
Want to know Certleader PCCET Exam practice test features? Want to lear more about Paloalto-Networks Palo Alto Networks Certified Cybersecurity Entry-level Technician certification experience? Study Tested Paloalto-Networks PCCET answers to Latest PCCET questions at Certleader. Gat a success with an absolute guarantee to pass Paloalto-Networks PCCET (Palo Alto Networks Certified Cybersecurity Entry-level Technician) test on your first attempt.
Online Paloalto-Networks PCCET free dumps demo Below:
NEW QUESTION 1
Which Palo Alto subscription service identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment?
Answer: C
NEW QUESTION 2
In which step of the cyber-attack lifecycle do hackers embed intruder code within seemingly innocuous files?
Answer: D
NEW QUESTION 3
What is required for a SIEM to operate correctly to ensure a translated flow from the system of interest to the SIEM data lake?
Answer: A
NEW QUESTION 4
What is a key advantage and key risk in using a public cloud environment?
Answer: A
NEW QUESTION 5
When signature-based antivirus software detects malware, what three things does it do to provide protection? (Choose three.)
Answer: CDE
NEW QUESTION 6
Systems that allow for accelerated incident response through the execution of standardized and automated playbooks that work upon inputs from security technology and other data flows are known as what?
Answer: C
NEW QUESTION 7
In addition to local analysis, what can send unknown files to WildFire for discovery and deeper analysis to rapidly detect potentially unknown malware?
Answer: A
NEW QUESTION 8
In addition to integrating the network and endpoint components, what other component does Cortex integrate to speed up IoC investigations?
Answer: C
NEW QUESTION 9
Which network analysis tool can be used to record packet captures?
Answer: B
NEW QUESTION 10
Which subnet does the host 192.168.19.36/27 belong?
Answer: D
NEW QUESTION 11
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
Answer: D
NEW QUESTION 12
What does SIEM stand for?
Answer: B
NEW QUESTION 13
Which IPsec feature allows device traffic to go directly to the Internet?
Answer: A
NEW QUESTION 14
Which attacker profile uses the internet to recruit members to an ideology, to train them, and to spread fear and include panic?
Answer: D
NEW QUESTION 15
Which technique changes protocols at random during a session?
Answer: B
NEW QUESTION 16
DRAG DROP
Match the description with the VPN technology.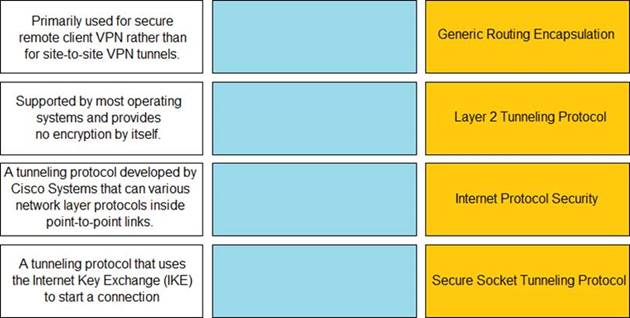
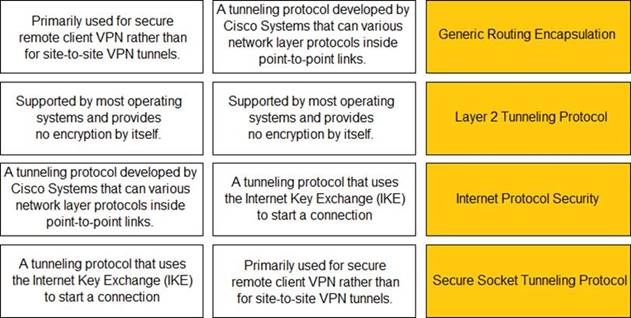
Answer: A
NEW QUESTION 17
On an endpoint, which method is used to protect proprietary data stored on a laptop that has been stolen?
Answer: B
NEW QUESTION 18
Which TCP/IP sub-protocol operates at the Layer7 of the OSI model?
Answer: C
NEW QUESTION 19
......
Thanks for reading the newest PCCET exam dumps! We recommend you to try the PREMIUM Dumps-files.com PCCET dumps in VCE and PDF here: https://www.dumps-files.com/files/PCCET/ (75 Q&As Dumps)