
It is more faster and easier to pass the Juniper JN0-230 exam by using Verified Juniper Security - Associate (JNCIA-SEC) questuins and answers. Immediate access to the Abreast of the times JN0-230 Exam and find the same core area JN0-230 questions with professionally verified answers, then PASS your exam with a high score now.
Online JN0-230 free questions and answers of New Version:
NEW QUESTION 1
Exhibit.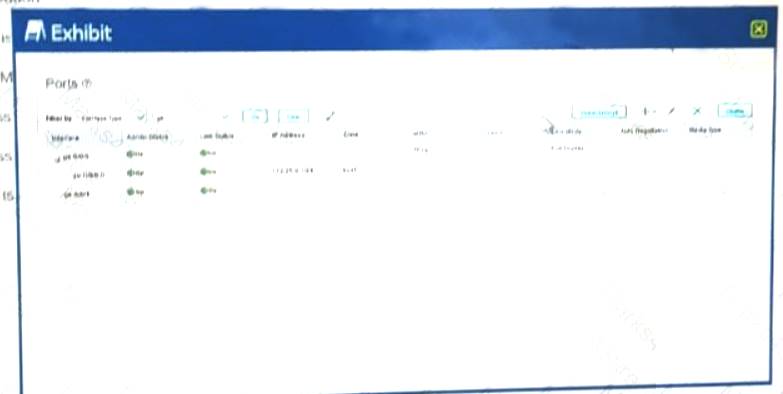
Which statement is correct regarding the interface configuration shown in the exhibit?
Answer: C
NEW QUESTION 2
Users should not have access to Facebook, however, a recent examination of the logs security show that users are accessing Facebook.
Referring to the exhibit,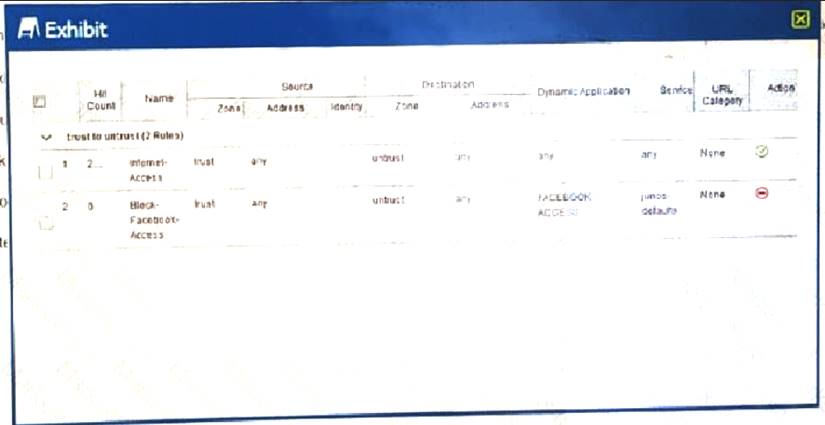
what should you do to solve this problem?
Answer: B
NEW QUESTION 3
Which UTM feature should you use to protect users from visiting certain blacklisted websites?
Answer: B
NEW QUESTION 4
Which two segments describes IPsec VPNs? (Choose two.)
Answer: AC
NEW QUESTION 5
Which management software supports metadata-based security policies that are ideal for cloud deployments?
Answer: A
NEW QUESTION 6
You have configured antispam to allow e-mail from example.com, however the logs you see thatjcart@example.comis blocked
Referring to the exhibit.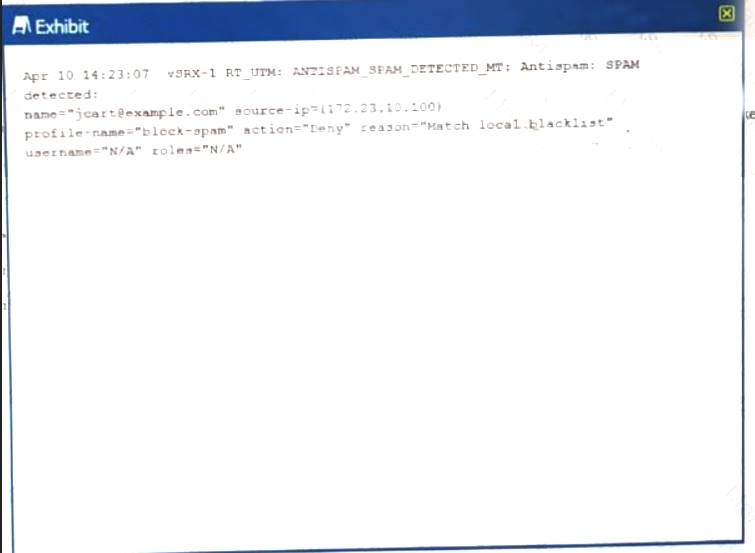
What are two ways to solve this problem?
Answer: BC
NEW QUESTION 7
Referring to the exhibit.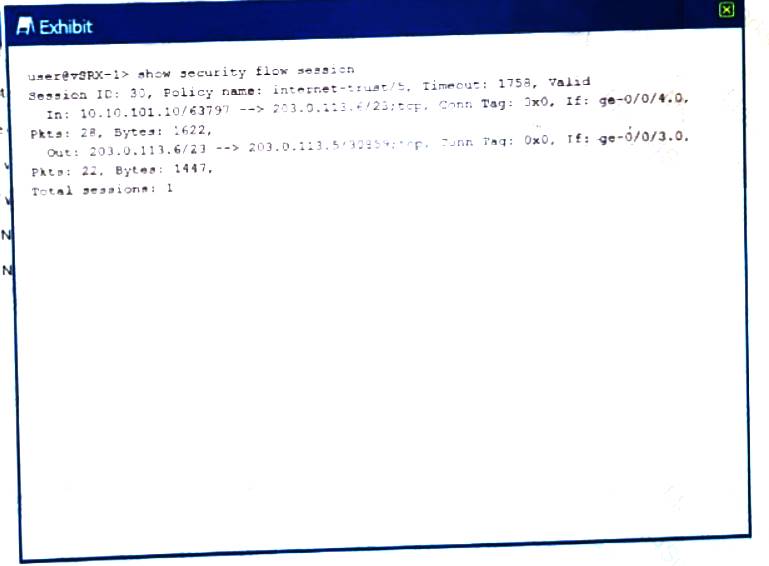
Which type of NAT is being performed?
Answer: A
NEW QUESTION 8
Which statement about IPsec is correct?
Answer: C
NEW QUESTION 9
You want to generate reports from the l-Web on an SRX Series device. Which logging mode would you use in this scenario?
Answer: B
NEW QUESTION 10
You are concerned that unauthorized traffic is using non-standardized ports on your network.
In this scenario, which type of security feature should you implement?
Answer: A
NEW QUESTION 11
Which statements about NAT are correct? (Choose two.)
Answer: AC
NEW QUESTION 12
What are the valid actions for a source NAT rule in J-Web? (choose three.)
Answer: BCE
Explanation:
Explanation
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/nat-security-source-and-source-pool.html
NEW QUESTION 13
You are configuring an IPsec VPN tunnel between two location on your network. Each packet must be encrypted and authenticated.
Which protocol would satisfy these requirements?
Answer: B
NEW QUESTION 14
You have created a zones-based security policy that permits traffic to a specific webserver for the marketing team. Other groups in the company are not permitted to access the webserver. When marketing users attempt to access the server they are unable to do so.
What are two reasons for this access failure? (Choose two.)
Answer: CD
NEW QUESTION 15
Which two statements are true about security policy actions? (Choose two.)
Answer: AB
NEW QUESTION 16
What is the purpose of the Shadow Policies workspace in J-Web?
Answer: A
NEW QUESTION 17
You verify that the SSH service is configured correctly on your SRX Series device, yet administrators attempting to connect through a revenue port are not able to connect.
In this scenario, what must be configured to solve this problem?
Answer: B
NEW QUESTION 18
Which statements is correct about Junos security zones?
Answer: C
NEW QUESTION 19
Which two statements are correct about using global-based policies over zone-based policies? (Choose two.)
Answer: AB
NEW QUESTION 20
You want to automatically generate the encryption and authentication keys during IPsec VPN establishment. What would be used to accomplish this task?
Answer: B
NEW QUESTION 21
Which type of security policy protect restricted services from running on non-standard ports?
Answer: B
NEW QUESTION 22
You are designing a new security policy on an SRX Series device. You must block an application and log all occurrence of the application access attempts.
In this scenario, which two actions must be enabled in the security policy? (Choose two.)
Answer: AD
NEW QUESTION 23
Your company uses SRX Series devices to secure the edge of the network. You are asked protect the company from ransom ware attacks.
Which solution will satisfy this requirement?
Answer: A
NEW QUESTION 24
On an SRX Series device, how should you configure your IKE gateway if the remote endpoint is a branch office-using a dynamic IP address?
Answer: B
NEW QUESTION 25
Which security feature is applied to traffic on an SRX Series device when the device is running n packet mode?
Answer: C
NEW QUESTION 26
......
P.S. Dumpscollection now are offering 100% pass ensure JN0-230 dumps! All JN0-230 exam questions have been updated with correct answers: http://www.dumpscollection.net/dumps/JN0-230/ (65 New Questions)