
100% Correct of PCCSA free practice questions materials and exam answers for Paloalto-Networks certification for IT professionals, Real Success Guaranteed with Updated PCCSA pdf dumps vce Materials. 100% PASS Palo Alto Networks Certified Cybersecurity Associate exam Today!
Free PCCSA Demo Online For Paloalto-Networks Certifitcation:
NEW QUESTION 1
Match each option with the term it describes.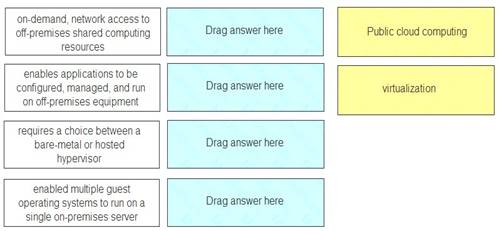
Answer: A
Explanation:
Public-cloud computing Public-cloud computing Virtualization Virtualization
NEW QUESTION 2
Which security component should you configure to block viruses not seen and blocked by the perimeter firewall?
Answer: C
NEW QUESTION 3
Company policy allows employees to access the internet. While searching for office supplies on the internet, a corporate user mistypes a URL, connects to a malicious website, and unknowingly downloads malware.
Which action should have been taken to prevent the malware download but still allow user access to the internet?
Answer: A
NEW QUESTION 4
What are two methods to securely transmit personally identifiable information? (Choose two.)
Answer: CD
NEW QUESTION 5
You discover malware has corrupted the BIOS on your laptop. Which type of malware is this?
Answer: A
NEW QUESTION 6
Which type of malware is self-replicating but must first infect a host program and be executed by a user or process?
Answer: B
NEW QUESTION 7
What method can be used to guarantee that a document originates from you and no one else?
Answer: A
NEW QUESTION 8
Which two types of SaaS applications are allowed by an IT department? (Choose two.)
Answer: AC
NEW QUESTION 9
Which security principle describes the practice of giving users the minimum rights to access the resources necessary to do their jobs?
Answer: B
NEW QUESTION 10
Which type of adversary would commit cybercrimes with the authorization of their country’s government?
Answer: A
NEW QUESTION 11
Match each type of breach to its consequence.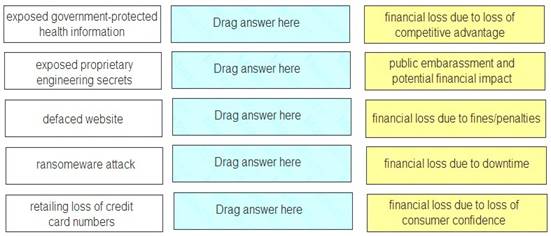
Answer: A
Explanation:
Exposed government-protected health information – financial loss due to fines/penalties Exposed proprietary engineering secrets – financial loss due to loss of competitive advantage Defaced website – public embarrassment and potential financial impact
Ransomware attack – financial loss due to downtime
Retailing loss of credit card numbers – financial loss due to consumer confidence
NEW QUESTION 12
Which type of cloud computing deployment makes resources exclusively available to members of a single organization?
Answer: B
NEW QUESTION 13
What is the function of a hashing protocol?
Answer: D
NEW QUESTION 14
Which network method securely connects two sites across a public network?
Answer: A
NEW QUESTION 15
Which device would an Evil Twin attack use to lure the victim to connect to the attack surface network?
Answer: D
NEW QUESTION 16
Which type of attack floods a target with TCP SYN requests?
Answer: C
NEW QUESTION 17
You discover an infected email attachment that contains software code that attacks a known vulnerability in a popular social networking application. This type of software code belongs to which type of malware category?
Answer: D
NEW QUESTION 18
Which protocol converts voice into a digital signal?
Answer: B
NEW QUESTION 19
Which well-known port is associated with the Simple Mail Transfer Protocol?
Answer: B
NEW QUESTION 20
......
Recommend!! Get the Full PCCSA dumps in VCE and PDF From Surepassexam, Welcome to Download: https://www.surepassexam.com/PCCSA-exam-dumps.html (New 50 Q&As Version)