
Your success in CompTIA PT0-002 is our sole target and we develop all our PT0-002 braindumps in a way that facilitates the attainment of this target. Not only is our PT0-002 study material the best you can find, it is also the most detailed and the most updated. PT0-002 Practice Exams for CompTIA PT0-002 are written to the highest standards of technical accuracy.
Online CompTIA PT0-002 free dumps demo Below:
NEW QUESTION 1
A penetration tester recently performed a social-engineering attack in which the tester found an employee of the target company at a local coffee shop and over time built a relationship with the employee. On the employee’s birthday, the tester gave the employee an external hard drive as a gift. Which of the following social-engineering attacks was the tester utilizing?
Answer: C
NEW QUESTION 2
A penetration tester wants to identify CVEs that can be leveraged to gain execution on a Linux server that has an SSHD running. Which of the following would BEST support this task?
Answer: B
NEW QUESTION 3
A company becomes concerned when the security alarms are triggered during a penetration test. Which of the following should the company do NEXT?
Answer: B
NEW QUESTION 4
A company has hired a penetration tester to deploy and set up a rogue access point on the network. Which of the following is the BEST tool to use to accomplish this goal?
Answer: B
NEW QUESTION 5
A penetration tester has obtained a low-privilege shell on a Windows server with a default configuration and now wants to explore the ability to exploit misconfigured service permissions. Which of the following commands would help the tester START this process?
Answer: B
NEW QUESTION 6
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following: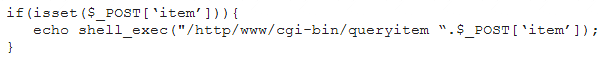
Which of the following tools will help the tester prepare an attack for this scenario?
Answer: C
NEW QUESTION 7
A security engineer identified a new server on the network and wants to scan the host to determine if it is running an approved version of Linux and a patched version of Apache. Which of the following commands will accomplish this task?
Answer: C
NEW QUESTION 8
The following line-numbered Python code snippet is being used in reconnaissance: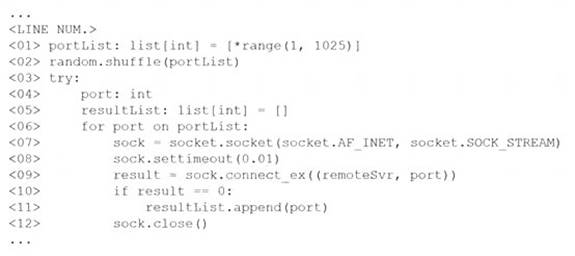
Which of the following line numbers from the script MOST likely contributed to the script triggering a “probable port scan” alert in the organization’s IDS?
Answer: A
NEW QUESTION 9
A company obtained permission for a vulnerability scan from its cloud service provider and now wants to test the security of its hosted data.
Which of the following should the tester verify FIRST to assess this risk?
Answer: A
NEW QUESTION 10
A new security firm is onboarding its first client. The client only allowed testing over the weekend and needed the results Monday morning. However, the assessment team was not able to access the environment as expected until Monday. Which of the following should the security company have acquired BEFORE the start of the assessment?
Answer: B
NEW QUESTION 11
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious. INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.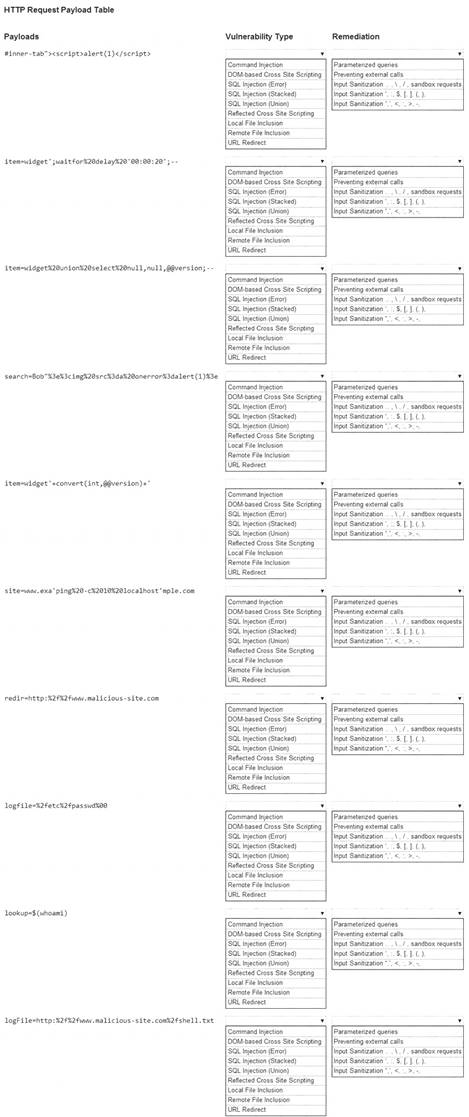
Answer: A
NEW QUESTION 12
A company is concerned that its cloud VM is vulnerable to a cyberattack and proprietary data may be stolen. A penetration tester determines a vulnerability does exist and exploits the vulnerability by adding a fake VM instance to the IaaS component of the client's VM. Which of the following cloud attacks did the penetration tester MOST likely implement?
Answer: A
NEW QUESTION 13
A penetration tester has obtained shell access to a Windows host and wants to run a specially crafted binary for later execution using the wmic.exe process call create function. Which of the following OS or filesystem mechanisms is MOST likely to support this objective?
Answer: D
NEW QUESTION 14
You are a penetration tester reviewing a client’s website through a web browser. INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present. Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.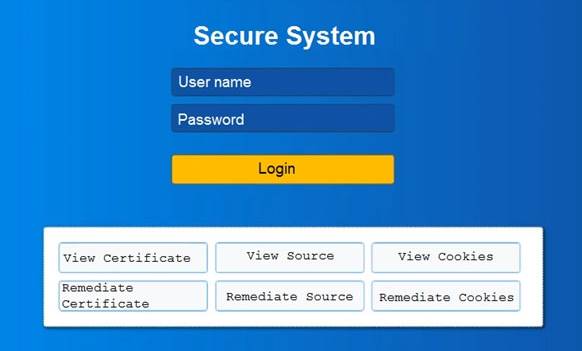
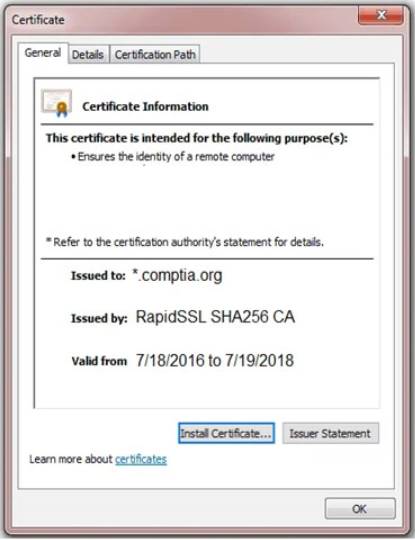
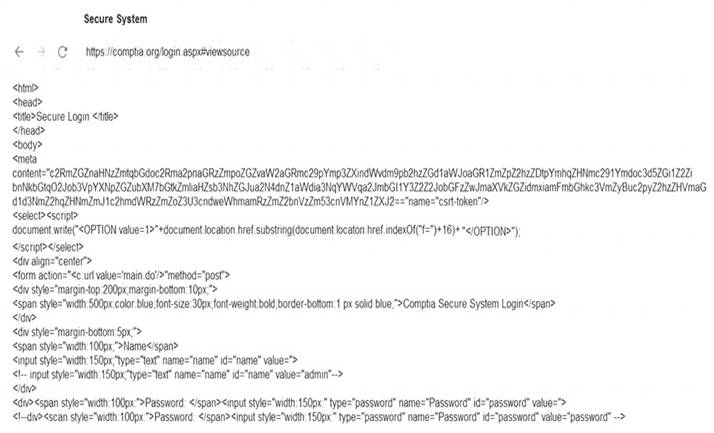
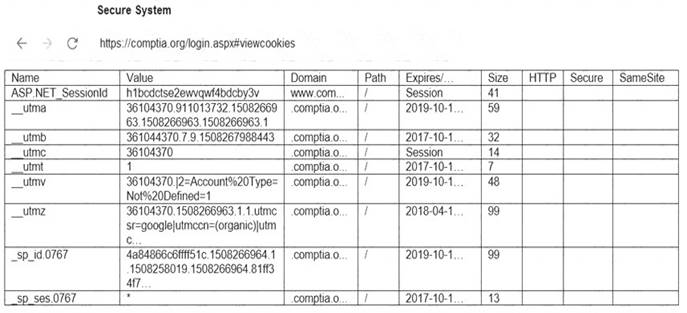
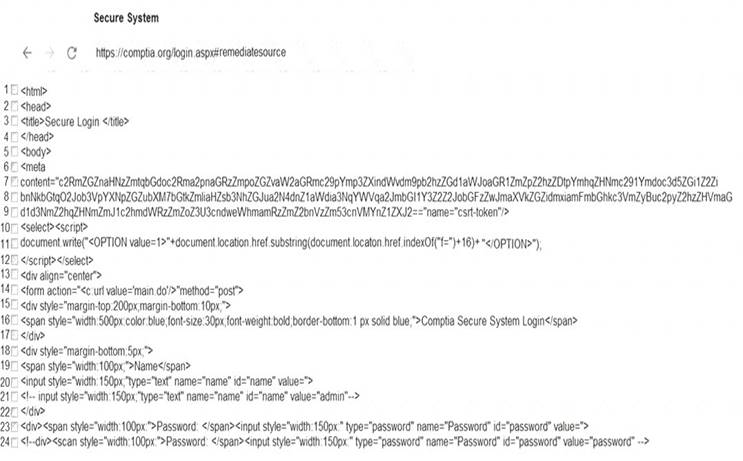
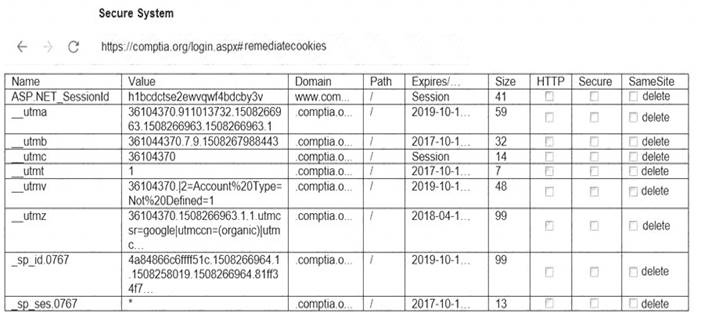
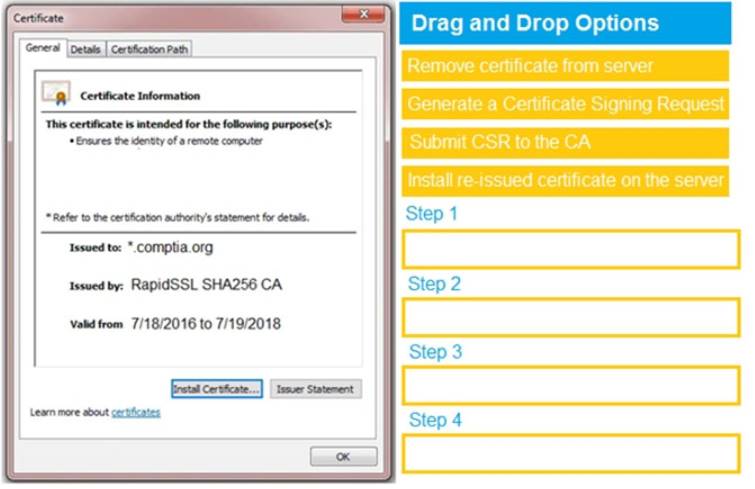
Answer: A
NEW QUESTION 15
Which of the following tools would be MOST useful in collecting vendor and other security-relevant information for IoT devices to support passive reconnaissance?
Answer: B
NEW QUESTION 16
A penetration tester ran a ping –A command during an unknown environment test, and it returned a 128 TTL packet. Which of the following OSs would MOST likely return a packet of this type?
Answer: A
NEW QUESTION 17
......
Recommend!! Get the Full PT0-002 dumps in VCE and PDF From Surepassexam, Welcome to Download: https://www.surepassexam.com/PT0-002-exam-dumps.html (New 110 Q&As Version)