
Exambible offers free demo for SAA-C01 exam. "AWS Certified Solutions Architect - Associate", also known as SAA-C01 exam, is a Amazon-Web-Services Certification. This set of posts, Passing the Amazon-Web-Services SAA-C01 exam, will help you answer those questions. The SAA-C01 Questions & Answers covers all the knowledge points of the real exam. 100% real Amazon-Web-Services SAA-C01 exams and revised by experts!
Also have SAA-C01 free dumps questions for you:
NEW QUESTION 1
Which of the following approaches provides the lowest cost for Amazon Elastic Block Store snapshots while giving you the ability to fully restore data?
Answer: C
Explanation:
http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ebs-deleting-snapshot.html
NEW QUESTION 2
You are setting up security groups for both incoming traffic and outgoing traffic in your VPC network on the AWS CLI. Which of the following AWS CLI commands would you use for adding one or more incoming traffic rules to a security group?
Answer: B
Explanation:
When setting up security groups for incoming traffic in your VPC network, to add one or more ingress (incoming traffic) rules to a security group, authorize-security-group-ingress (AWS CLI). ec2-authorize (Amazon EC2 CLI). Grant-EC2SecurityGroupIngress (AWS Tools for Windows PowerShell) In computer networking, ingress filtering is a technique used to make sure that incoming packets are actually
from the networks that they claim to be from. In computer networking, egress filtering is the practice of monitoring and potentially restricting the flow of information outbound from one network to another. Typically, it is information from a private TCP/IP computer network to the Internet that is controlled.
http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/using-network-security.html
NEW QUESTION 3
How many relational database engines does RDS currently support?
Answer: C
Explanation:
Amazon RDS provides you six familiar database engines to choose from, including Amazon Aurora, Oracle, Microsoft SQL Server, PostgreSQL, MySQL and MariaDB. https://aws.amazon.com/rds/?nc1=h_ls
NEW QUESTION 4
You try to connect via SSH to a newly created Amazon EC2 instance and get one of the following error messages:
"Network error: Connection timed out" or "Error connecting to [instance], reason: -> Connection timed out: connect,"
You have confirmed that the network and security group rules are configured correctly and the instance is passing status checks. What steps should you take to identify the source of the behavior? Choose 2 answers
Answer: AC
NEW QUESTION 5
Which of the following statements is true of tagging an Amazon EC2 resource?
Answer: C
Explanation:
You can assign tags only to resources that already exist. You can't terminate, stop, or delete a resource based solely on its tags; you must specify the resource identifier.
NEW QUESTION 6
Disabling automated backups disables the point-in-time recovery feature.
Answer: A
NEW QUESTION 7
When will you incur costs with an Elastic IP address (EIP)?
Answer: C
Explanation:
You are allowed one EIP to be attached to a running instance at no charge. otherwise, it will incur a small fee. in this case, the instance is stopped, and thus, the EIP will be billed at the normal rate. http://aws.amazon.com/ec2/pricing/
NEW QUESTION 8
Making your snapshot public shares all snapshot data with everyone. Can the snapshots with AWS Marketplace product codes be made public?
Answer: A
Explanation:
"Making your snapshot public shares all snapshot data with everyone; however, snapshots with AWS Marketplace product codes cannot be made public. Encrypted snapshots cannot be shared between
accounts or made public." http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ebs-modifyingsnapshot- permissions.html
"This is not a valid option for encrypted snapshots or snapshots with AWS Marketplace product codes."
NEW QUESTION 9
The _____ IAM policy element describes the specific action or actions that will be allowed or denied.
Answer: B
Explanation:
The Action element describes the specific action or actions that will be allowed or denied. Statements must include either an Action or NotAction element. Each AWS service has its own set of actions that describe tasks that you can perform with that service. http://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements.html
NEW QUESTION 10
A customer has a single 3-TB volume on-premises that is used to hold a large repository of images
and print layout files. This repository is growing at 500 GB a year and must be presented as a single logical volume. The customer is becoming increasingly constrained with their local storage capacity and wants an off-site backup of this data, while maintaining low-latency access to their frequently accessed data. Which AWS Storage Gateway configuration meets the customer requirements?
Answer: A
NEW QUESTION 11
Which of the following is true of Amazon CloudWatch?
Answer: A
Explanation:
Amazon CloudWatch monitors your Amazon Web Services (AWS) resources and the applications you run on AWS in real-time.
You can use CloudWatch to collect and track metrics, which are variables you can measure for your resources and applications. CloudWatch alarms send notifications or automatically make changes to the resources you are monitoring based on rules that you define. For example, you can monitor the CPU usage and disk reads and writes of your Amazon EC2 instances and then use this data to determine whether you should launch additional instances to handle increased load. You can also use this data to stop under-used instances to save money. In addition to monitoring the built-in metrics that come with AWS, you can monitor your own custom metrics.
With CloudWatch, you gain system-wide visibility into resource utilization, application performance, and operational health. http://docs.aws.amazon.com/AmazonCloudWatch/latest/DeveloperGuide/WhatIsCloudWatch.html
NEW QUESTION 12
Which of the following activities is NOT performed by the Auto Scaling policy?
Answer: A
Explanation:
Auto Scaling policies can scale up or down based on the user-defined policies, health status checks or schedules. It also performs a health check on the instances, terminates unhealthy instances, and launches healthy instances to maintain the current instance level. Scaling provides you with options, outside of scaling policies, to override attributes from the instance and use the values that you need. For example, you can override the instance type using AWS CLI commands. http://docs.aws.amazon.com/autoscaling/latest/userguide/create-lc-with-instanceID.html
NEW QUESTION 13
Without _____ , you must either create multiple AWS accounts-each with its own billing and subscriptions to AWS products-or your employees must share the security credentials of a single AWS account.
Answer: D
NEW QUESTION 14
_____ is a fully managed service for real-time processing of streaming data at massive scale.
Answer: B
Explanation:
Amazon Kinesis is a fully managed service for real-time processing of streaming data at massive scale. Amazon Kinesis can collect and process hundreds of terabytes of data per hour from hundreds of thousands of sources, allowing you to easily write applications that process information in realtime from sources such as web site click-streams, marketing and financial information,
manufacturing instrumentation and social media, and operational logs and metering data. http://docs.aws.amazon.com/mobile/sdkforandroid/developerguide/kinesis.html
NEW QUESTION 15
You're trying to delete an SSL certificate from the IAM certificate store, and you're getting the message "Certificate: <certificate-id> is being used by CloudFront." Which of the following statements is probably the reason why you are getting this error?
Answer: A
Explanation:
CloudFront is a web service that speeds up distribution of your static and dynamic web content, for example, .html, .css, .php, and image files, to end users. Every CloudFront web distribution must be associated either with the default CloudFront certificate or with a custom SSL certificate.
Before you can delete an SSL certificate, you need to either rotate SSL certificates (replace the
current custom SSL certificate with another custom SSL certificate) or revert from using a custom SSL certificate to using the default CloudFront certificate.
NEW QUESTION 16
The one-time payment for Reserved Instances is ____ refundable if the reservation is cancelled.
Answer: C
Explanation:
the one-time fee is non-refundable.
https://aws.amazon.com/ec2/purchasing-options/reserved-instances/buyer/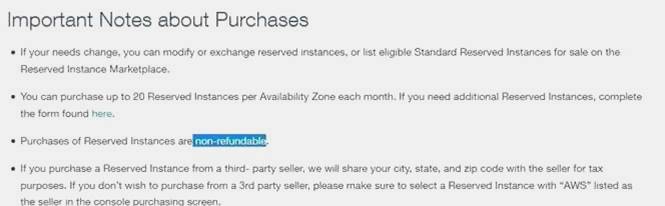
NEW QUESTION 17
In order to optimize performance for a compute cluster that requires low inter-node latency, which of the following feature should you use?
Answer: D
Explanation:
A placement group is a logical grouping of instances within a single Availability Zone. Using placement groups enables applications to participate in a low-latency, 10 Gigabits per second (Gbps) network. http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/placement-groups.html References:
NEW QUESTION 18
By default, EBS volumes that are created and attached to an instance at launch are deleted when that instance is terminated. You can modify this behavior by changing the value of the flag to false when you launch the instance
Answer: A
Explanation:
By default, Amazon EBS root device volumes are automatically deleted when the instance terminates. However, by default, any additional EBS volumes that you attach at launch, or any EBS volumes that you attach to an existing instance persist even after the instance terminates.
This behavior is controlled by the volume’s DeleteOnTermination attribute, which you can modify. http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/terminating-instances.html
NEW QUESTION 19
Amazon RDS DB snapshots and automated backups are stored in
Answer: A
NEW QUESTION 20
When automatic failover occurs, Amazon RDS will emit a DB Instance event to inform you that automatic failover occurred. You can use the ____ to return information about events related to your DB Instance
Answer: C
Explanation:
Q: Will I be alerted when automatic failover occurs?
Yes, Amazon RDS will emit a DB Instance event to inform you that automatic failover occurred. You can use the DescribeEvents to return information about events related to your DB Instance, or click the "DB Events" section of the AWS Management Console
https://aws.amazon.com/rds/faqs/
NEW QUESTION 21
Is Federated Storage Engine currently supported by Amazon RDS for MySQL?
Answer: B
NEW QUESTION 22
What does Amazon ELB stand for?
Answer: D
NEW QUESTION 23
What is a security group in Amazon AWS?
Answer: C
Explanation:
A security group acts as a virtual firewall that controls the traffic for one or more instances. When you launch an instance, you associate one or more security groups with the instance. You add rules to each security group that allow traffic to or from its associated instances. You can modify the rules for a security group at any time; the new rules are automatically applied to all instances that are associated with the security group. When we decide whether to allow traffic to reach an instance, we
evaluate all the rules from all the security groups that are associated with the instance. http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/using-network-security.html
NEW QUESTION 24
AWS IAM permissions can be assigned in two ways:
Answer: B
Explanation:
Permissions can be assigned in two ways: as identity-based or as resource-based. Identity-based, or IAM permissions are attached to an IAM user, group, or role and let you specify what that user, group, or role can do. For example, you can assign permissions to the IAM user named Bob, stating that he has permission to use the Amazon Elastic Compute Cloud (Amazon EC2) RunInstances action and that he has permission to get items from an Amazon DynamoDB table named MyCompany. The user Bob might also be granted access to manage his own IAM security credentials. Identity-based permissions can be managed or inline. Resource-based permissions are attached to a resource. You
can specify resource-based permissions for Amazon S3 buckets, Amazon Glacier vaults, Amazon SNS topics, Amazon SQS queues, and AWS Key Management Service encryption keys. Resource-based permissions let you specify who has access to the resource and what actions they can perform on it. Resource-based policies are inline only, not managed. http://docs.aws.amazon.com/IAM/latest/UserGuide/access_permissions.html
NEW QUESTION 25
An AWS customer is deploying an application mat is composed of an AutoScaling group of EC2 Instances.
The customers’ security policy requires that every outbound connection from these instances to any other service within the customers
Virtual Private Cloud must be authenticated using a unique x 509 certificate that contains the specific instance-id.
In addition, an x 509 certificates must Designed by the customer's Key management service in order to be trusted for authentication.
Which of the following configurations will support these requirements?
Answer: A
Explanation:
http://jayendrapatil.com/tag/iam/
NEW QUESTION 26
......
100% Valid and Newest Version SAA-C01 Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/SAA-C01-exam-dumps.html (New 288 Q&As)