You work as a Network Administrator for Tech Perfect Inc. You have a laptop running Windows Vista Ultimate. You want to configure Windows Defender on your laptop so that it does not take any action automatically whenever it scans malicious software. Rather, it should recommend the action and wait for your approval for taking any action. Which of the following actions will you take to accomplish the task?
Answer: D
Explanation:
According to the question, you want to prevent Windows Defender from taking any action automatically during the scanning of your laptop. In order to accomplish this, you will have to clear the Apply default actions to items detected during a scan check box in Defender Options.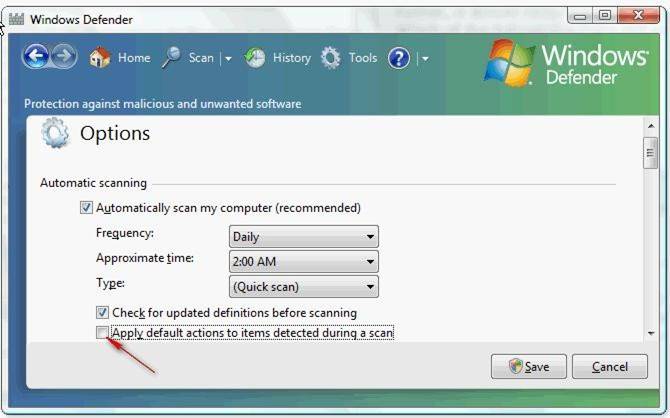
If you clear the Apply default actions to items detected during a scan check box, it will result in Windows Defender only recommending an action to take for detected malicious software.
NEW QUESTION 10
You have just taken over as the Network Administrator for a medium sized company. You want to check to see what services are exposed to the outside world. What tool would you use to accomplish this?
Answer: C
Explanation:
A port scanner is often used on the periphery of a network by either administrators or hackers. It will tell you what ports are open. By determining what ports are open, you know what services are exposed to the outside world. For example, if port 80 is open, then HTTP traffic is allowed, meaning there should be a Web server on the network. Answer: A is incorrect. Network mappers give a topography of the network, letting you know what is on your network and where it is connected. Answer: B is incorrect. A protocol analyzer does detect if a given protocol is moving over a particular network segment, thus would detect services working on that segment. However, a port scanner is a better tool for detecting all the ports that are open. Answer: D is incorrect. Packet sniffers are used to intercept traffic and to detect the contents of that traffic.
NEW QUESTION 11
Samantha works as a Web Developer for XYZ CORP. She develops a Web application using Visual InterDev. She wants to group a series of HTML elements together so that an action can be performed collectively on them. Which of the following tags will Samantha use to accomplish this?
Answer: A
Explanation:
DIV is an HTML tag that groups a series of elements into a larger group. It can be used when an action needs to be performed collectively on the grouped elements. The DIV tag acts as a container for other elements. Answer D is incorrect. The SPAN tag is used within an element to group a part of it. For example, this tag can be used to group a few sentences from within a paragraph, so that a particular action can be performed only on them. Answer C is incorrect. The BODY tag is used to specify the beginning and end of
the document body. Answer B is incorrect. There is no tag such as GROUP in HTML.
NEW QUESTION 12
Which of the following is an example of penetration testing?
Answer: C
Explanation:
Penetration testing is a method of evaluating the security of a computer system or network by simulating an attack from a malicious source, known as a Black Hat Hacker, or Cracker. The process involves an active analysis of the system for any potential vulnerabilities that may result from poor or improper system configuration, known and/or unknown hardware or software flaws, or operational weaknesses in process or technical countermeasures. This analysis is carried out from the position of a potential attacker, and can involve active exploitation of security vulnerabilities. Any security issues that are found will be presented to the system owner together with an assessment of their impact and often with a proposal for mitigation or a technical solution. The intent of a penetration testing is to determine feasibility of an attack and the amount of business impact of a successful exploit, if discovered. It is a component of a full security of penetration testing.
NEW QUESTION 13
You work as a Software Developer for UcTech Inc. You want to encode a URL, so that it can be used with the sendRedirect() method to send the response to the client. In order to accomplish this, you have to use a method of the HttpServletResponse interface. Which of the following methods will you use?
Answer: B
Explanation:
The encodeRedirectURL() method of the HttpServletResponse interface, returns a URL by including a session ID in it for use in the sendRedirect() method. If the encoding is not required, the URL is returned unchanged. If browser supports cookies, the encodeRedirectURL() method returns the input URL unchanged, since the session ID will be persisted as a cookie. This method is different from the encodeURL as this method redirects the request to a different URL in the same session. The syntax of the encodeRedirectURL() method is as follows: public String encodeRedirectURL(String urlstring) Here, urlstring is the URL to be encoded. Answer C is incorrect. The encodeURL() method of the HttpServletResponse interface returns a URL by including the session ID in it. If the encoding is not required, the URL is returned unchanged. If cookies are supported by the browser, the encodeURL() method returns the input URL unchanged since the session ID will be persisted as a cookie. The syntax of the encodeURL() method is as follows: public String encodeURL(String urlstring) Here, urlstring is the URL to be encoded.
NEW QUESTION 14
You are concerned about war driving bringing hackers attention to your wireless network. What is the most basic step you can take to mitigate this risk?
Answer: C
Explanation:
By not broadcasting your SSID some simple war driving tools won't detect your network. However you should be aware that there are tools that will still detect networks that are not broadcasting their SSID across your network. Answer D is incorrect. While MAC filtering may help prevent a hacker from accessing your network, it won't keep him or her from finding your network.
NEW QUESTION 15
You have to move the whole directory /foo to /bar. Which of the following commands will you use to accomplish the task?
Answer: C
Explanation:
You will use the mv /foo /bar command to move the whole directory /foo to /bar. The mv command moves files and directories from one directory to another or renames a file or directory. mv must always be given at least two arguments. The first argument is given as a source file. The second argument is interpreted as the destination. If destination is an existing directory, the source file is moved to that directory with the same name as the source. If the destination is any other directory, the source file is moved and/or renamed to that destination name. Syntax : mv [options] source destination Some important options used with mv command are as follows: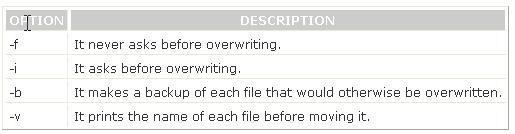
Answer A is incorrect. The mv /bar /foo command will move the whole /bar directory to the /foo directory. Answer B, D are incorrect. These are not valid Linux commands.
NEW QUESTION 16
You have been assigned a project to develop a Web site for a construction company. You have to develop a Web site and want to get more control over the appearance and presentation of your Web pages. You also want to increase the ability to precisely specify the location and appearance of the elements on a page and create special effects. You plan to use Cascading style sheets (CSS). You want to apply the same style consistently throughout your Web site. Which type of style sheet will you use?
Answer: B
Explanation:
To apply the same style consistently throughout your Web site you should use external style sheet. Cascading style sheets (CSS) are used so that the Web site authors can exercise greater control on the appearance and presentation of their Web pages. And also because they increase the ability to precisely point to the location and look of elements on a Web page and help in creating special effects. Cascading Style Sheets have codes, which are interpreteA, Dpplied by the browser on to the Web pages and their elements. There are three types of cascading style sheets. External Style Sheets Embedded Style Sheets Inline Style Sheets External Style Sheets are used whenever consistency in style is required throughout a Web site. A typical external style sheet uses a .css file extension, which can be edited using a text editor such as a Notepad. Embedded Style Sheets are used for defining styles for an active page.
Inline Style Sheets are used for defining individual elements of a page. Reference: TechNet, Contents: Microsoft Knowledgebase, February 2000 issue PSS ID Number: Q179628
NEW QUESTION 17
Which of the following are the limitations for the cross site request forgery (CSRF) attack?
Answer: AB
Explanation:
Following are the limitations of cross site request forgeries to be successful:
* 1. The attacker must target either a site that doesn't check the Referer header (which is common) or a victim with a browser or plugin bug that allows Referer spoofing (which is rare).
* 2. The attacker must find a form submission at the target site that does something useful to the attacker (e.g., transfers money, or changes the victim's e-mail address or password).
* 3. The attacker must determine the right values for all the form inputs: if any of them are required to be secret authentication values or IDs that the attacker can't guess, the attack will fail.
* 4. The attacker must lure the victim to a Web page with malicious code while the victim is logged in to the target site. Since, the attacker can't see what the target Web site sends back to the victim in response to the forged requests, unless he exploits a cross- site scripting or other bug at the target Web site.
Similarly, the attacker can only "click" any links or submit any forms that come up after the initial forged request, if the subsequent links or forms are similarly predictable. (Multiple "clicks" can be simulated by including multiple images on a page, or by using JavaScript to introduce a delay between clicks). from cross site request forgeries (CSRF) by applying the following countermeasures available: Requiring authentication in GET and POST parameters, not only cookies. Checking the HTTP Referer header. Ensuring there's no crossdomain.xml file granting unintended access to Flash movies. Limiting the lifetime of authentication cookies. Requiring a secret, user-specific token in all form submissions prevents CSRF; the attacker's site can't put the right token in its submissions. Individual Web users can do relatively little to prevent cross-site request forgery. Logging out of sites and avoiding their "remember me" features can mitigate CSRF risk; not displaying external images or not clicking links in "spam" or unreliable e-mails may also help.
NEW QUESTION 18
Which of the following tools combines two programs, and also encrypts the resulting package in an attempt to foil antivirus programs?
Answer: C
Explanation:
The Trojan Man is a Trojan wrapper that not only combines two programs, but also encrypts the resulting package in an attempt to foil antivirus programs.
NEW QUESTION 19
Pingdom is a website monitoring service. Which of the following services are provided by Pingdom?
Answer: BCD
Explanation:
Pingdom is a website monitoring service that is used by administrators to monitor sites and servers on the Internet. It alerts the site owners if it detects a problem. Pingdom service is used to track the uptime, downtime, and overall performance of websites. Pingdom also works as an iPhone application to make sure that a website is reachable and responding properly at all times. If not so, it provides the administrator with the email and SMS alerts. It creates charts and tables that are easy to understand. These charts and tables enable an administrator to spot trends and accurately pinpoint problems. Answer A is incorrect. Pingdom creates charts that are easy to understand. These charts are used to spot trends and accurately pinpoint problems.
NEW QUESTION 20
......
Recommend!! Get the Full GSNA dumps in VCE and PDF From DumpSolutions.com, Welcome to Download: https://www.dumpsolutions.com/GSNA-dumps/ (New 368 Q&As Version)