
Virtual of N10-007 test preparation materials and practice for CompTIA certification for examinee, Real Success Guaranteed with Updated N10-007 pdf dumps vce Materials. 100% PASS CompTIA Network+ N10-007 exam Today!
Online N10-007 free questions and answers of New Version:
NEW QUESTION 1
A network administrator wants to monitor traffic by deploying MIBs. Which of the follow network monitoring resources would be used?
Answer: D
NEW QUESTION 2
Which of the following is used to classify network data for the purpose of providing QoS?
Answer: D
NEW QUESTION 3
Which of the following is the correct representation of an IPv6 address?
Answer: A
NEW QUESTION 4
A network administrator is troubleshooting an intermittent network issue between devices that have a particularly long cable run. The issue was escalated to a network designer who alluded to potential attenuation issues. Which of the following BEST describes what the network designer was referring to?
Answer: D
NEW QUESTION 5
An administrator is setting up a secure wireless network. The administrator decides to support 802.11n and 802.11g with a WPA2 pre-shared key. Users are given the SSID with the pre-shared key, but the administrator has disabled the SSID broadcast and MAC filtering. Some users have reported connection issues. Which of the following would MOST likely resolve the users' connection issues?
Answer: B
NEW QUESTION 6
A technician notices that network access is becoming increasingly slow. All of the activity lights, on the only network layer 2 switch, are blinking at steadily increasing rates. Which of the following is the MOST likely cause of the increased traffic?
Answer: D
NEW QUESTION 7
Which of the following BEST describes how a layer 2 switch functions?
Answer: A
NEW QUESTION 8
An administrator wants to implement an additional authentication factor to the remote SSH servers. Which of the following accomplishes this goal with the principle of*something you have*?
Answer: A
NEW QUESTION 9
A firewall administrator is implementing a rule that directs HTTP traffic to an internal server listening on a non-standard socket. Which of the following types of rules is the administrator implementing?
Answer: B
NEW QUESTION 10
In which of the following ways does a DDoS attack differ from a spoofing attack?
Answer: C
NEW QUESTION 11
Zach, a network technician, is unable to remotely manage or ping certain layer 2 switches. To manage those devices remotely, which of the following will MOST likely need to be configured?
Answer: A
NEW QUESTION 12
A VoIP line will MOST likely have which of the following connectors?
Answer: D
NEW QUESTION 13
An administrator is troubleshooting analog telephony issues on the punch down block. Which of the following tools would be MOST useful in this scenario?
Answer: B
NEW QUESTION 14
The security manager reports that individual systems involved in policy or security violations or incidents cannot be located quickly. The security manager notices the hostnames all appear to be randomly generated characters. Which of the following would BEST assist the security manager identifying systems involved in security incidents?
Answer: B
NEW QUESTION 15
After plugging a cable into a computer, a user reports there is no network access. Which of the following tools would the technician MOST likely check to verify that the cable was crimped correctly?
Answer: B
NEW QUESTION 16
A network administrator gets a call regarding intermittent network outages across the country. Which of the following should be used to connect to the network so the administrator can troubleshoot this issue from home? (Choose two.)
Answer: CD
NEW QUESTION 17
A junior network technician is working in the field and needs to connect to the company/s remote server, however, doing so will require the junior technician to use the public Internet. Because security is a concern which of the following is the BEST method to use?
Answer: B
NEW QUESTION 18
Your company recently purchased a new building down the street from the existing office. For each of the tasks below, select the appropriate antenna type and encryption object for all wireless access point (AP).
1. Create an encrypted wireless connection between the two buildings that BEST controls signal propagation, while maximizing security.
2. Restrict the wireless signal generated by the access points (APs) inside Building 1, so that it minimizes broadcast beyond the building.
3. Maximize wireless coverage inside Building 1.
4. Building 1’s internal wireless network is for visitors only and must not require any special configuration on the visitor’s device to connect.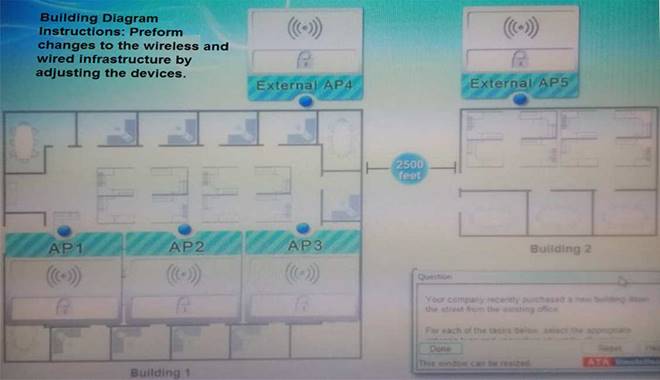
Instructions: When you have completed the simulation, select the Done button to submit.
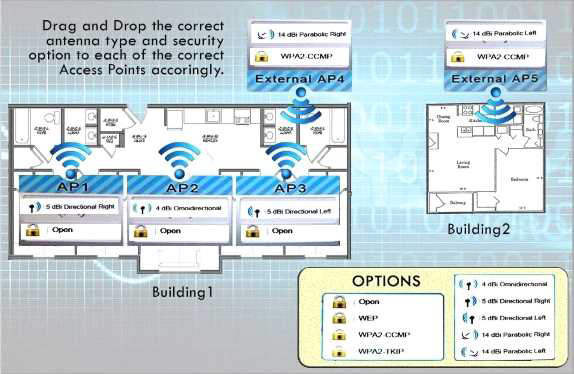
Answer: A
NEW QUESTION 19
......
100% Valid and Newest Version N10-007 Questions & Answers shared by Dumps-hub.com, Get Full Dumps HERE: https://www.dumps-hub.com/N10-007-dumps.html (New 601 Q&As)