
Your success in Microsoft SC-100 is our sole target and we develop all our SC-100 braindumps in a way that facilitates the attainment of this target. Not only is our SC-100 study material the best you can find, it is also the most detailed and the most updated. SC-100 Practice Exams for Microsoft SC-100 are written to the highest standards of technical accuracy.
Free demo questions for Microsoft SC-100 Exam Dumps Below:
NEW QUESTION 1
You need to recommend a solution to meet the security requirements for the InfraSec group. What should you use to delegate the access?
Answer: D
NEW QUESTION 2
You receive a security alert in Microsoft Defender for Cloud as shown in the exhibit. (Click the Exhibit tab.)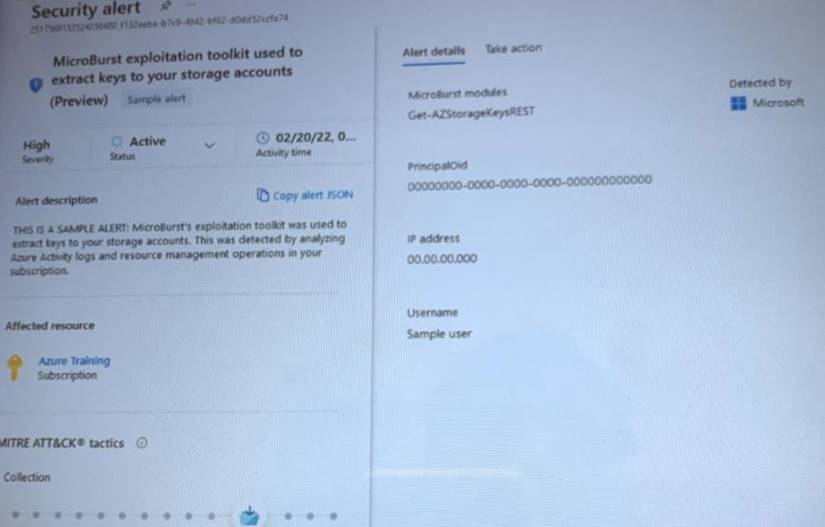
After remediating the threat which policy definition should you assign to prevent the threat from reoccurring?
Answer: A
NEW QUESTION 3
Your company has the virtual machine infrastructure shown in the following table.
The company plans to use Microsoft Azure Backup Server (MABS) to back up the virtual machines to Azure. You need to provide recommendations to increase the resiliency of the backup strategy to mitigate attacks
such as ransomware.
What should you include in the recommendation?
Answer: C
NEW QUESTION 4
Your company is developing a modern application that will run as an Azure App Service web app. You plan to perform threat modeling to identify potential security issues by using the Microsoft Threat Modeling Tool.
Which type of diagram should you create?
Answer: C
NEW QUESTION 5
You are creating the security recommendations for an Azure App Service web app named App1. App1 has the following specifications:
• Users will request access to App1 through the My Apps portal. A human resources manager will approve the requests.
• Users will authenticate by using Azure Active Directory (Azure AD) user accounts. You need to recommend an access security architecture for App1.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.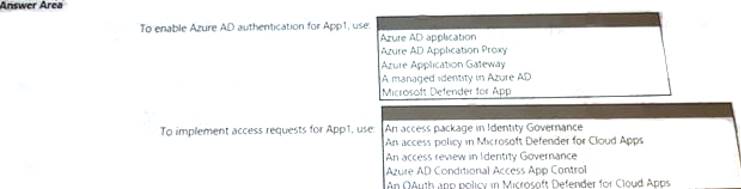
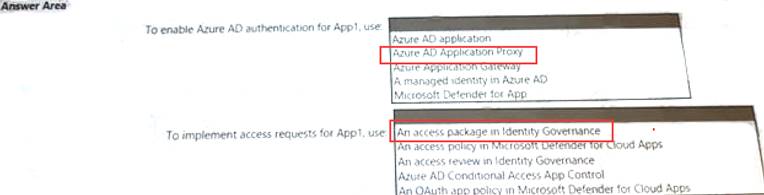
Answer: A
NEW QUESTION 6
You have a hybrid cloud infrastructure.
You plan to deploy the Azure applications shown in the following table.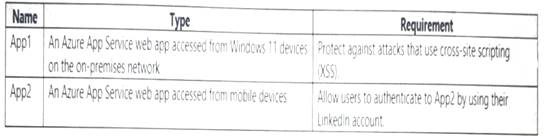
What should you use to meet the requirement of each app? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

Answer: A
NEW QUESTION 7
Your company is migrating data to Azure. The data contains Personally Identifiable Information (Pll). The company plans to use Microsoft Information Protection for the Pll data store in Azure. You need to recommend a solution to discover Pll data at risk in the Azure resources.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.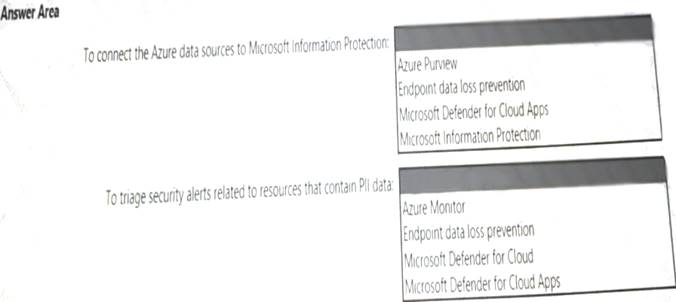
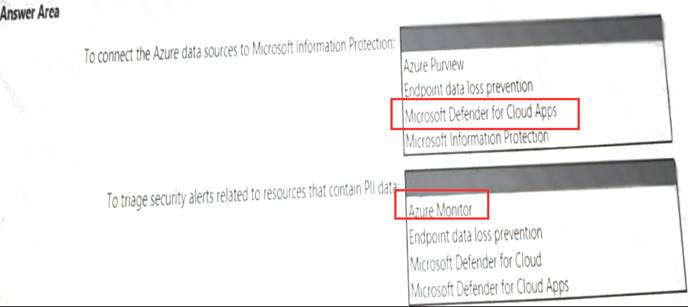
Answer: A
NEW QUESTION 8
You have an Azure subscription that contains several storage accounts. The storage accounts are accessed by legacy applications that are authenticated by using access keys.
You need to recommend a solution to prevent new applications from obtaining the access keys of the storage accounts. The solution must minimize the impact on the legacy applications.
What should you include in the recommendation?
Answer: A
NEW QUESTION 9
Your company finalizes the adoption of Azure and is implementing Microsoft Defender for Cloud. You receive the following recommendations in Defender for Cloud
• Access to storage accounts with firewall and virtual network configurations should be restricted,
• Storage accounts should restrict network access using virtual network rules.
• Storage account should use a private link connection.
• Storage account public access should be disallowed.
You need to recommend a service to mitigate identified risks that relate to the recommendations. What should you recommend?
Answer: A
NEW QUESTION 10
Your company is designing an application architecture for Azure App Service Environment (ASE) web apps as shown in the exhibit. (Click the Exhibit tab.)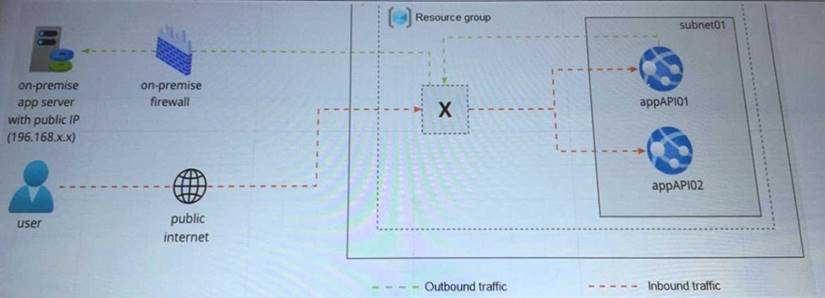
Communication between the on-premises network and Azure uses an ExpressRoute connection.
You need to recommend a solution to ensure that the web apps can communicate with the on-premises application server. The solution must minimize the number of public IP addresses that are allowed to access the on-premises network.
What should you include in the recommendation?
Answer: A
NEW QUESTION 11
You have an Azure subscription that has Microsoft Defender for Cloud enabled. Suspicious authentication activity alerts have been appearing in the Workload protections dashboard.
You need to recommend a solution to evaluate and remediate the alerts by using workflow automation. The solution must minimize development effort. What should you include in the recommendation?
Answer: D
NEW QUESTION 12
You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?
Answer: D
NEW QUESTION 13
You are designing security for an Azure landing zone. Your company identifies the following compliance and privacy requirements:
• Encrypt cardholder data by using encryption keys managed by the company.
• Encrypt insurance claim files by using encryption keys hosted on-premises.
Which two configurations meet the compliance and privacy requirements? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
Answer: CD
NEW QUESTION 14
Your company has a Microsoft 365 E5 subscription.
The company plans to deploy 45 mobile self-service kiosks that will run Windows 10. You need to provide recommendations to secure the kiosks. The solution must meet the following requirements:
• Ensure that only authorized applications can run on the kiosks.
• Regularly harden the kiosks against new threats.
Which two actions should you include in the recommendations? Each correct answer presents part of the
solution. NOTE: Each correct selection is worth one point.
Answer: AB
NEW QUESTION 15
Azure subscription that uses Azure Storage.
The company plans to share specific blobs with vendors. You need to recommend a solution to provide the vendors with secure access to specific blobs without exposing the blobs publicly. The access must be
tme-Vimted. What should you include in the recommendation?
Answer: D
NEW QUESTION 16
Your company has devices that run either Windows 10, Windows 11, or Windows Server. You are in the process of improving the security posture of the devices.
You plan to use security baselines from the Microsoft Security Compliance Toolkit.
What should you recommend using to compare the baselines to the current device configurations?
Answer: D
NEW QUESTION 17
......
P.S. Easily pass SC-100 Exam with 105 Q&As Certleader Dumps & pdf Version, Welcome to Download the Newest Certleader SC-100 Dumps: https://www.certleader.com/SC-100-dumps.html (105 New Questions)