
Cause all that matters here is passing exam with PT0-001 Dumps. Cause all that you need is a high score of PT0-001 Exam Dumps. The only one thing you need to do is downloading PT0-001 Exam Questions and Answers free now. We will not let you down with our money-back guarantee.
Free demo questions for CompTIA PT0-001 Exam Dumps Below:
NEW QUESTION 1
A penetration tester is utilizing social media to gather information about employees at a company. The tester has created a list of popular words used in employee profile s. For which of the following types of attack would this information be used?
Answer: B
NEW QUESTION 2
A penetration tester successfully explogts a Windows host and dumps the hashes Which of the following hashes can the penetration tester use to perform a pass-the-hash attack?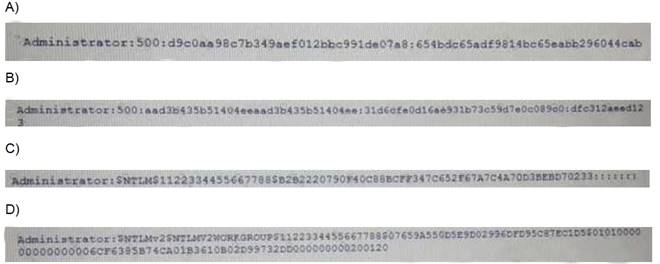
Answer: D
NEW QUESTION 3
A penetration tester has successfully explogted an application vulnerability and wants to remove the command history from the Linux session. Which of the following will accomplish this successfully?
Answer: D
NEW QUESTION 4
DRAG DROP
A manager calls upon a tester to assist with diagnosing an issue within the following Python script:
#!/usr/bin/python
s = "Administrator"
The tester suspects it is an issue with string slicing and manipulation Analyze the following code segment and drag and drop the correct output for each string manipulation to its corresponding code segment Options may be used once or not at all
Answer:
Explanation:
Nsrt
Snma
Trat
Imda
NEW QUESTION 5
Click the exhibit button.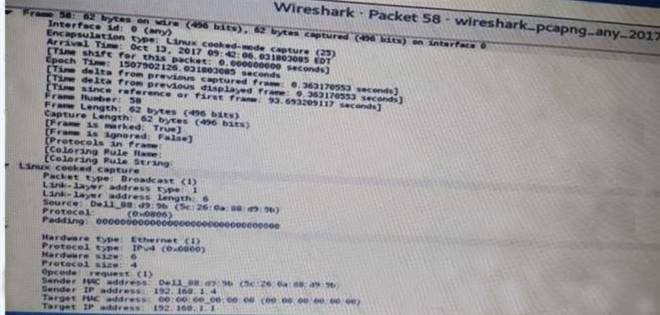
A penetration tester is performing an assessment when the network administrator shows the tester a packet sample that is causing trouble on the network Which of the following types of attacks should the tester stop?
Answer: B
NEW QUESTION 6
A penetration tester wants to target NETBIOS name service. Which of the following is the most likely command to explogt the NETBIOS name service?
Answer: C
NEW QUESTION 7
A penetration tester notices that the X-Frame-Optjons header on a web application is not set. Which of the following would a malicious actor do to explogt this configuration setting?
Answer: B
NEW QUESTION 8
A client asks a penetration tester to add more addresses to a test currently in progress. Which of the following would defined the target list?
Answer: D
NEW QUESTION 9
After several attempts, an attacker was able to gain unauthorized access through a biometric sensor using the attacker's actual fingerprint without explogtation. Which of the following is the MOST likely explanation of what happened?
Answer: A
NEW QUESTION 10
If a security consultant comes across a password hash that resembles the following b117 525b3454 7Oc29ca3dBaeOb556ba8
Which of the following formats is the correct hash type?
Answer: C
NEW QUESTION 11
A penetration tester locates a few unquoted service paths during an engagement. Which of the following can the tester attempt to do with these?
Answer: D
NEW QUESTION 12
A penetration tester successfully explogts a DM2 server that appears to be listening on an outbound port The penetration tester wishes to forward that traffic back to a device Which of the following are the BEST tools to use few this purpose? (Select TWO)
Answer: CD
NEW QUESTION 13
Which of the following types of physical security attacks does a mantrap mitigate-?
Answer: D
NEW QUESTION 14
Given the following script: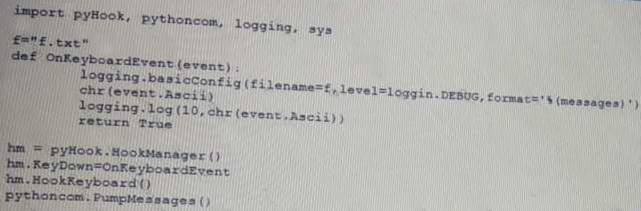
Which of the following BEST describes the purpose of this script?
Answer: C
NEW QUESTION 15
A company planned for and secured the budget to hire a consultant to perform a web application penetration test. Upon discovered vulnerabilities, the company asked the consultant to perform the following tasks:
• Code review
• Updates to firewall setting
Answer: C
NEW QUESTION 16
Which of the following BEST explains why it is important to maintain confidentiality of any identified findings when performing a penetration test?
Answer: C
NEW QUESTION 17
A client has voiced concern about the number of companies being branched by remote attackers, who are looking for trade secrets. Which of following BEST describes the types of adversaries this would identify?
Answer: B
100% Valid and Newest Version PT0-001 Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/PT0-001-exam-dumps.html (New 131 Q&As)