
We provide real GSNA exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass GIAC GSNA Exam quickly & easily. The GSNA PDF type is available for reading and printing. You can print more and practice many times. With the help of our GIAC GSNA dumps pdf and vce product and material, you can easily pass the GSNA exam.
Also have GSNA free dumps questions for you:
NEW QUESTION 1
You are responsible for a large network that has its own DNS servers. You periodically check the log to see if there are any problems. Which of the following are likely errors you might encounter in the log? (Choose three)
Answer: CDE
Explanation:
There are a number of errors one could find in a Windows Server 2003 DNS log. They are as follows: The DNS server could not create a Transmission Control Protocol. The DNS server could not open socket for address. The DNS server could not initialize the Remote Procedure Call (RPC) service. The DNS server could not bind the main datagram socket. The DNS Server service relies on Active Directory to store and retrieve information for Active Directory-integrated zones. And several active directory errors are possible. Answer B is incorrect. DNS Servers do not create FTP connections. Answer A is incorrect. DNS Servers do not create SMTP connections.
NEW QUESTION 2
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. The company has recently provided fifty laptops to its sales team members. You are required to configure an 802.11 wireless network for the laptops. The sales team members must be able to use their data placed at a server in a cabled network. The planned network should be able to handle the threat of unauthorized access and data interception by an unauthorized user. You are also required to prevent the sales team members from communicating directly to one another. Which of the following actions will you take to accomplish the task?
Answer: BCD
Explanation:
In order to enable wireless networking, you have to install access points in various areas of your office building. These access points generate omni directional signals to broadcast network traffic. Unauthorized users can intercept these packets. Hence, security is the major concern for a wireless network. The two primary threats are unauthorized access and data interception. In order to accomplish the task, you will have to take the following steps: Using group policies, configure the network to allow the wireless computers to connect to the infrastructure networks only. This will prevent the sales team members from communicating directly to one another. Implement the IEEE 802.1X authentication for the wireless network. This will allow only authenticated users to access the network data and resources. Configure the wireless network to use WEP encryption for data transmitted over a wireless network. This will encrypt the network data packets transmitted over wireless connections. Although WEP encryption does not prevent intruders from capturing the packets, it prevents them from reading the data inside.
NEW QUESTION 3
You have just installed a Windows 2003 server. What action should you take regarding the default shares?
Answer: B
Explanation:
Default shares should be disabled, unless they are absolutely needed. They pose a significant security risk by providing a way for an intruder to enter your machine. Answer A is incorrect. Whether this is a domain server, a DHCP server, a file server, or database server does not change the issue with shared drives/folders. Answer C is incorrect. They cannot be hidden. Shared folders are, by definition, not hidden but rather available to users on the network. Answer D is incorrect. These are not necessary for Windows Server operations.
NEW QUESTION 4
Mark works as a Web Designer for XYZ CORP. The company has a Windows-based network. Mark creates an HTML document that gives the following error on execution: "These hypertext system features are not supported by HTML". Which of the following can be the hypertext system features that are NOT supported by HTML? (Choose three)
Answer: ABD
Explanation:
HTML lacks some of the features found in earlier hypertext systems, such as typed links, source tracking, fat links etc. Even some hypertext features that were in early versions of HTML have been ignored by most popular web browsers until recently, such as the link element and in- browser Web page editing. Sometimes Web services or browser manufacturers remedy these shortcomings. Answer C is incorrect. Hyperlink is supported by HTML as well as Hypertext.
NEW QUESTION 5
Which of the following is a prevention-driven activity to reduce errors in the project and to help the project meet its requirements?
Answer: D
Explanation:
Quality assurance is the application of planned, systematic quality activities to ensure that the project will employ all processes needed to meet requirements. It is a prevention-driven activity to reduce errors in the project and to help the project meet its requirements. Answer A is incorrect. Audit sampling is an application of the audit procedure that enables the IT auditor to evaluate audit evidence within a class of transactions for the purpose of forming a conclusion concerning the population. When designing the size and structure of an audit sample, the IT auditor should consider the audit objectives determined when planning the audit, the nature of the population, and the sampling and selection methods. Answer C is incorrect. The process of limiting access to the resources of a Web site is called access control. Access control can be performed in the following ways: Registering the user in order to access the resources of the Web site. This can be confirmed by the user name and password. Limiting the time during which resources of the Web site can be used. For example, the Web site can be viewed between certain hours of a day. Answer B is incorrect. It is the practice of managing the whole life cycle (design, construction, commissioning, operating, maintaining, repairing, modifying, replacing and decommissioning/disposal) of physical and infrastructure assets such as structures, production, distribution networks, transport systems, buildings, and other physical assets.
NEW QUESTION 6
Which of the following Web authentication techniques uses a single sign-on scheme?
Answer: C
Explanation:
Microsoft Passport authentication is based on single sign-on authentication in which a user needs to remember only one username and password to be authenticated for multiple services. The Passport is a suite of services for authenticating users across a number of applications. The Passport single sign-on service is an authentication service allowing users to create a single set of credentials that will enable them to sign in to any participating site that supports the Passport service. It enables the use of one set of credentials to access any Passport-enabled site such as MSN, Hotmail, and MSN Messenger.
NEW QUESTION 7
You work as a Web Developer for XYZ CORP. The company has a Windows-based
network. You have been assigned the task to secure the website of the company. To accomplish the task, you want to use a website monitoring service. What are the tasks performed by a website monitoring service?
Answer: BCD
Explanation:
Website monitoring service can check HTTP pages, HTTPS, FTP, SMTP, POP3, IMAP, DNS, SSH, Telnet, SSL, TCP, PING, Domain Name Expiry, SSL Certificate Expiry, and a range of other ports with great variety of check intervals from every four hours to every one minute. Typically, most website monitoring services test a server anywhere between once-per hour to once-per-minute. Advanced services offer in-browser web transaction monitoring based on browser add-ons such as Selenium or iMacros. These services test a website by remotely controlling a large number of web browsers. Hence, it can also detect website issues such a JavaScript bugs that are browser specific. Answer A is incorrect. This task is performed under network monitoring. Network tomography deals with monitoring the health of various links in a network using end-to-end probes sent by agents located at vantage points in the network/Internet.
NEW QUESTION 8
Which of the following statements about packet filtering is true?
Answer: A
Explanation:
Packet filtering is a method that allows or restricts the flow of specific types of packets to provide security. It analyzes the incoming and outgoing packets and lets them pass or stops them at a network interface based on the source and destination addresses, ports, or protocols. Packet filtering provides a way to define precisely which type of IP traffic is allowed to cross the firewall of an intranet. IP packet filtering is important when users from private intranets connect to public networks, such as the Internet.
NEW QUESTION 9
You work as a Network Administrator for XYZ CORP. The company has a TCP/IP-based network environment. The network contains Cisco switches and a Cisco router. A user is unable to access the Internet from Host B. You also verify that Host B is not able to connect to other resources on the network. The IP configuration of Host B is shown below: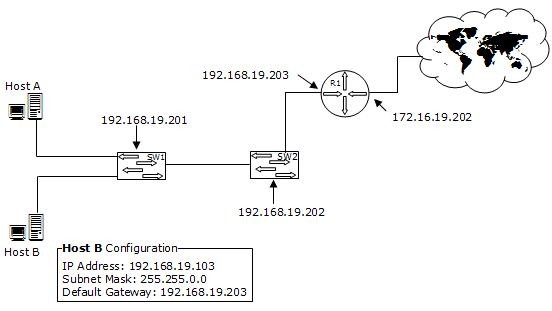
Which of the following is the most likely cause of the issue?
Answer: A
Explanation:
According to the network diagram, the IP address range used on the network is from the class C private address range. The class C IP address uses the following default subnet mask: 255.255.255.0 The question specifies that the subnet mask used in Host B is 255.255.0.0, which is an incorrect subnet mask.
NEW QUESTION 10
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to track the system for user logins. To accomplish the task, you need to analyze the log configuration files. Which of the following Unix log configuration files can you use to accomplish the task?
Answer: B
Explanation:
In Unix, the /var/log/secure file is used to track the systems for user logins. Answer D is incorrect. In Unix, the /var/log/maillog file is the normal system maillog file. Answer A is incorrect. In Unix, the /var/log/messages file is the main system message log file. Answer C is incorrect. In Unix, the /var/spool/mail file is the file where mailboxes are usually stored.
NEW QUESTION 11
A Web developer with your company wants to have wireless access for contractors that come in to work on various projects. The process of getting this approved takes time. So rather than wait, he has put his own wireless router attached to one of the network ports in his department. What security risk does this present?
Answer: D
Explanation:
Any unauthorized Wireless Access Point (WAP) is a serious security breach. Its configuration might be very unsecure. For example it might not use encryption or MAC filtering, thus allowing anyone in range to get on the network.
NEW QUESTION 12
You work as a Security Administrator in Tech Perfect Inc. The company has a TCP/IP based network. The network has a vast majority of Cisco Systems routers and Cisco network switches. You have mplemented four VPN connections in the network. You use the Cisco IOS on the network. Which feature will you enable to maintain a separate routing and forwarding table for each VPN?
Answer: B
Explanation:
In this scenario, the company's network has a vast majority of Cisco Systems routers and Cisco network switches. The security administrator of the company has implemented four VPN connections in the network and uses the Cisco IOS on the network. He needs to maintain a separate routing and forwarding table for each VPN in order to provide more secure communication. To accomplish this task, he should enable the VRF- aware firewall feature on the Cisco IOS routers.
NEW QUESTION 13
Which of the following user authentications are supported by the SSH-1 protocol but not by the SSH-2 protocol?
Answer: ABC
Explanation:
The Rhosts (rsh-style), TIS, and Kerberos user authentication methods are supported by the SSH-1 protocol but not by SSH-2 protocol. Answer D is incorrect. Password-based authentication is supported by both the SSH-1 and SSH-2 protocols.
NEW QUESTION 14
A sequence number is a 32-bit number ranging from 1 to 4,294,967,295. When data is sent over the network, it is broken into fragments (packets) at the source and reassembled at the destination system. Each packet contains a sequence number that is used by the destination system to reassemble the data packets in the correct order. The Initial Sequence Number of your computer is 24171311 at login time. You connect your computer to a computer having the IP address 210.213.23.21. This whole process takes three seconds. What will the value of the Initial Sequence Number be at this moment?
Answer: B
Explanation:
You took 3 seconds to establish a connection. During this time, the value of the Initial Sequence Number would become [24171311 + (1 * 64000) + (3 * 128000)], i.e., 24619311.
NEW QUESTION 15
You have purchased a laptop that runs Windows Vista Home Premium. You want to protect your computer from malicious applications, such as spyware, while connecting to the Internet. You configure Windows Defender on your laptop to schedule scan daily at 2 AM as shown in the image below: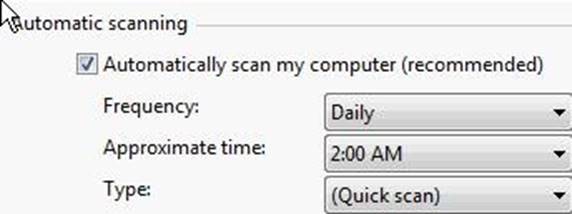
You want Windows Defender to scan the laptop for all the known spyware and other potentially unwanted software, including the latest one. You do not want to manually perform this task. Which of the following actions will you perform to accomplish the task?
Answer: C
Explanation:
According to the question, Windows Defender should scan the laptop for all the known spyware and other potentially unwanted software, including the latest one. Windows Defender uses definitions to scan the system. Definitions are files that include the information of known spyware and potentially unwanted software. To scan a computer for the latest spyware, Windows Defender requires the latest definition files available on the Internet. For this, you have to configure Windows Defender to check for the latest definitions and download them, if available, before scanning the computer. Furthermore, the question also states that the task must be performed automatically. In order to accomplish the task, you will have to select the Check for updated definitions before scanning check box in the Automatic Scanning section.
NEW QUESTION 16
George works as an office assistant in Soft Well Inc. The company uses the Windows Vista operating system. He wants to disable a program running on a computer. Which of the following Windows Defender tools will he use to accomplish the task?
Answer: D
Explanation:
Software Explorer is used to remove, enable, or disable a program running on a computer. Answer A is incorrect. Allowed items contains a list of all the programs that a user has chosen not to monitor with Windows Defender. Answer C is incorrect. Options is used to choose how Windows Defender should monitor all the programs running on a computer. Answer B is incorrect. Quarantined items is used to remove or restore a program blocked by Windows Defender.
NEW QUESTION 17
You work as a Network Administrator for Tech Perfect Inc. You need to configure the company firewall so that only Simple Network Management Protocol (SNMP) and Secure HTTP (HTTPS) traffic is allowed into the intranet of the company. No other traffic should be allowed into the intranet. Which of the following rule sets should you use on your firewall to accomplish the task? (Assume left to right equals top to bottom.)
Answer: C
Explanation:
In the given rule set, 'Input chain' defines that the rule is for the incoming traffic, i.e., traffic coming from the intranet to the Internet. Port 25 is being allowed for SNMP traffic and port 443 for the HTTPS traffic. Deny all is being used after allowing port 25 and 443; hence, all the other traffic will be denied. Answer B is incorrect. Deny all is executed first; hence, all the traffic will be denied including port 25 and 443. Answer A, D are incorrect. These rule sets are used for outgoing traffic, i.e., traffic going from the intranet to the Internet as the 'Output chain' rule is being used.
NEW QUESTION 18
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He is configuring the Apache Web server settings. He does not want the commands being used in the settings to be stored in the history. Which of the following commands can he use to disable history?
Answer: B
Explanation:
According to the scenario, John can use the set +o history command to disable history. Answer D is incorrect. John cannot use the set -o history command to accomplish his task. This command is used to enable disabled history.
Answer A is incorrect. John cannot use the history !! command to accomplish his task. This command is used to see the most recently typed command. Answer C is incorrect. John cannot use the history !N command to accomplish his task. This command is used to display the Nth history command.
NEW QUESTION 19
You work as a Network Administrator for Techpearl Inc. You are configuring the rules for the firewall of the company. You need to allow internal users to access secure external websites. Which of the following firewall rules will you use to accomplish the task?
Answer: D
Explanation:
The TCP 172.16.1.0/24 any any 443 HTTPs permit rule is used to allow internal users to access secure external websites. Answer A is incorrect. The TCP 172.16.1.0/24 any any 80 HTTP permit rule is used to allow internal users to access external websites (secure & unsecure both). Answer C is incorrect. The TCP 172.16.1.0/24 any any 80 HTTP deny rule is used to deny internal users to access external websites. Answer B is incorrect. The TCP 172.16.1.0/24 any any 25 SMTP permit rule is used to allow internal mail servers to deliver mails to external mail servers.
NEW QUESTION 20
......
P.S. Thedumpscentre.com now are offering 100% pass ensure GSNA dumps! All GSNA exam questions have been updated with correct answers: https://www.thedumpscentre.com/GSNA-dumps/ (368 New Questions)